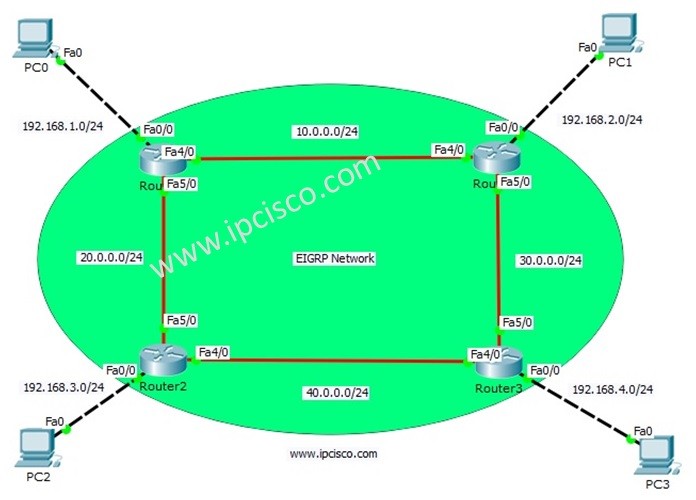
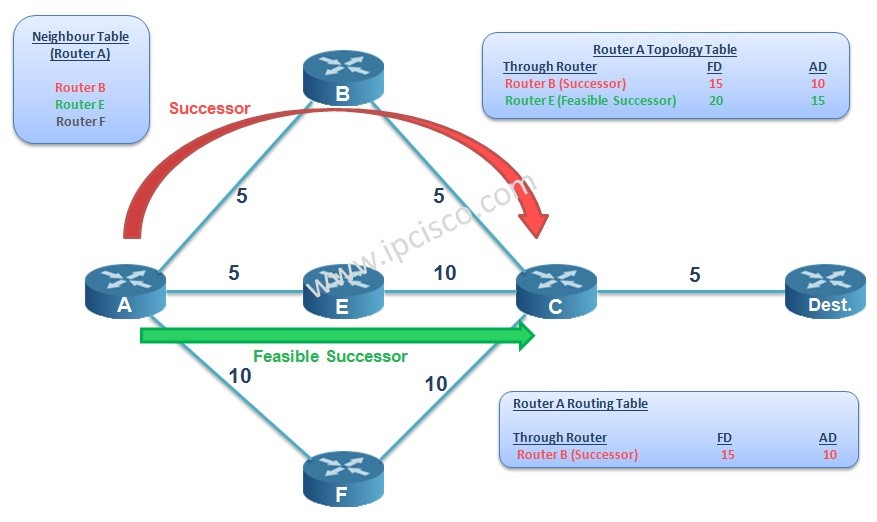
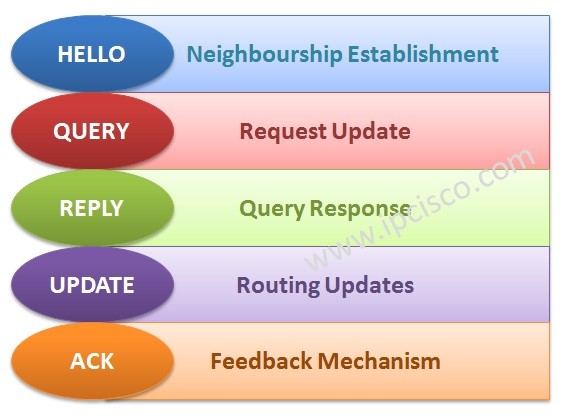
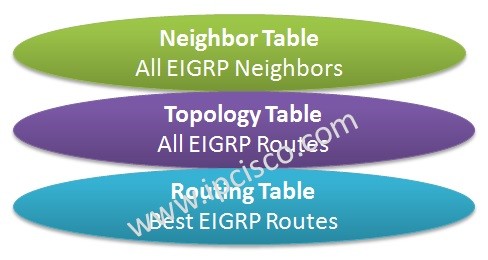
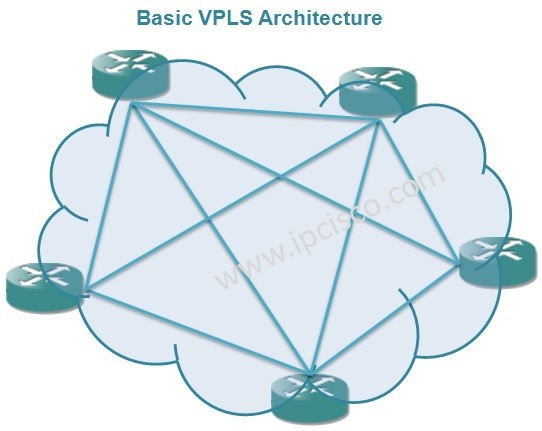
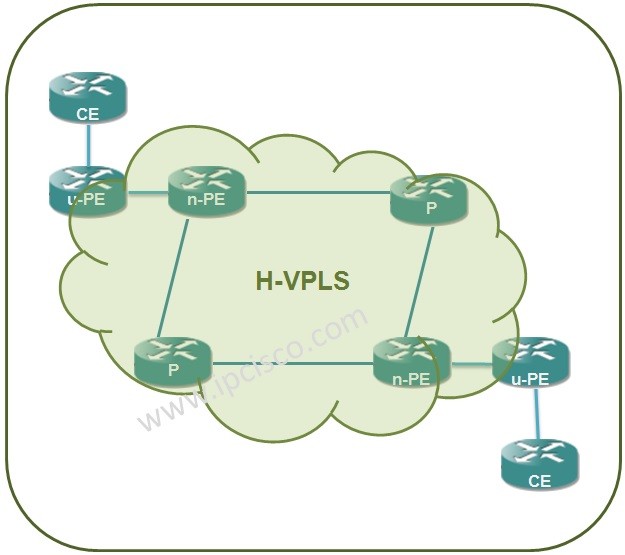
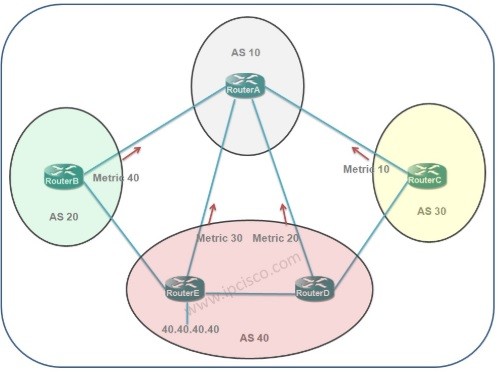
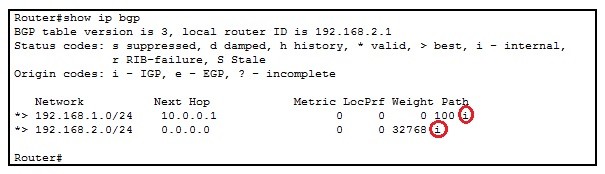
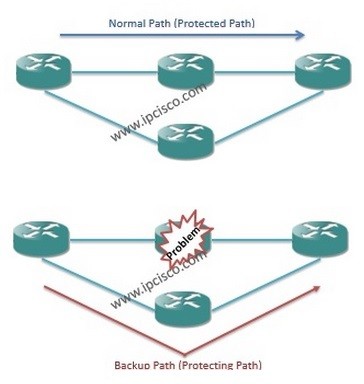
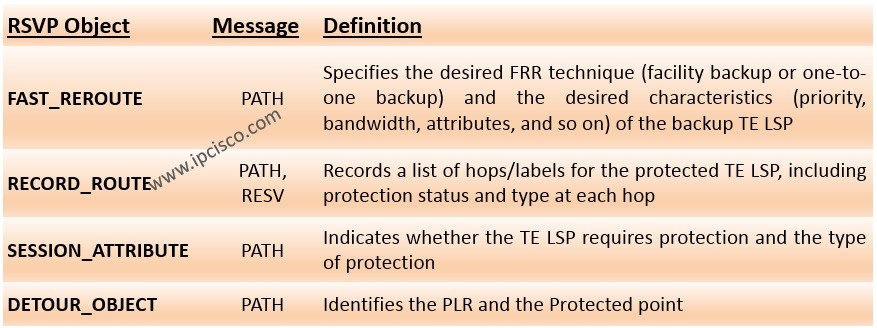
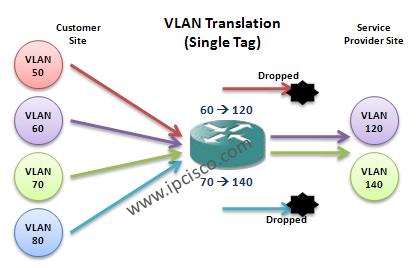
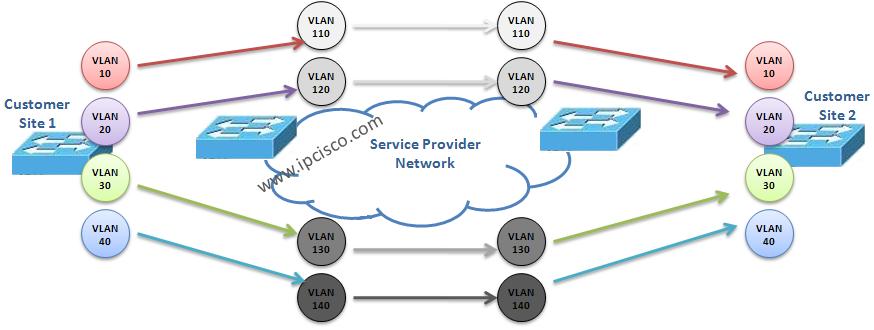
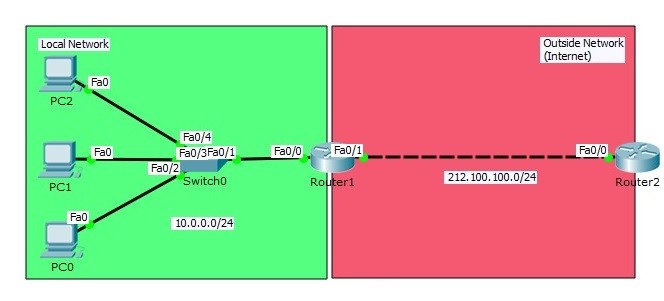
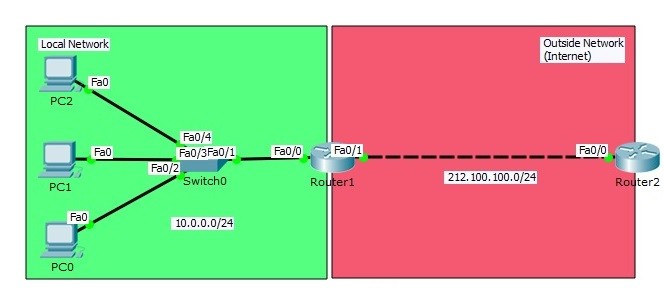
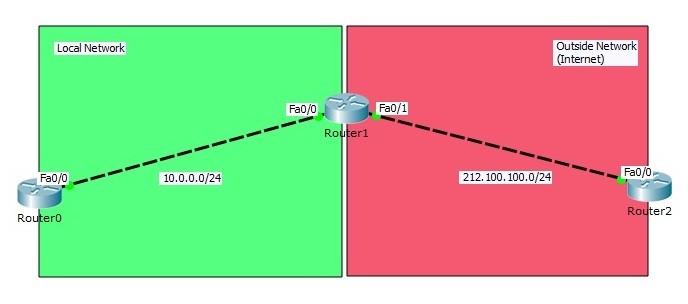
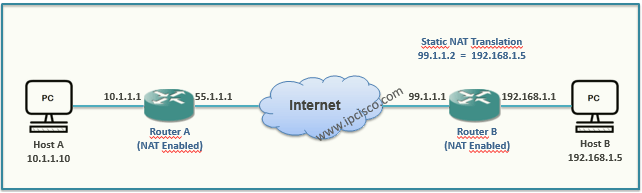
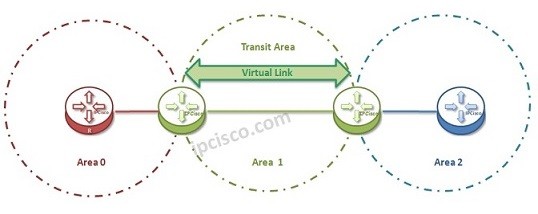
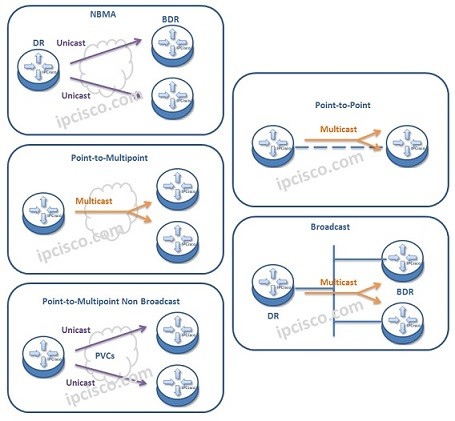
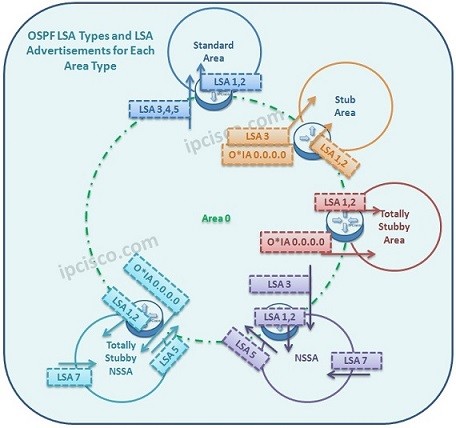
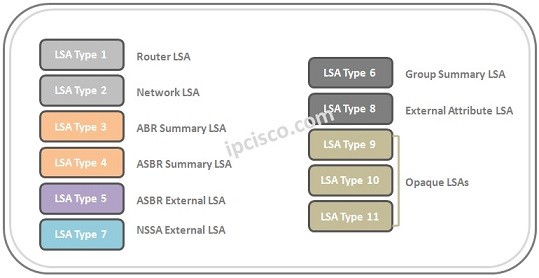
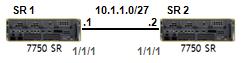Cisco Interview Questions
Cisco Systems is one of the important vendors in information technology and network field. Many network engineers work with Cisco devices during their career and almost all network engineers dream to work in Cisco Systems. Cisco Systems is the industry leader in computer networking field.…
Network Operating System
