A Hacker is a highly skilled person on Cyber Security, Computer Systems and Networks. In other words, they are the Master of Computer World. With such an expertise, a Hacker can do many things on different computers and networks. So, here the important point is the Types of Hackers. Because there are many Hacker Types in tech World. If a Hacker select a legal way then he/she uses his/her expertise for good. If not, then he/she can achieve illegal bad activities.
The activities of an hacker can be harmful or useful. Because thy know networking, linux administration, programming very well. If a Hacker tries to steal any private data, Money etc., this type of hacker activities are illegal and bad activites. But, if he/she uses this expertise for securing any systems towards other hackers, then this activity is legal and every critical organization need such a person in their network.
So what are the Types of Hackers? Which Hackers are legal and which ones are not? Let’s talk about each of these Hacker Types and learn their aims, behaviours and motivations.

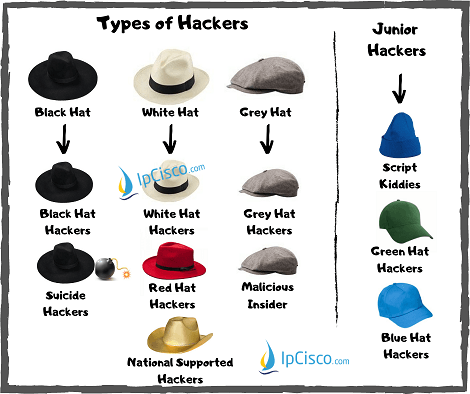
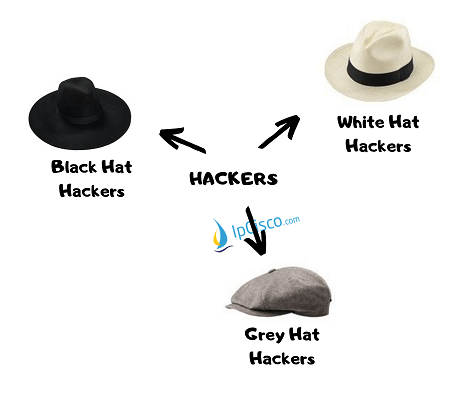
Mainly, we will devide Hackers into three. This is according to their harmful or useful parts. These main types of Hackers are:
- Black Hat Hackers
- White Hat Hackers
- Grey Hat Hackers
These main has sub types under it. These are given also below:
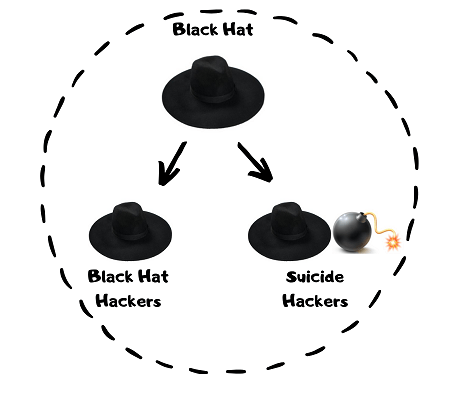
Black Hat :
- Classic Black Hat Hackers
- Suicide Hackers
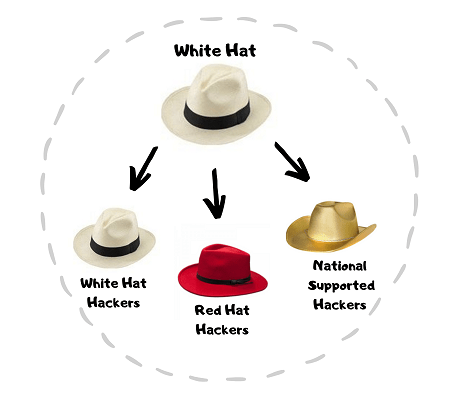
White Hat :
- Classic White Hat Hackers
- Red Hat Hackers
- State/Nation Sponsored Hackers
Grey Hat :
- Classic Grey Hat Hackers
- Malicious Insider or Whistleblower
Beside these Hacker types, there is also another definitions for a different Hacker Group. This type is not in any other main groups but they can be acccording to the affect.
