Table of Contents
Packet Tracer Extended Access Lists Configuration
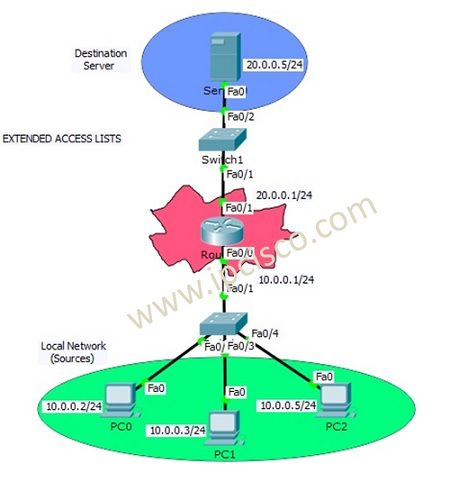
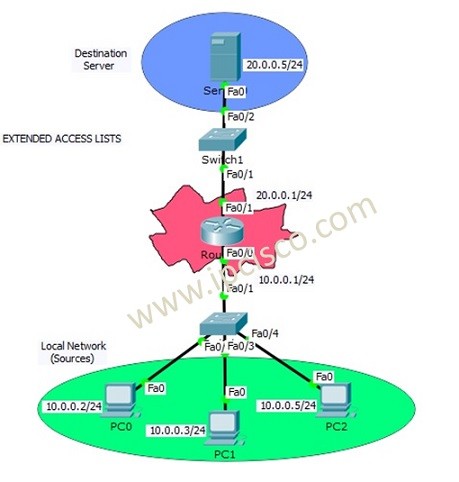
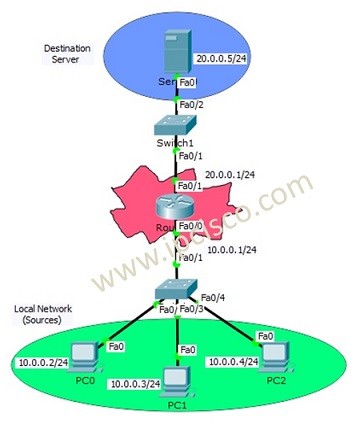
We have learned Access Control Lists overview and Standard ACL Configuration at the previous lessons. In this lesson we will focus on Cisco Extended ACL Configuration with Cisco Packet Tracer. We will use the below topology for our packet tracer configuration.
You can DOWNLOAD the Cisco Packet Tracer example with .pkt format at the End of This Lesson.
Like Standard ACL Configuration Example, we will use one router, one destination server and 3 PCS in common. The switches in the topology will onlu used for port need.
Extended ACLs are a little complex if we compare with Standard ACLs. With Extended ACLs, we can restrict or allow specific things like destination, protocol or port.
In this Cisco Extended ACL Configuration example, we will allow/deny ICMP protocol through the server. As you know, ICMP is ping protocol. Here, PC0 and PC1 will be allowed and PC2 will be denied.
You can also learn DHCP Server Configuration With Packet Tracer
Extended Access-List Configuration
Let’s start to configure router for our Cisco Extended ACL Configuration.
For Extended ACLs, we can use Extended Access-List Number range 100 to 199. Here, we will use 100.
Router # configure terminal
Router (config)# ip access-list extended 100
Router (config-ext-nacl)# permit icmp 10.0.0.0 0.0.0.3 host 20.0.0.5
Router (config-ext-nacl)# deny icmp host 10.0.0.5 host 20.0.0.5 host-unreachable
Router (config-ext-nacl)# end
Router # copy run start
You can also DOWNLOAD all the Packet Tracer examples with .pkt format in Packet Tracer Labs section.







Thanks so much Gokhan.
This topic has been a problem to me and I have really liked this tutorial.
God bless you as you prepare more tutorials.