What is NOS? A NOS (Network Operating System) is a special software that is designed for network equipment like router, switches, firewalls etc. Different vendors have different Network Operating System for their devices. Some of them also have multiple Network Operating Systems for their device…
SFP
SFP (Small Form-factor Pluggable) is a hot-pluggable network interface module used in the network devices of today’s computer networks. In this lesson, we will focus on what is SFP? Why we use these network interface modules and what are the types of SPFs. As a…
CCNA Minor Update! | CCNA 200-301 v1.1
CCNA is the entrance level certification for entry level network engineers. CCNA lessons covers all the entrance level networking levels that a network engineer need. According to the technology trends, certification content is being updated always. Here, we will cover the latest minor update in…
Cisco Packet Tracer Overview
Network engineers need practice on routers and switches. They use different emulators and simulators to gain hands on experience on Cisco devices. In this lesson, we will focus on one of these popular networking simulation tools, Cisco Packet Tracer. We will learn what is Cisco…
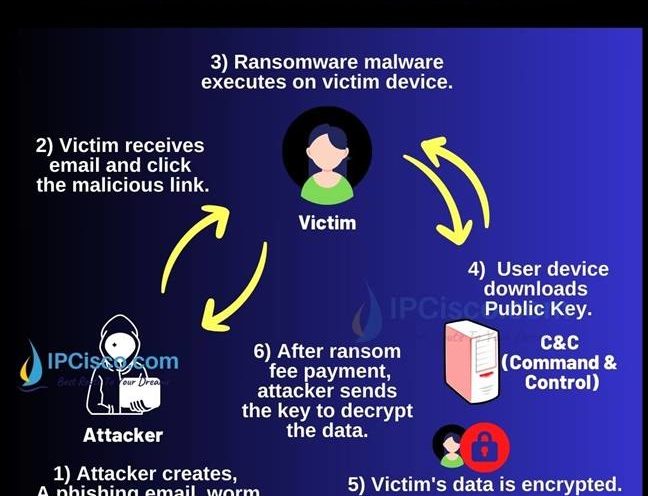
Ransomware Attack
Ransomware Attack is one of the most used cyber security attacks today. It is mainly an attack against user data. In this lesson, we will learn what is ransomware attack, how ransomware attack works and how to prevent ransomware attack. We will also learn popular…
Top 10 Network Certifications 2024
In network world, there are different network certification. Some of these network certifications are very popular between network engineers, network administrators and network technicians. In this post, we will explain Top 10 Network Certifications 2024. Let’s see these popular network certifications of 2024 in two…
Download Kali Linux and VMware Workstation Player Installation
Kali Linux is one of the most popular Linus Distros especially between network security and cyber security engineers. In this post, we will focus to download Kali Linux and Install it to VMWare Workstation Player. Here, we assume that you have already an installed VMware Workstation…
What is ChatGPT and How to Use It?
ChatGPT is one of the most popular technological developments of recent times. In this article, we will address this important development of artificial intelligence and we will answer the questions such as what is ChatGPT, what can we do with Chat GPT and How to…
What is New in CCNP ENCOR v1.1 Exam?
