Ransomware Attack is one of the most used cyber security attacks today. It is mainly an attack against user data. In this lesson, we will learn what is ransomware attack, how ransomware attack works and how to prevent ransomware attack. We will also learn popular ransomware attack variants done by different types of hackers.
Let’s start with what is Ransomware Attack?
Table of Contents
What is Ransomware Attack?
Ransomware Attack is mainly a malware which used to block user access to its own data or computer. In this type attack, attacker encrypts user files and he/she wants a ransom payment to decrypt it. Without a key, user cannot decrypt this encrypted data and user cannot use his/her own data or computer.
Today, these types of attacks effect many organizations. The effected organization can be a hospital, a financial organization or a company corporate network which has critical information.
The modern ransomware attacks began at 2017 with WannaCry outbreak. After that different ransomware variants have been developed.
At 2020, ransomware attacks have increased more than %50 because of COVID-10 pandemic period. In this period, remote works increased and as a result, company networks’ exploits are detected by attackers. This resulted more ransomware towards company networks.
How Ransomware Attack Works?
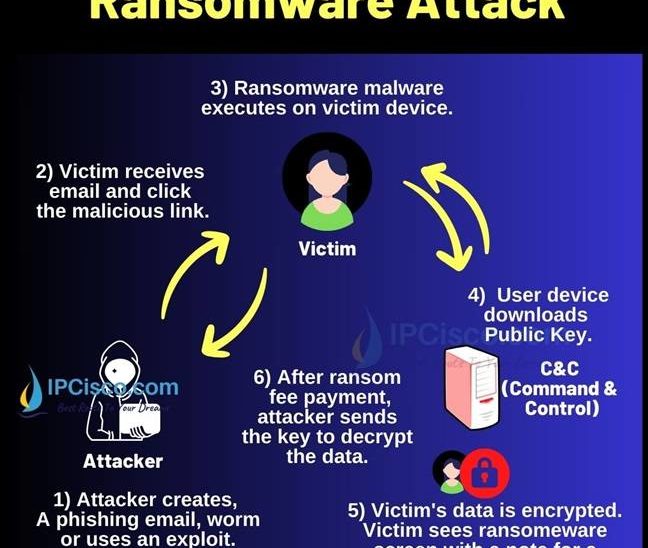
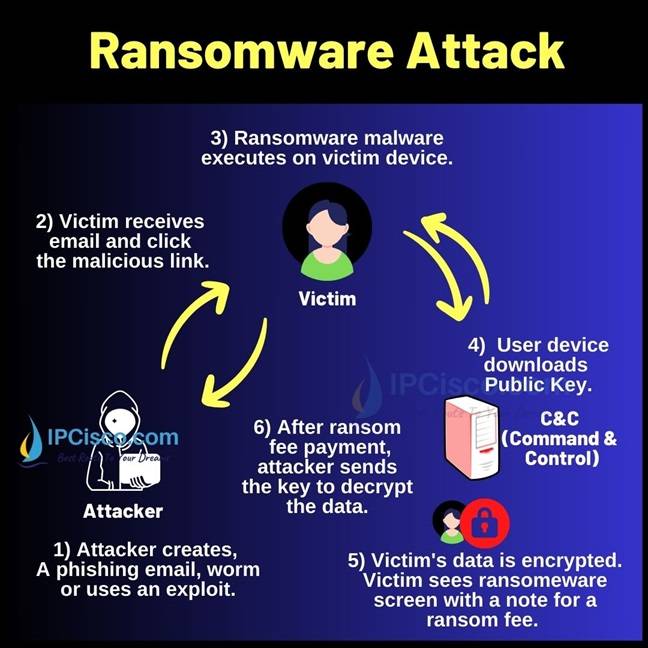
We have learned what is Ransomware attacks. Now, let ‘s focus on how ransomware attack works? There are different variant of these attacks and each one uses different methods. But there are some common steps in such attacks. These common ransomware steps are:
- Infection Step
- Data Encryption Step
- Ransom Demand Step
Below, you can find the details of these steps. After that we wil also focus on how to prevent ransomware attacks.
Infection Step
In the first step, attackers must access the victims’ system. This is infection step. In infection step, attacker can use various ways to access the victim data.
