Port Security is the security mechanism used in switches. With this mechanism, a specific port of a switch can be protected with undesirable access. Here, we will learn the theory of this lesson. We will focus on the properties of this mechanism and some of the Cisco configuration commands. For example configuration, you can view Cisco Port Security Configuration and Huawei Configuration with eNSP. You can also check Cisco website for this configuration, here.
The MAC address numbers connected to a port or the specific MAC addresses can be configured on a swithport with this technology. By doing this configuration, desired numbered of devices can connect to the switch over one port. And also a specific MAC addressed device can be allowed to access this port.
The number of desired device number is mentioned. After that the MAC address of this devices configured either statically or dynamically (sticky). If a manual MAC address is configured, then a device with this MAC address is waited and allowed to access. If there is no manual configuration, then dynamic (sticky) MAC adress learning is configured. And the first connected devices’s MAC address are registered up to the configured max accepted device value.
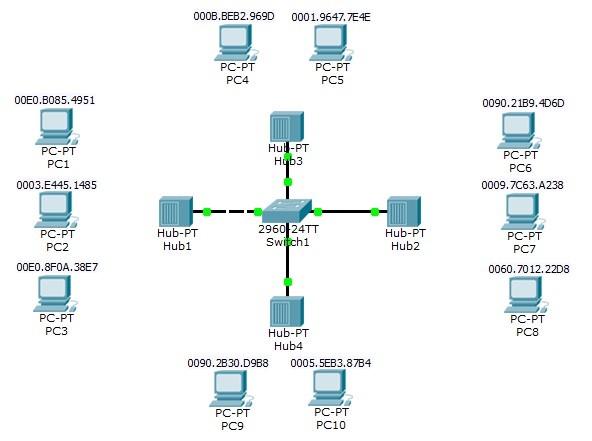
You can see the below shape as a little referance for Port Security. In this topology in switch maximum 2 allowed MAC is configured.And the allowed MAC adresses are mentined statically. So, the Host A and Host C is allowed, but Host be is not allowed for this port.

On Cisco Catalyst Switches to enable this security functionality, we use the below command as below:
Switch(config)# interface fastEthernet 0/1
On Cisco switches, to determine the Maximum Number of allowed MAC addresses are can be set with the below command. For example, if we would like to limit these MAC addresses as maximum 10, we will use he below command:
Switch(config-if)# switchport port-security maximum 10
MAC addresses can be learned Dynamically and Statically. For Static MAC learning we can use the below command with MAC address.
Switch(config-if)# switchport port-security mac-address AAAA.BBBB.CCCC
Tjhis configuration can be done also with a specific VLAN as below:
Switch(config-if)# switchport port-security mac-address AAAA.BBBB.CCCC vlan 10







Leave a Reply