CCNP ENCOR 350-401 Exam is the required exam for CCNP ENCOR (Implementing Cisco Enterprise Network Core Technologies) or CCIE Enterprise Infrastructure Certification. Various network lessons are covered in this exam and now, these topics are updated. The latest CCNP 350-401 ENCOR v1.1 Exam is, CCNP…
EVE-NG Download and Installation
In this EVE-NG VMware installation post, we will focus on one of the popular network emulators, EVE-NG. We will learn what is EVE-NG, why we use it and how to install EVE-NG. We will start with EVE-NG Download and then we will go through EVE-NG…
VMware Download and VMware Workstation Installation
VMware is an amazing virtualization platform for network engineers, system administrators and other information technology professionals. In this article, we will focus on VMware Workstation Player. We will learn VMware Download and VMware Workstation Installation step by step. With VMware, you can create virtual…
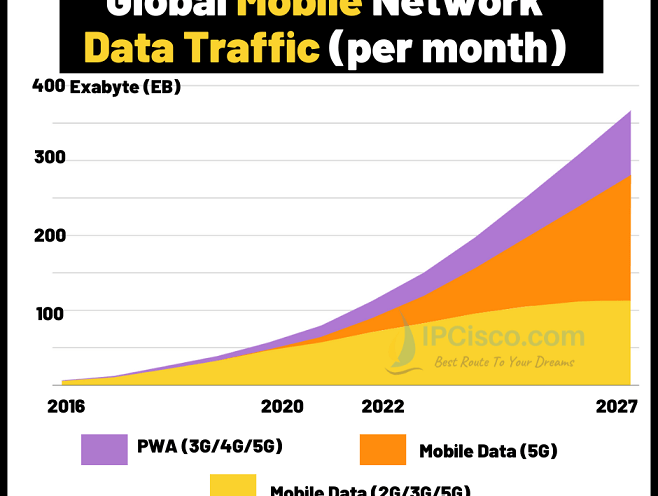
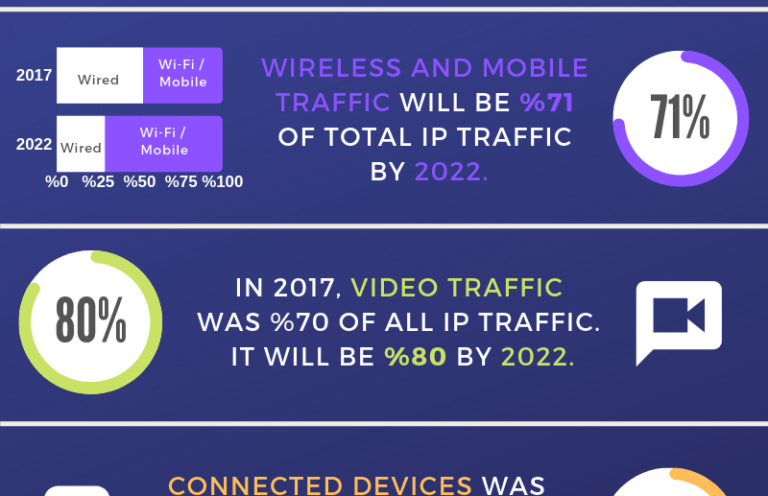
Global Mobile Data Traffic Forecast 2027
In today’s tech world, mobility is very important. Mobile data traffic has increased day by day and now, it is important than fixed data traffic. In the near future, mobile traffic will continue to increase rapidly according to the researches. In this article, we will…
14 Popular Ways To Study CCNA Online
Most Popular Online Ways To Learn CCNA Network Certifications are very popular in networking World. Many network engineers, network admin and network technicians are studying network certifications to get a certification which shows their capability on computer networks. Cisco CCNA Certification is one of these…
Cisco Live 2022 Is Upcoming!
What is Cisco Live? Cisco Live is a traditional Cisco Event that exist for many years all over the word. The event is done in different countries and in different dates in a year. Network world and in general IT world interested in this global…
Top 10 Network Certifications
Networking Certifications has served as a stepping stone for those seeking to advance their careers in Networking, h they are beginners or seasoned professionals. The great thing about Network Certifications is that they show you what you don’t know, they give you a guided way…
Amazing 28 Metaverse Jobs!
Metaverse is one of the most popular cases of today ’s and the near future’s technology world. Second life is the other name of this virtual universe. In the near future, Metaverse will be in our lives. Today, we are already using some new digital…
WiFi 6e
Technology is evolving very fast and wireless networks take their share from this evolution. One of the last Wi-Fi technologies was Wi-Fi 6. But the new wireless technology has passed Wi-Fi 6. In other words, one of the most important upgrades of the last 20…
WiFi 6 vs WiFi 5
Wireless technology is evolving every day. From the beginning of wifi technology, a new standard has developed and release almost every 5 years. And lastly while we were using Wi-Fi 5, a new standard, Wi-Fi 6 has developed. Then, lastly an enhancement came to this…
16 Reasons To Learn Linux
In the recent years, IT guys ask a question: “Why i should learn Linux?” In this post, we will answer this questions with 16 reasons to start learning Linux. Linux is one of the post popular operating systems for Information Technology Employees. System Administrators,…
How to Install GNS3 with VMware?
GNS3 is one of the most used network simulators in networking world. We can use this program to practice on various network devices by loading their images to GNS3. To have more opportunity on GNS3, we can use virtual machines with this program as GNS3…
15 Reasons To Have Cisco CCNA Certification!
In network world there are different vendors like Cisco, Nokia, Huawei, Juniper, HP etc. And all these vendors has their own networking certification paths. A network engineer candidate or an existing network engineer, starts one of these certifications paths and learn networking protocols and configurations…
How to Install Cisco GNS3 IOS Images?
GNS3 is one of the most used network simulators in network world like Cisco Packet Tracer. Many network engineers start to learn router and switch configurations with a simulator program. One of these network simulator programs is GNS3. Before using GNS3, the required router or…
FTP and FTP Ports
In this article, we will focus on File Transfer Protocol (FTP), FTP Ports and FTP Modes. We will firstly learn what is FTP. And then, we will learn ports of FTP. After that we will see FTP active and passive modes. We will learn FTP…
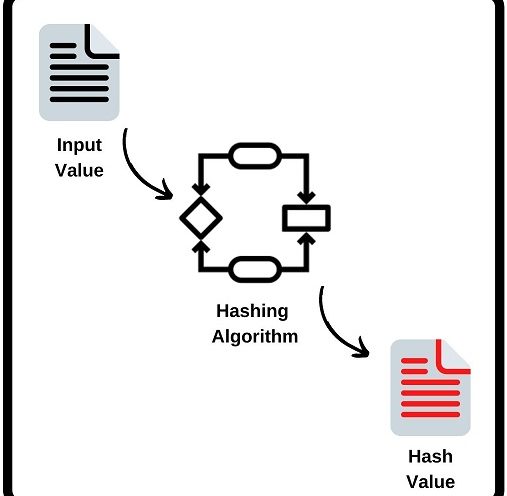
What is a Hash?
