- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
Cisco TrustSec is an umbrella name of a Cisco proprietary network security solution. It is basically a next generation access control enforcement based on strong identify capability of the devices in the network. In this lesson, we will learn What is Cisco TrustSec, how Cisco TrustSec works detailly. We will also focus on Cisco TrustSec Configuration Phases. You can also check IEEE 802.1AE MACsec.
So, let’s start with what is Cisco TrustSec?
Cisco CCNP ENCOR and Cisco CCNA Courses!
Table of Contents
Cisco TrustSec is basically a network security enhancement. It is the umbrella name of some security improvements on network access. It is a Cisco proprietary solution which was developed by Cisco to overcome security needs of growth networks.
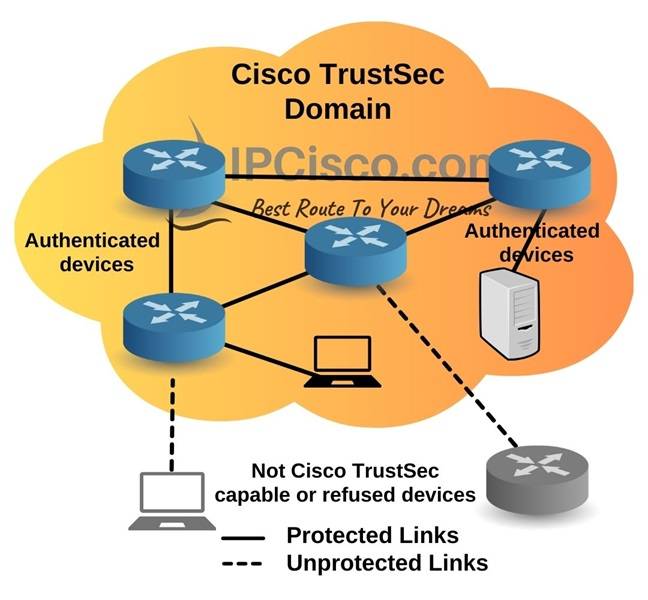
Cisco TrustSec builds a secure network by establishing trusted network domains. In such a domain, each device is authenticated by its peers. Beside this authentication process, the links between the peers are also secured with encryption, integrity check and reply protection mechanisms. Below, you can find a simple TrustSec topology. As you can see below, the devices in TrustSec domain and the links between them are secured, they are protected. The Non-Cisco TrustSec capable or refused device links are unprotected.
In this Cisco TrustSec topology, each participant has different roles. Here, there are three main roles. These are:
Supplicant is the device that is not authenticated within Cisco TrustSec yet. It is attempting to join the network.
Authentication server is the server which validates the identity of the supplicant and assigns policies.
Authenticator is the authenticated device in the TrustSec network which can authenticate new peers on behalf of authentication server.
Cisco TrustSec builds security and intelligence into the network with:
Cisco TrustSec does this with role-based approach. What is this role-based approach?
In today’s networks network security is very important. Generally, network security is provided by access lists and firewall rules. This is done with IP addresses. But with the growth of the networks, especially in large networks, it is difficult to manage such operations. To overcome this overhead, Cisco TrustSec has developed. With its new approach, instead of IP addresses, it manages network security with roles. Different users, hosts, devices that have different network roles are classified with ingress tagging and according to their roles different policies are applied to them at the egress point. Cisco TrustSec does this tagging with SGT (Security Group Tag). So, what is Security Group and SGT?
A security group is the group of devices or uses that share access control policies. Whenever a new device or a host comes to Cisco TrustSec domain, authentication server assigns these hosts or devices to an appropriate security group. These security groups can be defined in Cisco ISE or Cisco Secure ACS. In TrustSec domain, Security Group Tag (SGT) is attached to each Security Group.
SGT (Security Group Tag) is a 16-bit security group label assigned to a security group for classification of the source. It is unique in the TrustSec Network for that security group. SGT (Security Group Tag) shows the privileges of the source in the domain.
SGT is appended to layer 2 Ethernet Frame or Layer 3 IP Packet. The other name of SGT is Scalable Group Tags in Cisco SD-Access.
