There are various ways for network traffic control. One of the common ways for this job is using Access Contorol Lists. There are three types of access lists. These are;
• Router Access Control Lists( RACLs)
• Port Access Control Lists (PACLs)
• VLAN Access Control Lists (VACLs)
RACL is the most known Access Control List. Generally when ACL abbreviation is used it means RACL. RACL is used to control traffic for layer 3. Port Access Control is used to control the traffic for inbound layer 2. It is only used inbound direction because there is an hardware limitation for outbound direction.The last one, VLAN Access Control List is used to control the traffic within the VLAN.
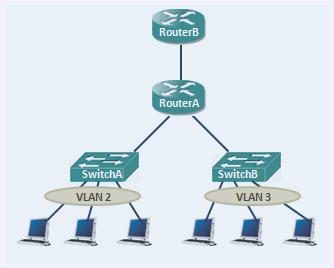
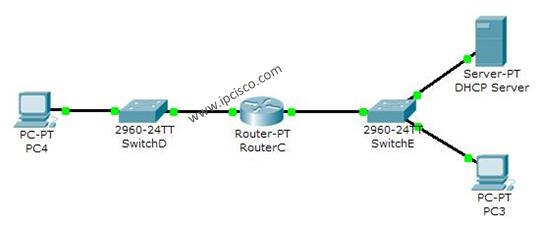
Here to explain all these ACL types the below topology will help us.
Table of Contents
RACLs (Router Access Control Lists)
As mentined before, RACLs are used for controlling layer 3 traffic. These ACLs can be issued for both inbound and outbound direction. Below, the links that RACLs can be implemented is highlighted.
RACL for both direction
RACLs Configuration
Assume that we have a gigabitethernet 1/0/1 port on our router and we will add a RACL to this interface for both inbound and outbound direction. Firstly we must define the RACL and then we will apply the RACL to the interface.
Here is the configuration commands…
To control the configuration and the RACL assignation to the port, use the following show commands:
show ip interface gigabitethernet 1/0/1
show running-config interface gigabitethernet 1/0/1
PACLs (Port Access Control Lists)
In layer layer 2 interfaces PACLs are used instead of RACLs. PACLs are implemented only inbound direction because of the switches’s hardware limitations. Below, the ports that PACLs can be implemented are highlighted.






thanks boss its really help full for learning.