In this post we will learn what is hashing or what is a hash? We will try to explain hash function in cryptography. This term is a security term used in Information technology. So what is hashing? What is hash? Hashing is basically converting…
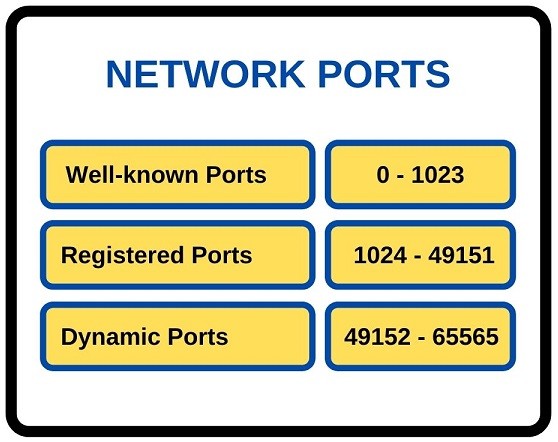
Network Ports
In computer networking, there are network port numbers used for various applications. The range of these network ports are from 0 to 65535. There are three different port types used networking. These network port types are given below: Well-known Ports Registered Ports Dynamic Ports…
Internet Access Technologies
To access Internet, there are different alternatives of different Service Providers. Here, we will focus on these internet access technologies. So, what are these Internet technologies? These are: Digital Subscriber Line (DSL) Cable Internet Mobile Internet Fiber Internet Satellite Internet Now, let’s learn…
Multifactor Authentication (MFA)
What is Multifactor Authentication? As you know password are one of the most used security mechanisms to secure a device. We use different types of password to secure our systems. But passwords are vulnerable to attacks in todays network world. There must be additional security…
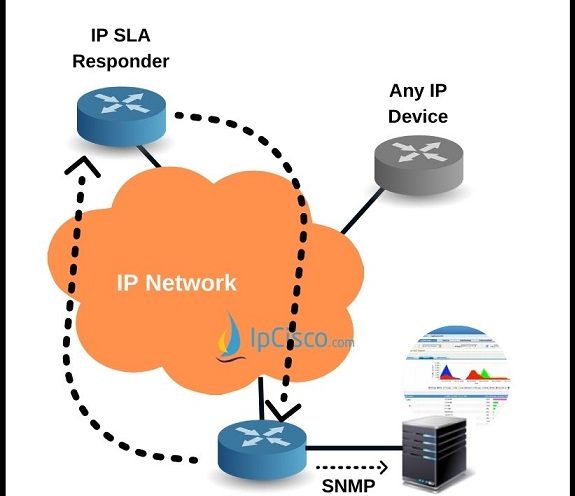
Cisco IP SLA and Configuration
What is Cisco IP SLA? Cisco IP SLA is a network performance analyze concept developed by Cisco. In a network we should give a good performance for our customers. This performance is determined with IP Service Level Agreements (IPSLA). With Cisco IP SLA, the…
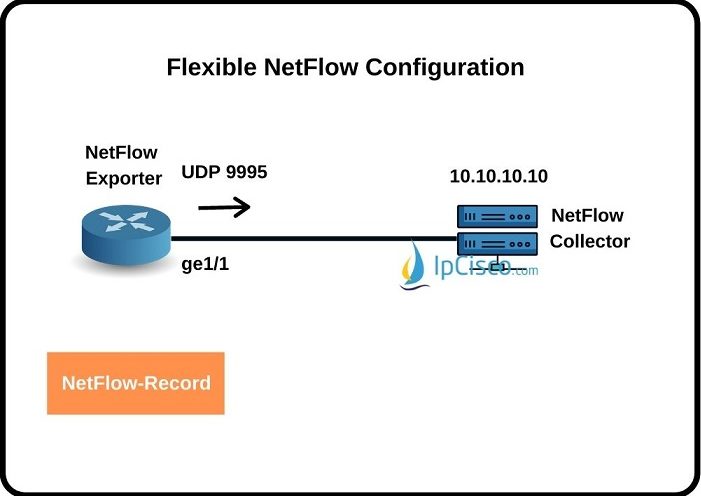
Flexible Netflow Configuration
In this lesson, we will learn how to configure Flexible Netflow on Cisco Routers. We will see Cisco Flexible Netflow Configuration steps one by one with a configuration example. Before, we have also see Traditional NetFlow Configuration on Cisco Routers. To configure Flexible Netflow Cisco,…
