- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
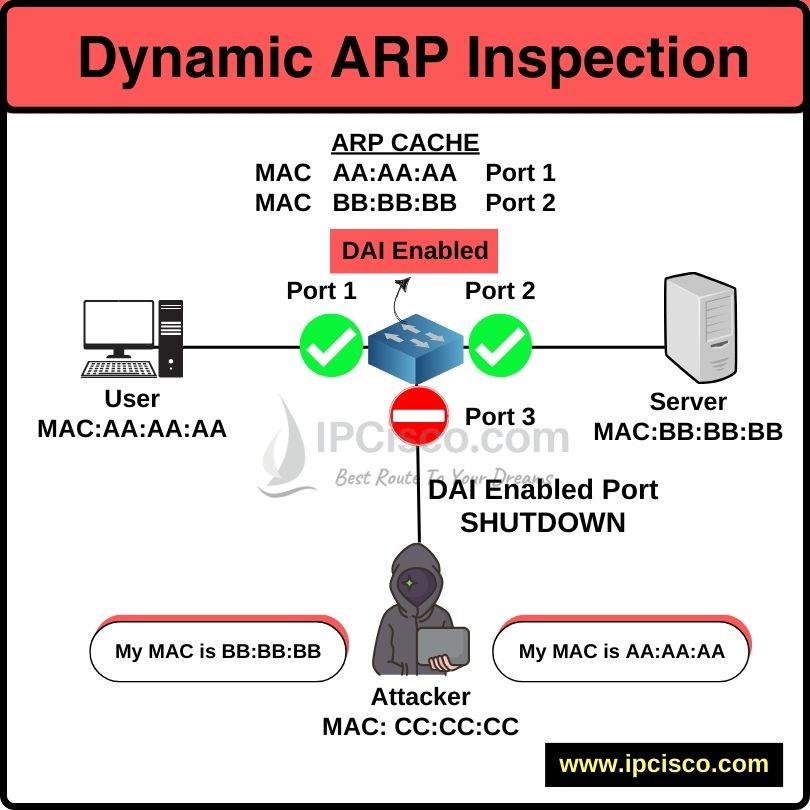
Dynamic ARP Inspection (DAI) is one of the security mechanisms used against ARP spoofing attacks. In this lesson, we will focus on Dynamic ARP Inspection Juniper configuration and we will learn how to configure Dynamic ARP Inspection on Juniper Routers. DAI is basically a security mechanism utilize DHCP Snooping database towards malicious ARP attacks. Let’s learn more on this mechanism.
By the way, this lesson is important for Juniper Certifications, JNCIS-ENT and JNCIE-ENT.
Table of Contents
In Ethernet networks, ARP (Address Resolution Protocol) is used for MAC-IP matchings. After the first transmission of a packet, ip address and MAC address of the sender is recorded to an ARP Cache. After that, when ever a device need to send a packet, it checks this cache. If it finds an entry about the destination, it sends the packet to that destination. If it does not find any entry, then it sned the packet as broadcast.
ARP is vulnerable to some network attacks. One of them is ARP Spoofing Attack. What is an ARP spoofing attack? ARP spoofing attack is a Man-in-the-middle attack with which, attacker resides between two system and poisons their ARP Cache to direct the traffic for malicious aims. Here, attacker simply changes IP-MAC matchings in ARP Cache and tricks both end with new wrong entries. When ever the victim sends a packet, he/she thinks that, the packet is going to the exact destination. But, the packet is going to the attacker at this time.
With Dynamic ARP Inspection mechanism, we validate ARP packets in the network. By doing this, we prevent our network against and malicious ARP attacks like ARP spoofing. Here, ARP packet validation is done with the help of DHCP Snooping Database. It checks DHCP Snooping database if are there any entry about this ARP packet. If it finds any record, it accept the packet. If it des not find eny entry about it, DAI drops the packet.

Dynamic ARP Inspection Protection
In Juniper devices, we can configure DAI easily with a few steps. Here, we will focus on these steps one by one. Before this configuration, let’s explain some key points about Juniper DAI configurations.
On Juniper EX Series switches and QFX Series, Dynamic ARP Inspection is used on Access Ports. Because on access ports, all the ports are untrusted by default. Here, trunk portsa re bypassed, because, trunk portsa re trusted by default.
On Juniper devices, we configure DAI for each VLAN, not for each interface. By default, DAI is disabled on VLANs. If you would like to use this security mechanism, you should configure DAI for each VLAN.
As a keynote, in Juniper devices, if you set an interface as DHCP trusted, it is also trusted for ARP packets. You do not need to configure it as trusted again.
To enable DAI on a VLAN in a Juniper device, we shoould go under vlan configuration. Certainly, before this configuration, we should do our VLAN configuration. Here, under “vlans vlan-name forwarding-options”, we will g oto “dhcp-security” and under it we will use “set arp-inspection” command.
[edit vlans vlan-name forwarding-options dhcp-security]
ipcisco@switch# set arp-inspection
vlans vlan-name forwarding-options{
dhcp-security {
arp-inspection;
…
On Juniper devices that not support enhanced layer 2 software (ELS), we use the belwo commands to configure DAI.
[edit ethernet-switching-options secure-access-port]
ipcisco@switch# set vlan vlan-name arp-inspection
[edit ethernet-switching-options secure-access-port]
ipcisco@switch# set vlan all arp-inspection
To verify Dynamic ARP Inspection on Juniper devices, we use “shows arp inspection statistics” command. With this Juniper command, we can see the received packets, ARP Inspection pass and ARP Inspection failed packets easily. Below, you can find an example of this command’s output.
ipcisco@switch> show arp inspection statistics
ARP inspection statistics:
Interface Packets received ARP inspection pass ARP inspection failed
————— ————— ——————– ———————
ge-0/0/1.0 25 20 5
ge-0/0/2.0 9 9 0
ge-0/0/3.0 13 0 13
As you see at the above screenshot, packets received by the interfaces. Some of them are passed and some of them failed according to the Juniper DAI configuration.
Leave a Reply