- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
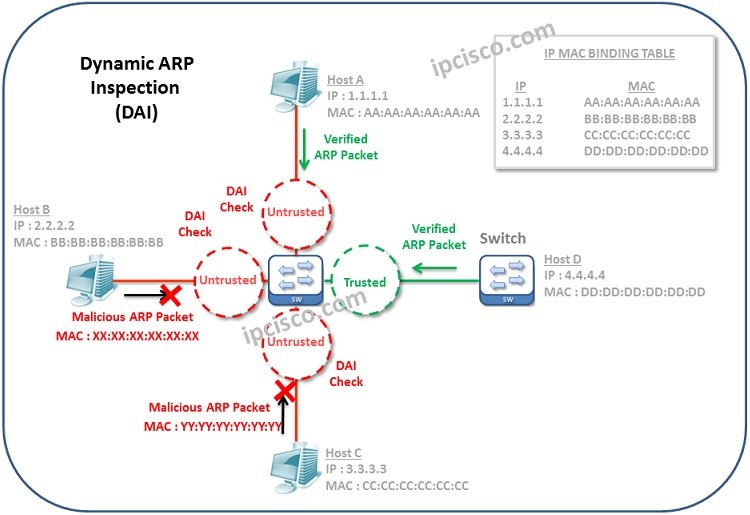
Table of Contents
Dynamic ARP Inspection (DAI) is the security mechanism that prevents malicious ARP attacks by rejecting unknown ARP Packets. ARP attacks can be done as a Man-in-the-Middle Attack by an attacker. In this type of attack, by capturing the traffic between two hosts, attacker poisons the ARP Cache and sends his/her own MAC address as requested ip address. To prevent from such a maniplation, we should validate IP-MAC matchings. Dynamic ARP Inspection does this job and validates IP-MAC matchings.
Dynamic ARP Inspection (DAI) uses DHCP Snooping binding database that is created by DHCP Snooping by listening DHCP Messages between the nodes. According to the DHCP Snooping binding database, DAI decides what to do. If there is a record in the database about sender’s IP and MAC address then it accepts the ARP Packet. If there is no record in the database, ARP packet is rejected. Instead of using DHCP Snooping, Static IP-MAC mappings can be also used for this validation process.
Dynamic ARP Inspection (DAI) uses Trust states for interfaces. There are two trust states for interfaces, these are given below:
If an interface set as Trusted, DAI does not work for this interface. But if it is an Untrusted, DAI precedures work and the MAC-IP matchings are checked. In other words, if we set an interface as trusted, we do not do a validation on these interfaces.
In a network all the interfaces connected to the hosts are configured as Untrusted while the interfaces connected to the switches are configured as Trusted. By doing this, ARP Packets are checked if it is coming from a host device. Because, generally such an attacks can come from a host interface.
By the way, Dynamic ARP Inspection is done through VLANs. One or one more VLANs can be used for this configuration.
As you can see above, if DAI is enabled, IP-MAC Binding Table is cheched and then if the incoming MAC address is in binding table, then this ARP Packet is accepted. If not, then the packet is discarded. Above, Host B and Host C is sending ARP packets including different MAC addresses maliciously. They are connected to the interfaces which were configured as untrusted. So, IP-MAC validation will be done on these interfaces. So, this malicious behaviour will be detected by Dynamic ARP Inspection Mechanism.
To configure Dynamic ARP Inspection on Cisco switches, we will use the below simple switch topology. As you can see below,m there are two switch connected to eachother and there are two PCs are connected to each switch.
AS we have mentined above, we can use DAI for VLANs. Here, we will configure DAI for VLAN 2 only. The hosts in VLAN 2 will be Untrusted. So, ARP packets coming from these interfaces will be checked for IP-MAC validation. The other interfaces will be configured as trusted interfaces.
So, let’s start to configure DAI.
Enabling Dynamic ARP Inspection
To enable ARP Inspection on VLAN 2, we will use “ip arp inspection vlan 2” command globally on a Cisco switch.
Switch A# configure terminal
Switch A(config)# ip arp inspection vlan 2
Setting Trusted interfaces
To set any interfaces as trusted we will use “ip arp inspection trust” command under that interface. On Switch A, we will set FastEthernet 0/1 and FastEthernet 0/3 as Trusted. The remaining ports will be Untrusted by default.