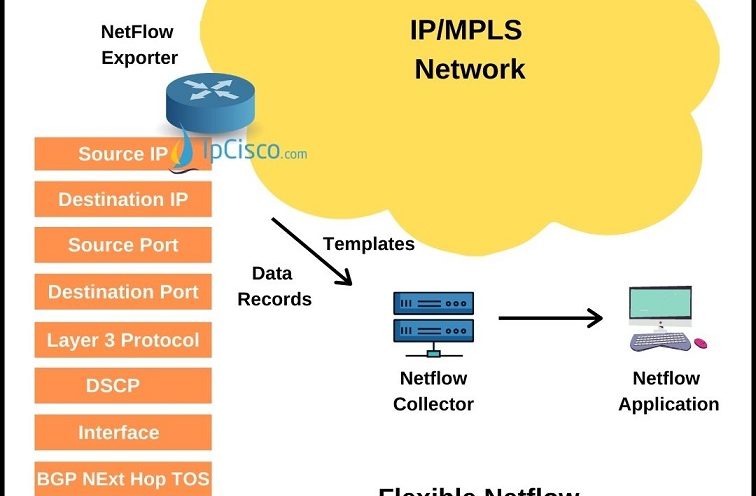
Flexible Netflow
What is Flexible Netflow? NetFlow is a protocol developed by Cisco to monitor and analyze network traffic flows. And now there is an enhanced version. This is Flexible NetFlow. Basically, Flexible NetFlow is an extension of Traditional NetFlow. In other words, it is advanced and next…
Netflow and Netflow Configuration
What is Netflow? In this lesson, we will learn What is NetFlow and we will see Netflow Cisco Configuration. Neflow is a network that is used to monitor the network and to collect ip traffic information. By analyzing your network traffic, Netflow gives you a…
Control Plane Policing (CoPP)
Control Plane Policing (CoPP) is one of the mechanisms used for Control Plane defence against the Network Attacks that is done to the Control Plane. Here, we will focus on what is Control Plane Policing and How to use CoPP. We will also learn How…
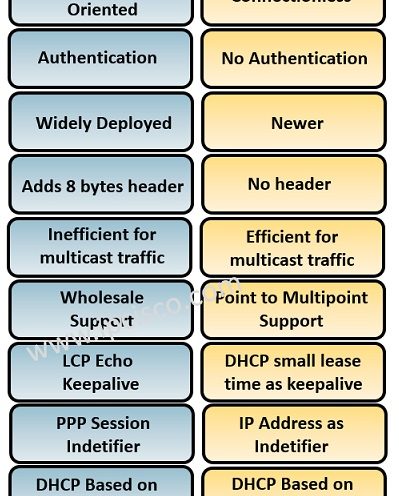
IPoE Overview And IPoE Vs PPPoE
What is IPoE? In this lesson, we will talk about the protocols used in broadband connections. These are PPPoE (Point-to-Point Over Ethernet) and IPoE (IP Over Ethernet). Here, we will mainly focus on IPoE. We will learn what is IPoE and IPoE vs PPPoE. …
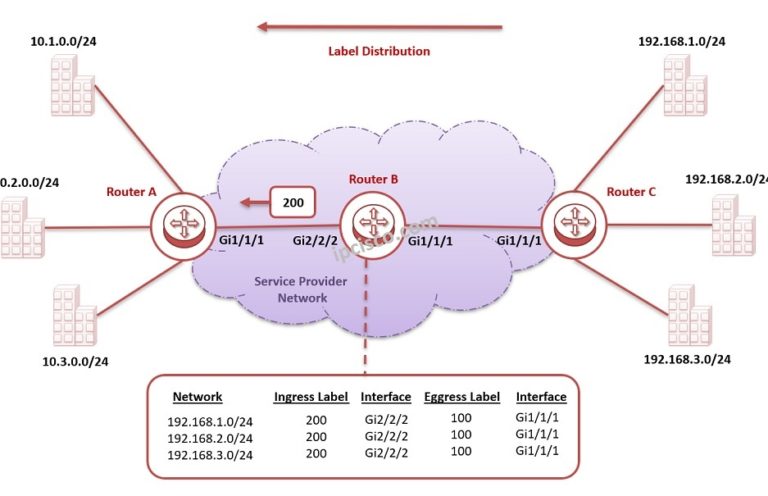
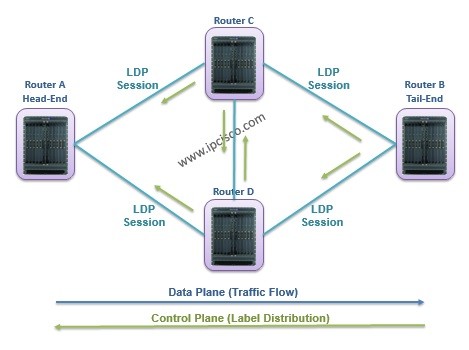
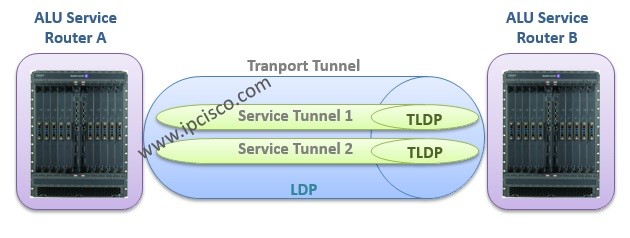
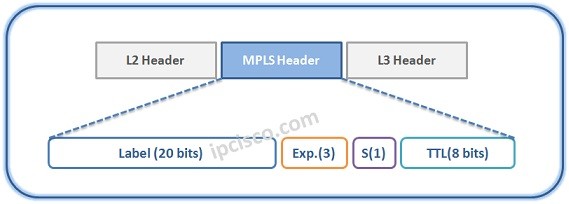
MPSL Label Distribution
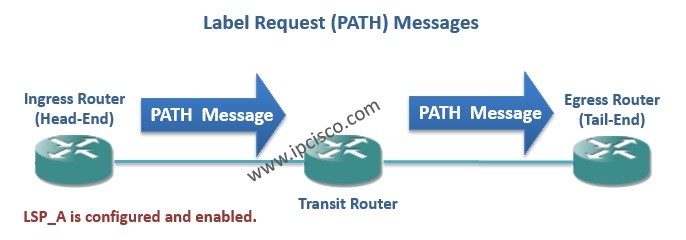
LDP (Label Distribution Protocol) is one of the MPLS Label Distribution protocols that is used for label signaling in MPLS (Multi Protocol Label Switching). So, how LDP works and how is the label distribution done? In this lesson, we will explain these processes detailly with…
Python Nedir?