- Hactivist
There are also Expert Hacker candidates, Junior Hackers. These Junior Hacker Types are:
- Script Kiddies
- Green Hat Hackers
- Blue Hat Hackers
Lastly, there is a Purple Hat Hackers and Social Media Hackers. We will discuss all of these types one by one detailly.
Table of Contents
Types of Hackers: Black Hat
There are two categories under Black Hat Hacking. These are “Classic Black Hat Hackers” and “Suicide Hackers”.You can find the details of the Bad Boys of cyber world below.
Black Hat Hackers
Motivation : Personal Gain; Money, Data
Actions : Steal, Destroy, Manuplate
Behaviour : Illegal
Black Hat Hackers are the most dangerous Hacker types. Their main motivation is using their knowledge to gain critical private data, steal money from bank accounts etc.
This type of Hackers can create viruses, malwares and other harmful programs and with these programs, they detect the vulnerabilities of the systems. After entering the system, theycan learn important business, personal or financial private data. According to this knowledge, they can reach many private networks, many computers. They can destroy the systems and manuplate compputer system’s behaviour.
Think about it, if an Hacker accesses to your bank account, he/she can transfer all the Money to his/her account. Or, if he/she gain access to the government’s system, he/she can learn many critical information and use this information.
As a summary, Black Hat Hackers, are the ones who are behind of many critical cyber crimes. They work in the dark part o the web.
Suicide Hacker
Motivation : Money, Revenge
Actions : Steal Critical Data
Behaviour : Illegal
Malicious Insider or Whistleblower is the
Suicide Hackers are the ones who knows that they will caught by the cyber teams.Although knowing this, he/she acts and hacks the systems. This is like suicide bombers. The main motivation of this group is high Money offer or a big revenge from thier enemies.
Types of Hackers : White Hat
There are three categories under White Hat Hacking. These are “Classic White Hat Hackers” , “Red Hat Hackers” and “State/Nation Sponsored Hackers”. The details about of the Guards of cyber security below.
White Hat Hackers
Motivation : Provide Security
Actions : Cyber Security Activities
Behaviour : Legal
White Hat Hackers are the golden guys in computer World. The other name of White Hat Hackers are Ethical Hachers. They are the heros of government and many organization who need cyber security.
White Hat Hackers are the computer system experts who has an excellent knowledge like Black Hat Hackers. The key difference is, one side is trying to enter and steal like a thief. The other side is waiting in front of the door like a guard.
During the integation and operaiton, systems can have many backholes. Ethical Hackers detect this with many tools and penetration tests. After that they cloeses this backdoors which are the entrance of the malicious hackers. They also use antivirus and antimalware programs towards any viruses, malwares, trojans etc.
As a summary, White Hat Hackers, are the guard of computer systems and networks. They are the heros for organizations.
Red Hat Hackers
Motivation : Revenge
Actions : Cyber Security Activities and Attack back
Behaviour : Legal aggressive
Red Hat Hackers are the White Hat Hackers who behave like them with a little difference. A Red Hat Hacker do not defence only. He/She also attack backs to the hacker. Here, the main aim is not only detect the vulnerabilities and defend towards the hackers, but also defeating the hacker.
As a summary, Red Hat Hackers are good bu a little aggressive guys. They would like to defeit the evil in its house. Who knows, maybe the best defence is offence sometimes.
State/Nation Sponsored Hackers
Motivation : Government Cyber Security
Actions : Cyber Security Activities
Behaviour : Legal
State/Nation Sponsored Hackers are the White Hat Hackers who defend the national systems as a cyber security team. They are the guards at the door of govenment systems. With advanced tools they proide the security of systems and networks towards any Black Hat Hacking coimng from any organisations, hacker or other national governments. They defend the country, so they are highly paid Hackers.
As a summary, State/Nation Sponsored Hackers are hackers sponsored by governments. They defend critical govenment systems from internal and external attacks.
Types of Hackers : Grey Hat
There are two categories under Grey Hat Hacking. These are “Classic Grey Hat Hackers” and “Malicious Insider or Whistleblower”.
Grey Hat Hackers
Motivation : Data Gain
Actions : Steal Critical Data
Behaviour : Illegal
Grey Hat Hackers are the Hachers who are between Black Hat Hackers and White Hat Hackers. They are not Black because they do not use their knowledge for a personal gain. But they are also not White, because reaching critical data without any permission is not legal.