Switch A(config)# interface fastethernet 0/1
Switch A(config-if)# ip arp inspection trust
Switch A(config)# interface fastethernet 0/3
Switch A(config-if)# ip arp inspection trust
Here, we have set these two interfaces as Trusted. The other interface, Fastethernet 0/2 remains as Untrusted. Because by default all interfaces are Untrusted.
Switch B Configuration
Now, let’s do the similar configuration on the other Cisco switch, on Switch B.
Switch B# configure terminal
Switch B(config)# ip arp inspection vlan 2
Switch B(config)# interface fastethernet 0/1
Switch B(config-if)# ip arp inspection trust
Switch B(config)# interface fastethernet 0/2
Switch B(config-if)# ip arp inspection trust
DAI Verification
Now, it is time to verification. To verify Dynamic ARP Inspection, we can use the below show commands on Cisco switches.
Switch A# show ip arp inspection vlan 2
Source Mac Validation : Disabled
Destination Mac Validation : Disabled
IP Address Validation : Disabled
Vlan Configuration Operation ACL Match Static ACL
—- ————- ——— ——— ———-
1 Enabled Active
Vlan ACL Logging DHCP Logging
—- ———– ————
1 Deny Deny
Switch A# show ip arp inspection interfaces fastethernet 0/1
Interface Trust State Rate (pps)
————— ———– ———-
Fa0/1 Trusted None
Switch A# show ip arp inspection interfaces fastethernet 0/2
Interface Trust State Rate (pps)
————— ———– ———-
Fa0/2 Untrusted None
Switch A# show ip arp inspection statistics vlan 2
Vlan Forwarded Dropped DHCP Drops ACL Drops
—- ——— ——- ———- ———-
1 2 0 0 0
Vlan DHCP Permits ACL Permits Source MAC Failures
—- ———— ———– ——————-
1 2 0 0
Vlan Dest MAC Failures IP Validation Failures
—- —————– ———————-
1 0 0
In this lesson, we have talked about DAI. We have learned what is DAI, how it works and how can we configure DAI on Cisco switches. ARP Packets are important in a network. So, defending your network from any malicious attacks related with ARP, Dynamic ARP Inspection is an important security mechanism.
ARP Spoofing Attack is one of the Man-in-the-middle Attacks. In such a network attack, attacker establishes connection to both ends as in all MiMT Attacks by poisoning the ARP tables of both ends. Attacker write, his MAC address as destination of the packets. Both ends think that they are directly connected but attacker located among them. After that attacker intercepts all the packets between these ends and he can change these packets or insert new ones.
Dynamic ARP Inspection (DAI) protects against ARP Spoofing Attack, a Man-in-the-middle Attack and ARP Cache Poisoning.
If Dynamic ARP Inspection (DAI) is enabled on the switch, if an attacker sends a malicious ARP packet, it detects this malicious behavior and discard this ARP packet. If these attempts exceed a threshold, then switch generates alarms.
ARP (Address Resolution Protocol) is one of the common protocols of networking. The main duty of ARP is mapping IP address to MAC address. In other words, ARP maps layer 2 address to layer 3 address. How does ARP do this in a network? How does ARP Work? Let’s explain ARP mechanism step by step with the below simple topology.
Let’s think that, PC 1 will send a packet to PC 4 over this switch. To do this:
By the way, to check ARP Cache on a PC, we use “arp -a” command.
PC1:\> arp -a
Internet Address Physical Address Type
192.168.1.4 dd-dd-dd-dd-dd-dd dynamic
Dynamic ARP Inspection (DAI) protects ARP mechanism, switch ARP Caches, towards ARP Spoofing Attacks. DAI does this by configuring switch ports as trusted ports and untrusted ports as we have mentioned above
DAI protects against ARP Spoofing attacks with which attacker establish a connection as Man-in-the-middle attack and posion ARP tables on both ends.
DAI has two trust states: Trusted and Untrusted.
In global configuration mode, we can use “ip arp inspection vlan vlan-id” command to enable DAI in Cisco devices for a VLAN.
We use Dynamic ARP Inspection Juniper command, “set arp-inspection“, to enable DAI on Juniper routers.
Leave a Reply