Attacker can use a phishing email which includes download links inside. When user download this malicious ransomware program, it is executed on user’s computer.
Attacker can also guess or steal user credentials to access user data by using Remote Desktop Protocol (RDP). This way is especially used towards remote workers. With this way, attacker enters corporate network and user computer. Here, he/she downloads and executes the malicious ransomware software.
Data Encryption Step
After accessing the user system, ransomware attacker encrypts user file and these files are only accessible with a key. If user want to access his/her files again, he/she need to get this key from the attacker.
In some strict variants of ransomware attacks, backup files and copies are also deleted to force the user for ransom payment.
Ransom Demand Step
The last step of ransomware attacks is ransom demand step. In this step, ransom fee demand message is showed by changing the background of the computer or by adding a note to the folders.
Ransomware Variants
There are many ransomware variants but some of them are more popular than others. Because, these attack variants are more successful than the others. Below, you can find some of these popular ransomware variants according to a well-known security vendor Check Point.
- Ryuk
- Maze
- Revil
- Lockbit
- DearCry
- Lapsus$
Ryuk
Ryuk ransomware is one of the most used variants of these attacks. With Ryuk attack, attacker sends a phishing email or uses compromised user credentials to get the control of user data. Then attacker encrypts the user data and puts a ransom wish message to the user.
This attack is an expensive attack because it demands average more than 1.000.000$ from the victims. So, the victims of this type of attack are especially large organizations whose data is very valuable for their functionality.
Maze
Maze ransomware attack is the first attack which uses both data encryption and data theft. In this type of attack, attackers wish a ransom fee again. But this time if victim do not send this payment, they sell or distribute this data to public.
Although this variant of ransomware attack is officially ended by the developed group, it is used with different variants today.
Revil
Another ransomware attack is the most known one on internet. It is Revil ransomware. It is also known as Sodinokibi. This attack is operated by a Russian group. In this attack, again, both data steal and data encryption are used.
Revil is also an expensive attack which demands 800.000$ from the victims. Because of both using data encryption and data theft, in this variant, sometimes a second ransom fee is demanded by the attackers.
Lockbit
Lockbit ransomware is the other variant. In this type of malware, user data is encrypted. And this malware works as a Ransomware-as-a-Service (RaaS). Lockbit target large organizations and encrypt their data rapidly. After that it wishes a ransom fee to decrypt the data.
DearCry
DearCry is the ransomware variant which targets four Microsoft Exchange vulnerabilities. By using these vulnerabilities, DearCry encrypts user data and wish ransom fee to decrypt it.
Lapsus$
Lapsus$ is another dangerous ransomware attack variant. The origin of this attack is South America. In this type of attack, user information both encrypted and theft again. If victim do not pay ransom fee, the critical user information is released.
How to Prevent Ransomware Attacks?
We have learned what is ransomware attack, how it works and the variants of this malicious attacks. Now it is time to learn how to prevent ransomware attacks?
Cyber Security Awareness Training
Trainings For Cyber Security Awareness is one of the most important prevention methods towards ransomware attacks. Because attackers enter user system by phishing emails or by stealing credentials. If a user is educated for such threads, user will be aware of the style of phishing emails and he/she can prevent his credentials better towards any malicious behaviors.
Data Backups
Continuous data backups are very important to recover from such attacks without paying any ransom fee. Because if you have your data backups, you can overcome this malicious attack with your own data. You do not need any encryption key to recover them.
Updates and Patching
Different vulnerabilities can occur I different software. By patching with the latest patches reqularly, you can overcome these vulnerabilities. In a well defended system, all the software must be updated with the latest patches.
Strong and Safe Credentials
One of the ways of ransomware attacks is stealing or guessing user credentials. To overcome this, strong credentials must be used by the users. Because strong passwords are difficult to guess by the attacker. Beside user must store its credentials in a safe place. Users can also use manual encryption for their passwords.
Last Word
We have learned what is ransomware attack, how ransomware attack works, what is the variants of this thread. We have also learned how to prevent ransomware attack. To prevent your system towards such an attacks, you can be aware of these techniques.












Leave a Reply