If a device is authenticated in Cisco TrustSec domain, whenever this device sends a packet, Cisco TrustSec tags this packet with an SGT (Security Group Tag). This SGT is carried inside the TrustSec header through the domain.
SGT (Security Group Tag) is used for ingress tagging for the identification and egress control policy enforcing. Cisco ISE (Cisco Identity Services Engine) assigns SGTs to the users after authentication and authorization process. This authentication and authorization process is done with 802.1x, MAB or WebAuth. At the egress point, an access enforcement policy is applied according to the assigned SGT.
SGACL (Security Group Access Control Lists) is an Access List (ACL) with which we can control which security group perform which operation. In other words, SGACL controls and manages authorization of the security group members.
SGACLs build SGACL policies. These SGACL policies are represented by permissions matrix in TrustSec domain. In this permission matrix, there are security group numbers and destination security group numbers. Below, you can find an example for SGACL policy.
By the way, SGACL (Security Group Access Control Lists) defines access control policies based on the identity, the role of the device, not IP address of the device like traditional ACLs. Here, users can move any place in the Cisco TrustSec domain.
We have learned what is TrustSec. Now, let’s focus on TrustSec configuration phases. There are three configuration phases of Cisco TrustSec. These TrustSec phases are given below:
Below, you can see these phases on a TrustSec Topology.
Now, let’s learn these TrustSec Phases one by one a little more detailly.
Classification phase is the process of SGT (Security Group Tag) assignment.
Classification or SGT assignment can be done in two ways. These classifications ways are given below:
Static SGT assignment is done manually by mapping SGT to an ip address, a subnet, a vlan or a port-profile. Static assignment is used for stable devices for example servers.
Dynamic SGT Assignment is done by Cisco ISE. It is mostly used for users. Because users move. They are mobile and they can connect with different medium, wired, wireless or VPN.
After the classification phase, the next step is Propagation phase. In propagation phase, SGTs are propagated from ingress to egress where the enforcement is done.
There are two different methods for Propagation. These propagation methods are given below:
In SGT Inline Tagging, SGT is embedded into the frame. The upstream device reads this and applies the policy. The other name of SGT inline tagging is Native Tagging. Inline tagging needs Cisco ASIC support for TrustSec. So, if a tagged frame is received by a Cisco device that does not support this, then the packet is dropped.
SXP (SGT Exchange Protocol) is the second way of propagation. It is a Cisco proprietary, TCP-based peer-to-peer protocol. SXP is used when there is no hardware support. Here, IP to SGT mappings is shared. The device that shares this information is called speaker and the received end is called listener.
The last step of Cisco TrustSec process is Enforcement phase. Enforcement is done at the end on a Cisco firewall, a switch or a router. Here is the point where the policies are executed. Role based ACLs (RBACLs) are used in this phase. There are different methods for enforcing traffic based on SGT. Two of them are given below:
Security Group ACL (SGACL) enforces policies on switches or routers. Here, SGACLs do egress filtering based on source and destination SGTs. These Security Group ACL (SGACL) rules are in Cisco ISE centrally.
Security Group Firewall (SGFW) enforces policies on firewalls like Cisco ASA or Cisco Next Generation Firewall (NGFW). Here, Security Group Firewall (SGFW) rules are locally stored with tags.
Some of the Cisco devices supports this new enhancement and some of them are not. There are three support levels here. In other words, we can classify the network devices according to Cisco TrustSec support into three categories. These supporting levels are given below:
If a device Cisco TrustSec Capable, it supports full TrustSec capabilities with hardware acceleration for Security Group Tag imposition and IEEE 802.1AE MACsec.
If a device Cisco TrustSec Aware, it does not support Security Group Tag imposition or IEEE 802.1AE MACsec. But it can forward Security Group Tag information to a TrustSec capable line card for egress.
If a device is Not Capable of Using Cisco TrustSec, it does not support Security Group Tag imposition or IEEE 802.1AE MACsec. It cannot do any forwarding decisions with Security Group Tag information.
Leave a Reply