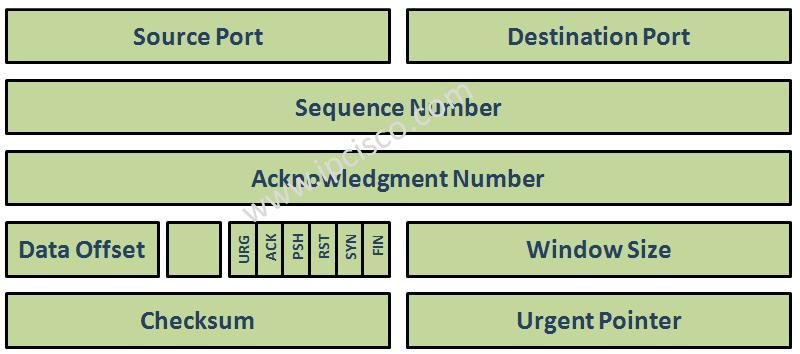
Each TCP segment has a special purpose and this is determined by flags.Here we will study on 6 important control flags. There are also other options in flag field, but we will focus only 6 of them. You can check these flags below.
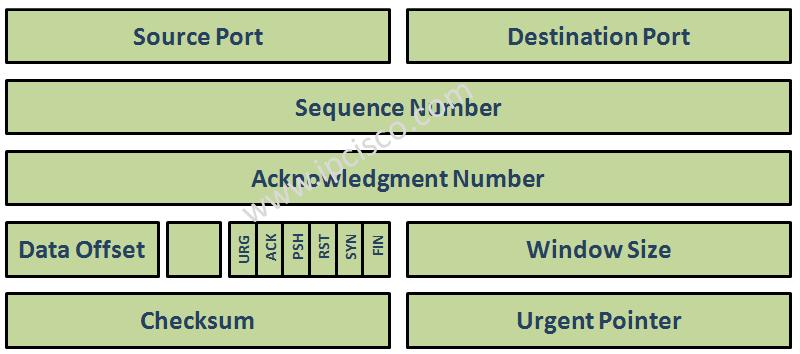
Table of Contents
1st Flag – Urgent Pointer
Urgent Pointer flag is used to say that this packet must have a priority. Normally packets goes to the queues on the receiving end. But a packet with urgent pointer flag is set, do not goes to the queue, it goes immediately to the receiver.
Additionaly there is an urgent pointer field in tcp header that we will discuss later. When the urgent pointer set to 1, then te urgent pointer field specifies the position of the urgent data in the segment.
2st Flag – Acknowledgement
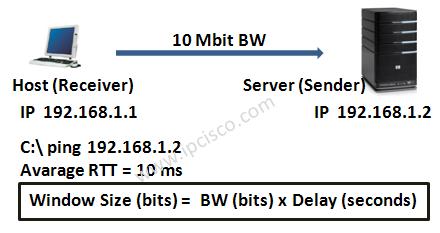
ACK flag is used to acknowledge the sending end that the packet has successfully come. For every packet received by the remote end, remote end send a packet with ACK field set to 1. But with windowing, this is done like one ACK for every 3 received packet.







Leave a Reply