- COURSES
- SPECIALS
- BLOG
- MEMBERS
- SHOP
- ABOUT
- ENROLL HERE
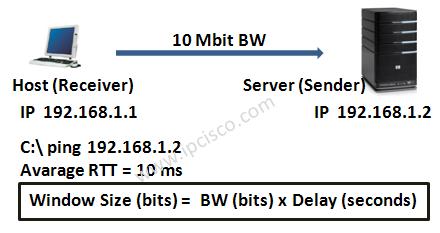
Table of Contents
The window, checksum and urgent pointer are another important fields in TCP header. Each of these fields are 2 bytes long. Now, let’s focus on these parts one by one and learn these details of TCP Header. We will start with TCP Window Size.
Window size the most important part in the TCP header. This fields is used by the receiver to indicate to the sender, the amouth of data that it can accept. So, this field is very important for efficient data transfer and flow control.
Window size uses byte as a metric. If it is mentined that window size is 60k, then it means that receiver accept 60 kilobyte data. When the data transmitted reaches window value then sender expect another window value from the receiver along with the acknowledgement for the window just received.
Window size is not a random value. It is calculated with some parameters like below:
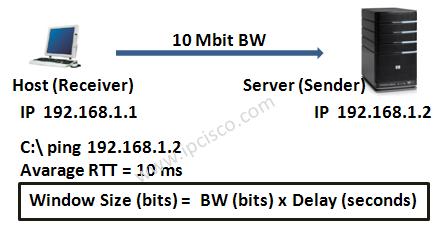
BW=10 Mbit
Delay(Avarage RTT) = 10 ms
Window Size = BW (10000000) x Delay(0.01)
= 100000 bit
= (100000/8)/1024
= 12,5 kbyte is equal to nine 1460 byte segments

By default 63 bytes window size is used. But the link monitored and some small increase or decrease can made to optimize this size. This is called “automatic self correcting mechanism”.
In the case when window size falls to zero, then the remote TCP can not send data until receiving another window size.
Think about a host connection to a web server. Web server needs small amouth of memory (RAM) different than the client session. This memory size is equal to window size. And this is dependent to tha bandwidth and delay between host and the web server.
Checksum field provides the data to reach error-free to the correct destination. For this purpose an extra header called “pseudo header” is used.
Here, let’s talk about pseudo header a little. The pseudo header is a combination of five fields. These fields are 32 bit source ip address, 32 bit destination ip address, 8 bit zeros, 8 bit protocol field and 8 bit TCP length. Totaly 88 bits or 11 bytes.
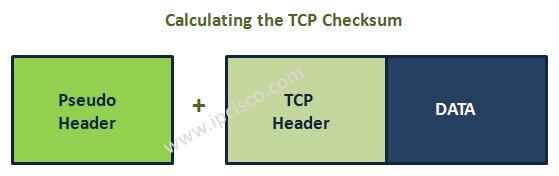
The checksum field is zero at the initial calculation.Because it is a unknown. When the value is calculated then it changed with 0.
Here we will recall some information that we discuss before. This is urgent pointer flag. As I mentined before, with urgent pointer flag, the data is signed as urgent. And with the urgent pointer field, the exact end of this urgent data is determined. Here urgent pointer field contains the address of the urgent data ends.
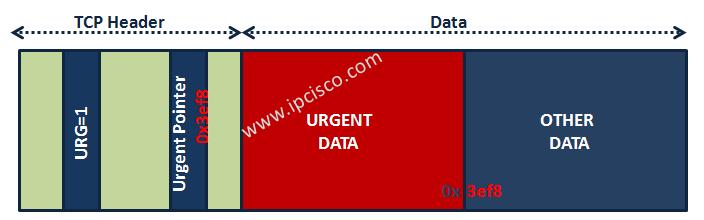
From the point of security, urgent pointer flag set can be used by attackers. Because some system guards do not check the packets that has urgent pointer flag set. This is a security vulnerability.
That’s all for these parameters… Let’s go the the last part of the TCP header article series…
Comparison of UDP and TCP Protocols!
Leave a Reply