Python Programlama Dili Bu yazımızda Python nedir sorusuna yanıt arayacağız. Python, 1990 yılında Guido Van Rossum tarafından temelleri atılmış, son yılların en popüler yüksek seviyeli ve nesne yönelimli bir programlama dilidir. İsmi ilk etapta bir yılan türünden alınmış gibi görünse de, Python programlama dilinin…
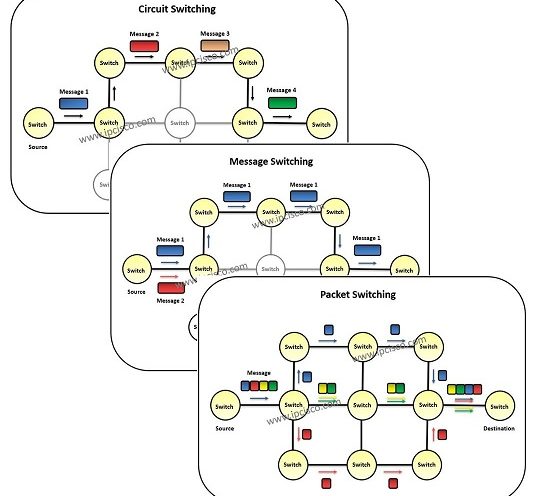
Switching
In this lesson, we will focus on one of the most important lessons of networking. This important lesson is switching. We will learn, what is switching, switching techniques, types of switching and more. Beside we will learn many things about the widely used network equipment,…
Most Popular 3 CCNA Books
CCNA (Cisco Certified Network Associate) is one of the most popular network certifications of the World. It is an entrance certification of Cisco to networking World. To have this popular certification, you should work for Updated CCNA Lessons with any resource and you should pass…
Cyber Security Jobs
Cyber Security is one of the most popular case of today’s information technology World. With the development of the information technology, security attacks has increased and to defend networks and systems towards these attacks, cyber security solutions has also developed. Beside with these solutions, new…
Cyber Security Salary
Cyber Security is a popular area of Information Technology (IT). Especially in recent years, with the development of the technology and by the increase of cyber attacks, cyber security became the most important area of technology. There are many types of hackers and bad guys…
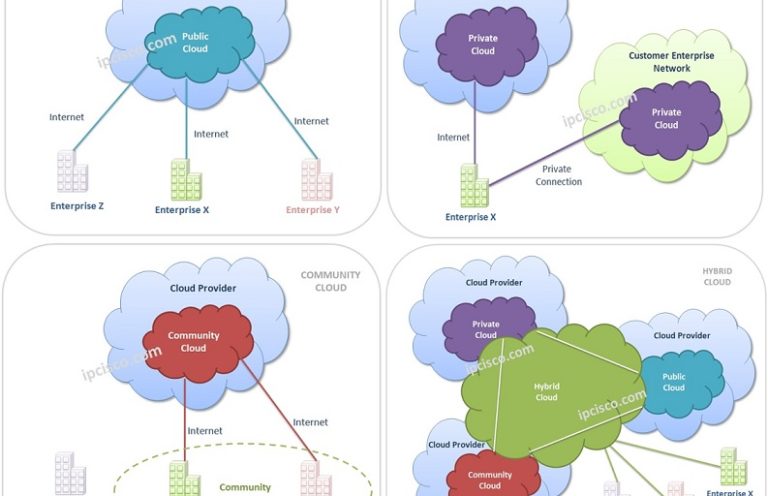
Cloud Computing
What is Cloud Computing? Cloud Computng and Virtualization is one of the new lessons of CCNA 200-301 Course. So What is Cloud Computing? Cloud Computing is the delivery of computing services like networking, storage, servers, software etc. on demand over internet. In this lesson, you…
Cyber Attacks, Network Attacks
Cyber Attacks, Network Attacks, Threats, Vulnerabilitis and Mitigation There are various Network Attacks and various ways to prevent yourself from the attackers. In this lesson we will focus what are these Network Attacks, Cyber Attacks. So, what are the types of Network Attacks (Cyber…
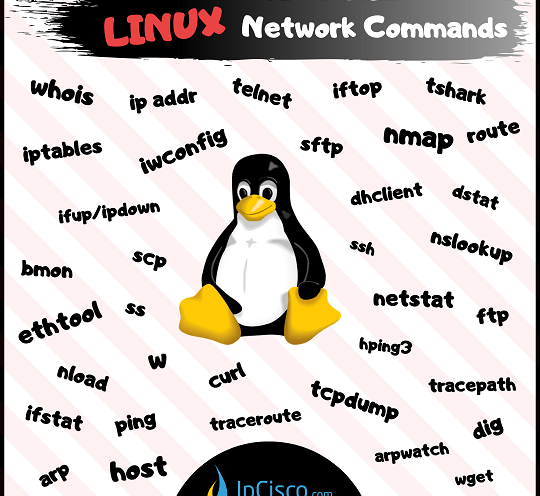
Network Commands in Linux
What Are The Top Network Commands in Linux? Linux is used in the servers as an operation system in many networks. It is the most important and widely used operating system in the World. There are various Linux Commands. Some of these commands are…
What is a Network Protocol?
This is one of the first questions of a Network Engineer: What is a Network Protocol? A Network Protocol is a set of rules, standards, precedures that provide the communication of devices in a network. With all these features, Network Protocols shows how to beahve…
Network Engineer Salary
How much is a network engineer salary? Network Engineering is one of the trend jobs in the World. Large or small, almost all companies has a network part and so they need network engineers. These companies can be large vendors like Cisco, Juniper, Nokia, Huawei,…
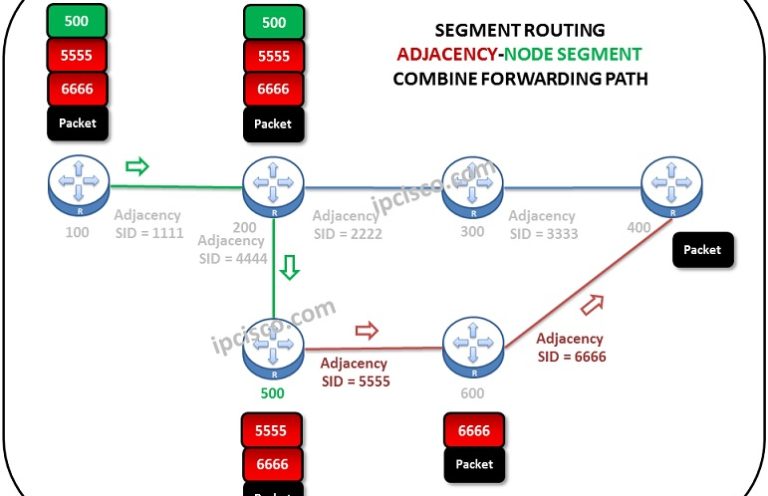
Segment Routing
