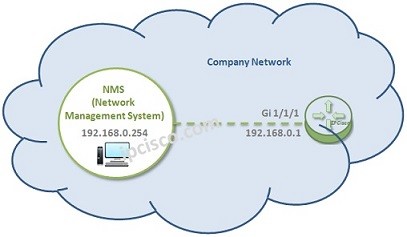
In this Cisco SNMP Configuration Example, we will see how to configure SNMP on Cisco SNMP Agent device. In this part I do not consider necessary what the snmp agent is. You already know that it is the device that we consider to manage with our NMS (Network Management Server).
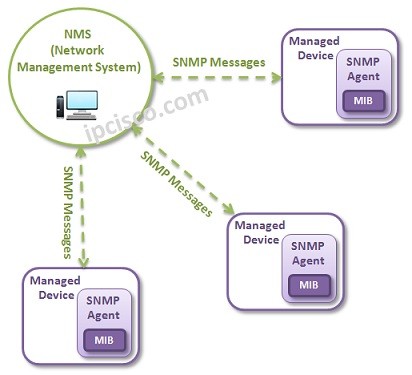
Managing all the network devices are a very difficult. So managing the network devices in one location is very important in network world. This is done with a standard protocol SNMP. With SNMP you can manage your devices with a NMS remotely and in a central point. And the agent device also sends traps,notifications about alarms or exceeding some threshold values determined before for a good managed network.
Table of Contents
SNMP Community Configuration
Like for all the vendor devices, to manage a Cisco devices from a central point we need SNMP. And to use SNMP, for Cisco SNMP Configuration, we need to enable this protocol. Enabling this protocol is done by creating a community strings. Community strings are used for the different access forms in SNMP. You can make the below configuration for different community string definitions.
Router (config)# snmp-server community public ro
Router (config)# snmp-server community ForYou ro
Router (config)# snmp-server community WithYourACL rw 10
Router (config)# snmp-server community HidenOne ro view noRouteTable
Router (config)# access-list 10 permit 192.168.100.1
Above, there are four community strings are defined. The first one can be for eveyone with only read-only access. The second one can be for you only. Here it is important to say that other vendors do not permit more than one read-only community strings.
The third community string above is the read-write one only allowed as the access-list 10. And the last one is the one that can be reached only with a certain user.
SNMP Trap Configuration
On our Cisco SNMP Configuration example, after defining community strings, it is time to configure something for SNMP traps that will inform SNMP Server during any trouble. To do this, use the below configuration commands.
Router (config)# snmp-server enable traps
Router (config)# snmp-server host 192.168.1.1 public
Other SNMP Lessons :
SNMP Overview
SNMP Configuration On Cisco
SNMP Configuration On Juniper
SNMP Configuration On Nokia
SNMP Configuration On Huawei








Leave a Reply