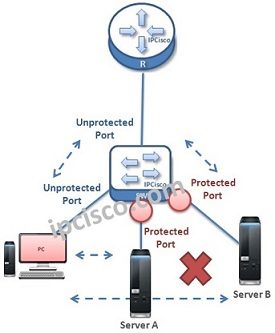
Protected Ports are one of the security mechanisms used on switch world. By default all the switch ports are unprotected and equal. But with Protected Port Configuration, some ports are filtered an restricted to access each other.
If you configure a port as protected, data traffic on Layer 2 is not transfered to other protected ports on this broadcast domain ( or switch stack). Only control traffic is sent to these ports. To provide data traffic between these ports a layer 3 device is required. But if you use protected ports, you do not need this.
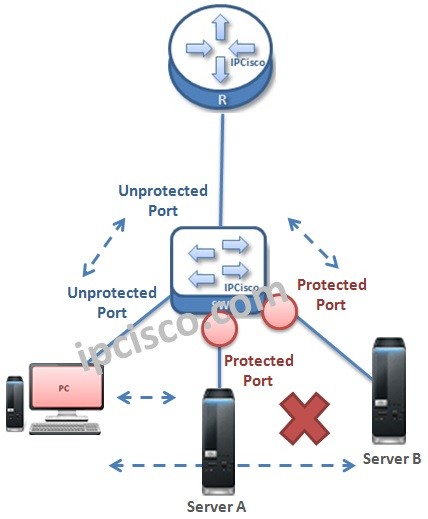
Simply we can say that Protected Ports do not send and receive traffic each other. But, they can send and receive traffic withother ports.
Think about the above topology. Here, when we configure the server ports on the switch as “Protected Port”, these port can not send /receive data traffic between themselves. They can only send data traffic to unprotected ports and receive data traffic from them too. As you see, the unconfigured ports are unprotected by default.
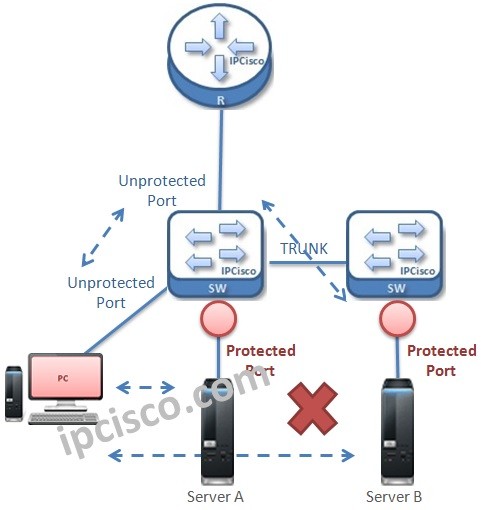
Protected Ports can be used on one switch or on multiple switches that represents a single switch logically. Protected ports on the same switch or in different switch but in the same broadcast domain can not send/receive data traffic each other.
Below, there is an example topology that has two switch that has only one broadcast domain. In this topology, configured protected ports are in different switches. Althought this, they behave like on the same switch and protected ports are restricted to send and receive data traffic eachother. Server B can reach the PC, because it is connected to unprohibited port.
By using Protected Ports, attacks or other harmfull behaviours are restricted on specific ports. This is not only for atack like behaviours. If you do not want some ports not to communicate, you can use Protected Ports.
VLAN Related Articles…
VLAN – Part 1
VLAN – Part 2 (VLAN Assignments and VLAN Port Types)
VLAN – Part 3 (VLAN Frame Tagging Protocols, ISL and Dot1.q)
VLAN – Part 4 (How to Configure Cisco VLANs)
VLAN – Part 5 (Packet Tracer VLAN Configuration Example)
VLAN Configuration on Huawei Switches






Leave a Reply