This type of Hackers can not work legally in an organization. But at the backplane, they are working. Grey Hat Hackers are the most crowded Hacker group on Internet.
As a summary, Grey Hat Hackers are data hunters. They are dangerous especially for the organizasions that has critical data.
Malicious Insider or Whistleblower
Motivation : Commercial Data Gain
Actions : Steal Critical Data
Behaviour : Illegal
Malicious Insider or Whistleblower is the hacker group who serve to an organization to get information about their rivals. This type of hacker is also a Grey Hat Hacker that can reach critical data illegally. They can use many hacking tools to access any rival company servers and learn critical data for his/her company.
As a summary, Malicious Insider or Whistleblower is the Grey Hat Hacker used by some organizations againts their rivals. They are harmful for their rivals.
Junior Hackers
There are three categories under Junior Hacking World. These are “Script Kiddies”, “Green Hat Hackers” and “Blue Hat Hackers”. The details about these beginners of the Hacker World are below.
Script Kiddies
Motivation : Gain Attention
Actions : Simple attacks
Behaviour : Illegal
Script Kiddies are the junior Hacker type. They use different Hacking tools,programs and codes. The main aim of a Script Kiddy is gain attention towards others. With their actions they can do some cyber security attacts. These attacks can ve DOS and DDOS attacks.
Script Kiddies has limited knowledge in Hacking and they are also not the ones who are very curious on this are. They are not eager to become a Master of Computer World, they are not like Green Hat Hackers. Their behavious is a little interest as their name’s implies.
As a summary, Script Kiddies are not as dangerous as Black Hat Hackers. But with strong progams they can impact your system during gaining attecntion towads his/her friends.
Green Hat Hackers
Motivation : Become an Experienced Hacker
Actions : Simple attacks
Behaviour : Who knows?
Green Hat Hackers are another junior hacker type. They know hacking programs, codes and they are eager to learn more. Their main aim is to become an expert Hacker. According to their eager, they can be an experienced hackers in the future. But we do not know, where will thay stay. At the White Part or At the Dark Part.
As a Summary, Green Hat Hackers are eager junior Hackers. Their main aim can not be rate a harmful attack but sometimes the most dangerous atatcks can be caused from a curious user.
Blue Hat Hackers
Motivation : Revenge
Actions : Simple attacks
Behaviour : Illegal
Blue Hat Hackers are the angry junior hacker type. They are like Script Kiddies and Green Hat Hackers but with a strict difference. They are learning for revenge towards any one or any organizasion. To become an expert Hacker is not a main motivation of this types of hackers.
As a summary, Blue Hat Hackers are angry junior Hacker type. So, being be careful towards these guys can be better.
Other Hacker Types
Hactivist
Motivation : Government Cyber Security
Actions : Cyber Security Activities
Behaviour : Illegal
Hactivists are the Hackers who acts to gain attention for any religion, social and political issue. They attacks and gain access to the systems and locate their message. The main aim of these type of Hackers are being seen my many people.
As a summary Hactivists are not too much harmful, their attacks are not too strict but at the end of the day they can affect your system with a style that you do not want.
Social Media Hacker
Motivation : Data Gain, Revenge
Actions : Steal Social Media Accounts
Behaviour : Illegal
Social Media Hacker is the one who steals social media accounts. This can be done for revenge or gain any information about someone.
Purple Hat Hacker
Motivation : Always to be better
Actions : Test own vulnerabilities and attacking capabilities
Behaviour : Legal
Purple Hat Hacker is a Hacker who tests himself/herself on their own PCs. They can buy a PC or they can use an old PC to hack thier another PC to see that how they are good at cyber security and hacking. This is really a very good cyber security practice for anyone.
Last Word About Hackers
As a Summary, there are many and different types of Hackers in the World. According to their motication, actions and behavior, they select a side. Black or White, Good or bad, Legal or Illegal and being a Hero or a Bad Guy.
As an experienced Network Expert, I offer to the junior experts to select always the good way. Kindly, do not use your excellent expertise for illegal activities and to be harmful for other people. If you go through your expertise, your dreams will be real one day. Because, at the end of the day always the Goods win!











Leave a Reply