- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
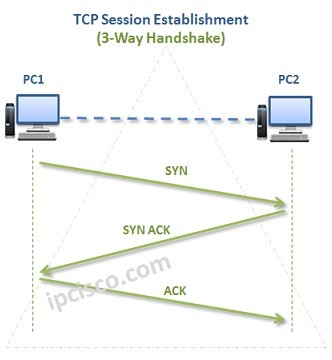
Table of Contents
TCP (Transmission Control Protocol) is the most important Transport Layer Protocol. It is also one of the important Protocols of network world and Cisco CCNA Certification. The other Transmission protocols are UDP and SCTP. We will talk about these protocols in another lessons like TCP vs UDP lesson. TCP Protocol is used in many cases in the computer networks. Here, we will focus on an overview of this important Protocol.
First of all, TCP is a Connection Oriented Transport Protocol. A TCP session must be established to use TCP. This TCP Session is established with a Three-way Handshake mechanism. And it can be terminated with Four-way Handshake mechanism. So how does these two important mechanism work? Let’s firstly check these mechanisms.
Three-way Handshake mechanism consists of three messages as its name implies. These messages are:
In these segments, related TCP Header Flags are set to 1. If it is a SYN message, SYN bit is set to 1. If it is a SYN-ACK message, SYN and ACK bits are set to 1. Or if it is an ACK message, ACK bit is set to 1.
Four-Way Handshake mechanism is used to terminate the TCP Sesssion. In Four-Way Handshake, both ends send two messages. Total 4 messages are sent. So what are the messages used in TCP Four-Way Handshake mechanism? These messages are given below:
In FIN message, FIN bit is set to 1. In ACK message, ACK bit is set to 1.
As you can see above, there are two different messages and these messages are sent from both ends to terminate the TCP sessions.
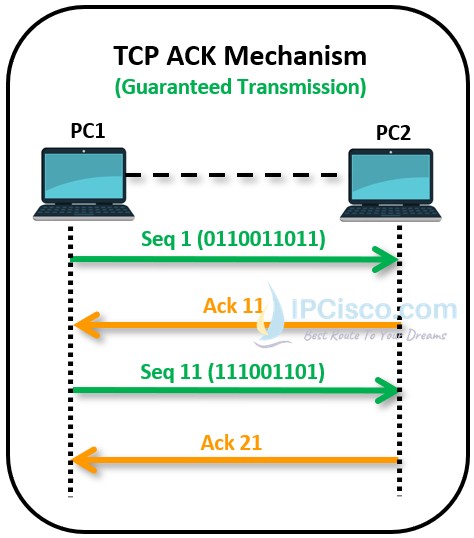
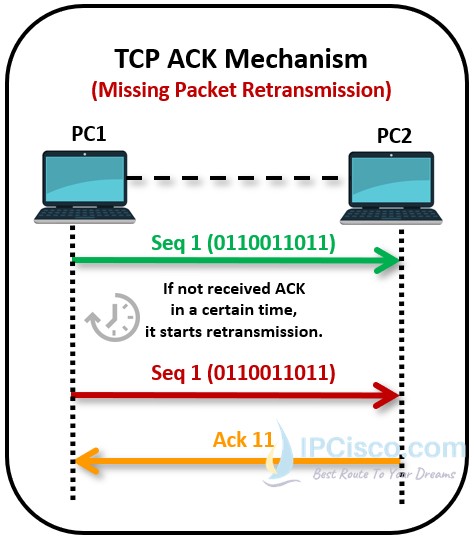
Transmission Control Protocol is a Secure and Reliable Protocol. It guarantees the transport of the data. TCP Protocol controls the bits with Sequence Numbering and ACK mechanism. By using this mechanism, if are there any missing bits in the transmission, it retransmits these missing bits and it prevents data loss. So, TCP can be used for the critical applications that require high reliability.
