- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
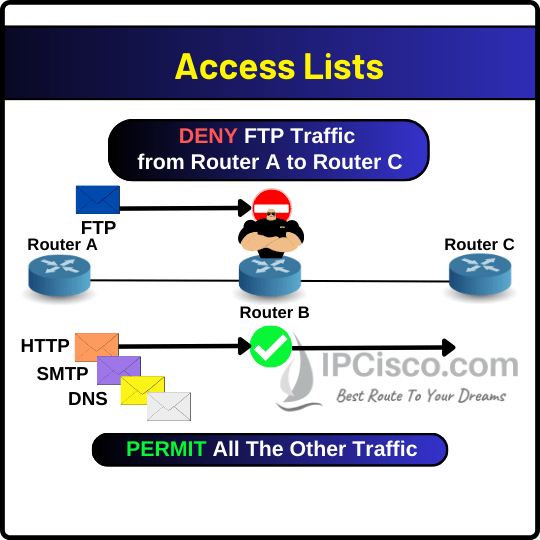
Table of Contents
Access Control Lists (ACLs) are one of the security and control mechanism used in routers. It is an important lessons of Cisco CCNA 200-301 and CCNP Encore 350-401 Certifications. They mainly filters incoming and outgoing traffic coming to a router or going from it. In other words, with the help of access list control, we can filter traffic coming from any where and going to any where. We can create Access lists by using various parametters like source ip address, destination ip address, protocol, port number etc.
For example, with an access control list, we can deny some users to access a specific server or service. Or we can allow only the people in a specific network to use FTP towards another network. Or we can limit one network to ping another. There can be many combinations and different ACL lines according to your need.
As an access control list example, you can check the below ACL shape. In this ACL example, we configure an Access list on Router B. This access list denies FTP packets coming from Router A network to Router C network. This is done by adding source network address with its subnet mask and destination network with its subnet mask. after that we define FTP traffic with ftp keyword or with the default FTP ports (20 and 21).

There are different access control list types used in networking. Each of them is used for various purposes and needs. According to your need, you can use one of these access list.
These access control list types are given below:
Now, let’s briefly explain these ACL types. We will explain these ACL types in the following lessons detailly.
Standard Access-Lists are the ACLs which uses only source addresses of the traffic. In other words, they filter the traffic according to their source. ACL numbers 1-99 and 1300-1999 are used for standard access control lists. Standard ACLs are added close to the destination.
Extended Access-Lists are enhanced versions of standard ACLs. In Extended ACLs, source, destination addresses, port numbers and protocol types are used to filter the traffic. ACL numbers 100-199 and 2000-2699 are used for extended access control lists. Extended ACLs are added close to the source.
In the below access list example, we permit only SSH packets and deny all the other packets coming form Router A to Router C. We can do this by entering permit keywords and then source network ip address with its subnet mask and destination ip address with its subnet mask. After that we can write SSH default port number or SSH keyword.
For the below access list example, firstly we permit TCP traffic coming from a specific network (10.0.0.0/24) to a specific network (30.0.0.0/24). Then we deny TCP traffic from a specific network (20.0.0.0/24) to a specific network (30.0.0.0/24). By the way we do not need to enter this last part because, if we do not use “permit any any” command, there is an Implicit Deny at the end of the ACLs which denies all the other traffic.
Named Access-Lists are the ACLs, which uses ACL names instead of ACL numbers. They can be used with both Standard and Extended ACLs. These type of ACLs are more memorable because of the explanatory names.
ACLs are created according to their type and each line after this creation is suitable to this type. This means that, if you are using standard ACLs, you can use only source addresses in the lines of ACLs. Or if you use extended ACL, you can use source, destination addresses and protocol or port information.
To use Access Lists in a network, there are some steps. These steps are given below:
Firstly we need to create the ACL. To do this we will need an ACL number or a memorable name for our access control list.
Secondly, we should add required entries to the ACL according to our needs. These entries consist of one or more permit/deny lines.
Then, we will determine the interface that we will add this access list. According to used ACL type the location can be different.
After determining the interface, it is time to determine the direction of this apply. This can be also different according to used ACL type.
Laslty, we will add the linet hat will add our ACL to the interface.
ACLs works not when they are created but when they are added to an interface. After adding them to an interface, they controls the traffic of that interface and according to its entries, it determines what to do to the traffic of this interface.
After creating and adding an ACL to an interface, whenever a traffic comes this interface, it firstly checks the lines of the access list control orderly. If it finds any entry that matches to the traffic, it stops and acts as the matched line. For example if it is a deny line, it denies the traffic that matches it. Or if it is a permit line, it allows this traffic.
After checking all the lines, if you do not use “permit any any” command, it will reject all the other traffic because of the invisible implicit deny at the end of the line. Implicit deny denies all the other traffic that do not match your entries. So, if you use ACL to deny some specific traffic only, you should use “permit ip any any” line to accept any other traffic. If you do not add this entry, not only your deny lines are denies but also all the other traffic are denied. This is an important problem and can cause critical traffic drops. So, you should be careful during access list configuration.
Leave a Reply