- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
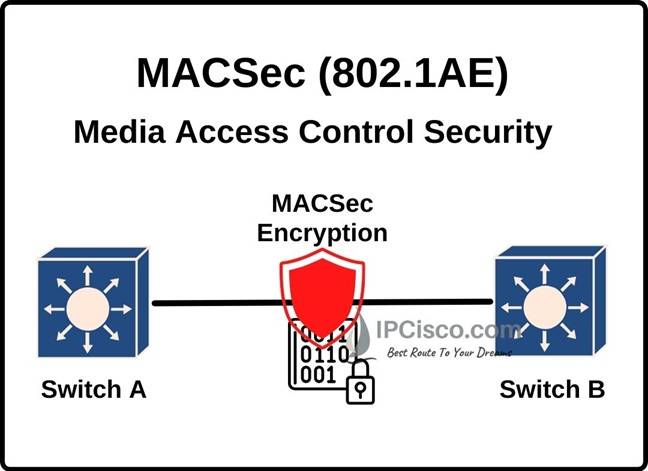
Table of Contents
The basic answer of what is MACsec question is this, MACsec (Media Access Control Security) is a standard based layer 2 security protocol which provides point-to-point security on Ethernet links between two MACsec-capable devices. The IEEE standard name of this protocol is standard 802.1AE. It provides Authentication, MAC-layer encryption and data integrity check between two Media Access Control Security capable devices. With this mechanism, Media Access Control Security detects many network attacks like Denial of Service (DoS), Man in the Middle (MiTM) attacks and it secures ethernet towards these malicious threats. We can use Media Access Control Security with different network security protocols like IPSec and SSL.

In Media Access Control Security mechanism, the traffic between nodes is encrypted. But in the nodes, the traffic is not encrypted. This provides flexibility for the services like QoS on the device. The encryption between the nodes prevents Layer 2 security threats, like denial of service, intrusion, man-in-the-middle, passive wiretapping, playback attacks etc.
Cisco Catalyst switches support 802.1AE encryption with MKA (MACsec Key Agreement) on the ports towards host devices (Downlink ports). These ports are the switch ports which are connected to end devices like PCs and IP Phones. The settings can be configured manually or dynamically. For dynamic configuraion, Cisco ISE is used.
Media Access Control Security is also supported on the ports towards other switches (Uplink ports). Here, instead of MKA, uplink MACsec uses TrustSec NDAC (Network Device Admission Control) and SAP (Security Association Protocol) Cisco proprietary solution.
Uplink MACsec can be done manually or dynamically. If we use dynamic one, switch must use 802.1x Authentiaction.
Media Access Control Security secures the communication between two nodes by using several configurable techniques. Here data is authenticated and it is tranported over a secured channel. For this security, Media Access Control Security uses a combination of data encapsulation and data integrity check. The frames are validated as MACsec ethernet frames and frame integrity is verified at the other end. Beside the sequence of the frame is monitored with a counter. If are there any invalid frame, it is dropped.
In the encapsulation step, Media Access Control Security encrypts the data on the link which resides between the nodes. In other words, MACsec provides MAC-layer encryption over wired networks with out-of-band methods for encryption keying. To do this, security keys are used on both ends of the link. At both end interface, security keys must match. The keys that will be used for this encryption can be configured manually or it can be done dynamically. It is up to the selected mechanism.
Media Access Control Security does not only encrypt the data between nodes, but also it provides data integrity. Media Access Control Security uses a header and a tailor for this purpose. This header and tailer are checked towards any data integrity problem at the other end.
Media Access Control Security encapsulates IP packets with a 16 bytes MACsec Security Tag and 16 bytes Integrity Check Value (ICV).
Media Access Control Security is used in Ethernet frame. But with Media Access Control Security, two fields are added to the ethernet frame. These are MACsec Security Tag and Integrity Check Value (ICV). Below, you can find the fields of Media Access Control Security and ICV field.
MACsec Security Tag fields are given below:
Now, let’s learn that why we use these fileds in MACsec Security Tag.
MACsec EtherType: EtherType field is 16 bits long. The value of EtherType is 0x88e5 for Media Access Control Security.
TCI/AN: TCI/AN field is 1 byte long. The full name of this field is Tag Control Information/Association Number. The role of this field is designating the version number if confidentiality or integrity is used
SL: Short Length field is 1 byte long and shows the length of the encrypted data.
Packet Number: Packet Number is 4 bytes long. It is the number for replay protection and building of the initialization vector.
SCI: Secure Channel Identifier is 8 bytes long. It is used to classify the connection to the virtual port.
With Media Access Control Security, we can use two different Media Access Control Security keying mechanism. These are given below:
SAP (Security Association Protocol) is a Cisco proprietary keying protocol. It is used only on Cisco devices.
MKA (MACsec Key Agreement Protocol) is a standard protocol which provides required session keys and manages encryption keys.
Leave a Reply