Below, you can check Ack mechanism used by Transmission Control Protocol. Here, firstly the data which has sequence number 1 is sent. In our example, this is 10 bits data. After first 10 bit transmission, receiver sends forward acknowledgement which means that you can send 11. bit. The sources sends another ten bits with sequence number 11 and then the destination sends forward acknowledgement for this transmission. With this ACK, it says, you can send 21. bit.
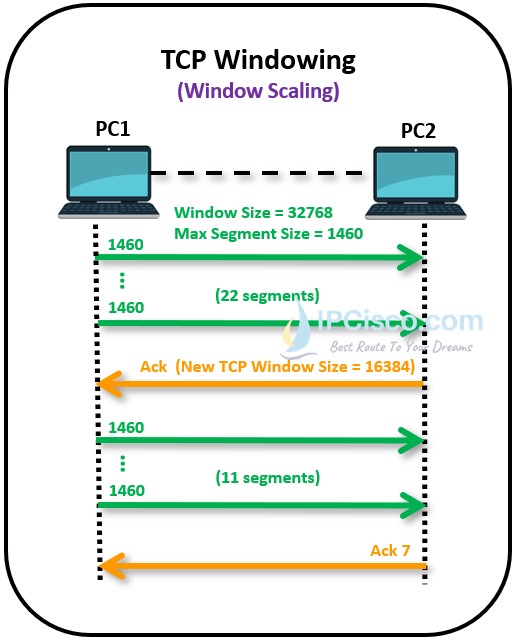
TCP has also a Flow Control Mechanims. It controls the sent data with Window scaling. Here, a window size is used and the data is sent with this fixed size. The sender send data with a window size and it increase it every transmisssion. If the sender exceed a certain value, the destination sends an Acknowledgement that request to decrease window size. This is TCP Window Scaling mechanism.
In data transmission, sometimes bits can send out of order. The sender sends the data packets in different times and at the receiver side, this data must be reordered to create a meaningfull data. Transmission Control Protocol has this reordering mechanism. The packets that are sent unordered, are reordered at the destination
Below, after Sequence 1, Sequence 11 is sent. But for any reason like delay, the receiver receives Sequence 11, later than Sequence 21. At the receiver end, this out of order data needs to be reordered. And TCP Reordering Mechanism do this job for a meaningful data.
Some protocols and applications uses TCP well-known ports. Below, you can find the protocols and the applications use only TCP ports:
Beside, DNS uses both TCP and UDP port 53.
TCP Header is a little complex if you compare with UDP Header. The total TCP Header length can 20 and 60 Bytes long in total.
What are the fields in a TCP Header? These TCP Header fields are given below:
Below, you can find an example TCP header that resides between IP Header and Data.
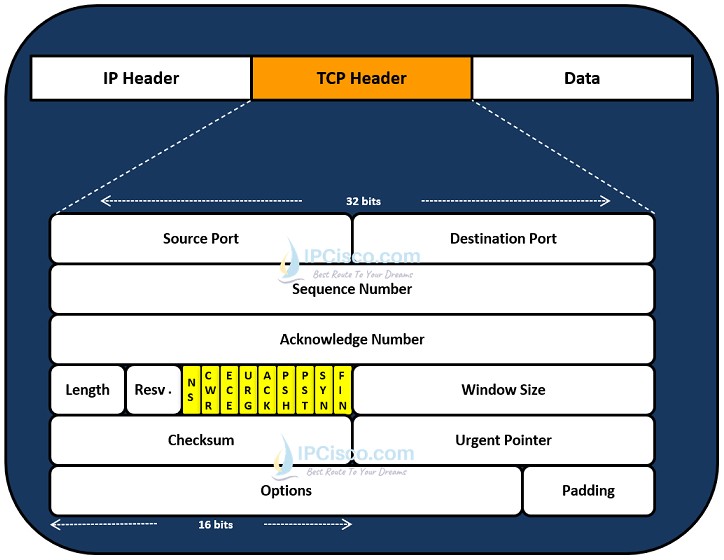
In the following lessons, we will talk about TCP Header fields and their roles detailly.
Leave a Reply