What is Segment Routing? Network technology is developing day by day. With this development many Technologies are coming to our lives and all these new Technologies need different type of requirements. What are these Technologies? For example, Internet of Things (IoT), 5G, Cloud Services etc.…
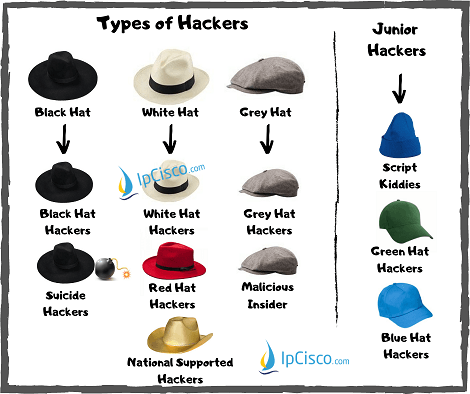
Types of Hackers
A Hacker is a highly skilled person on Cyber Security, Computer Systems and Networks. In other words, they are the Master of Computer World. With such an expertise, a Hacker can do many things on different computers and networks. So, here the important point is…
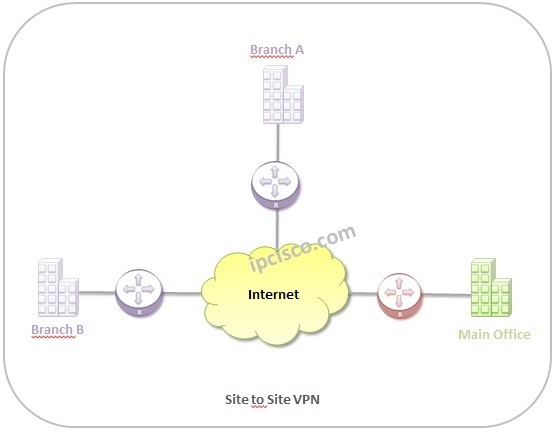
VPN Types and Protocols of VPN
VPN Types VPN (Virtual Private Network) is a technology that provides a secure connection to a private network over Internet for users. By encrypting the connections, VPN provides security in this type communication. Basically this security is provided over a VPN Tunnel and provide…
Cisco DevNet Certifications
Cisco’s New Software Development Certifications : DevNet Cisco has announced its new certification program as “Next Level Certifications”. One of the most important changes in Cisco Certifications with this new program is new Software Developer Certifications, DevNet Certifications. In this article, we will focus on…
Cisco Next Level Certifications
What is new With Cisco Next Level Certifications? Cisco has changed Cisco Certification Suite with a new focus on latest technologies as Cisco Next Level Certifications. There are new technologies that drives today’s technoology professional. With its new Certification Suite, with Cisco Next Level Certifications,…
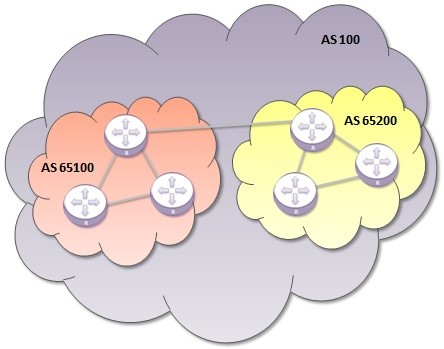
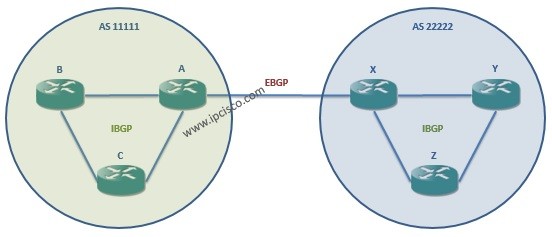
BGP Confederation
What is a BGP Confederation? BGP Confederations is an another mechanism to avoid iBGP Full Mesh topology like Route Reflectors. As a basic definion, BGP Confederaition mechanims is Autonomous Systems (AS) in Autonomous Systems (AS). In other words, in this BGP mechanism, there are…
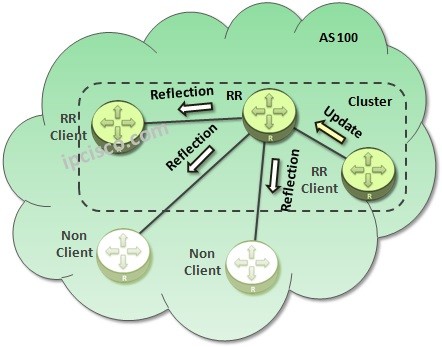
BGP Route Reflector
Why We Use BGP Route Reflectors? By default iBGP Peers need to be Full mesh together. BGP Route Reflector (RR) is a BGP Mechanism used to bypass this iBGP Full Mesh requirement and provide all iBGP Routing information to all iBGP peers. With this…
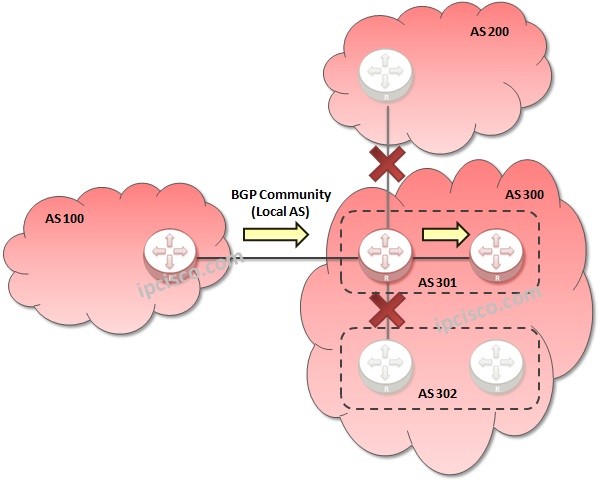
BGP Community
BGP Community Attribute BGP Community Attribute is an Optional Transitive BGP Path Attribute. With BGP Community Attribute, destinations are grouped and BGP route policy decisions are done special to each of these communities. BGP Community Attributes are assigned to specific prefixes and advertised to the…
CCNA Salary
What Does a CCNA Earn in a Month? Network Engineering and Network Technician Jobs are one of the popular Jobs in Information Technology. With the development of Computer Networks this need has increased and many Network Experts are needed for different level Network Jobs.…
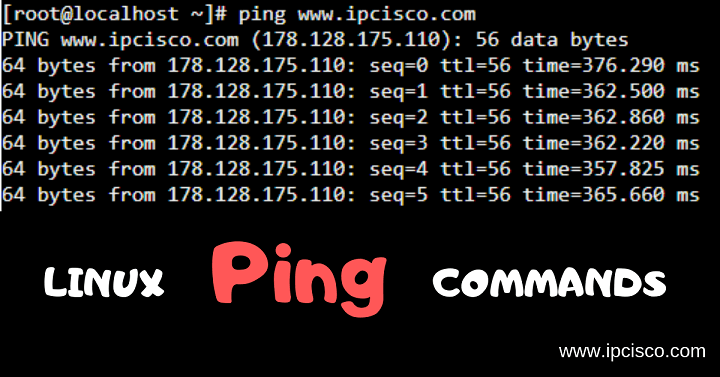
Ping Command in Linux
Ping Command in Linux Ping Command is the most used command in networking world. Maybe it is the first command that every network engineer has used firstly. During network integration, network operation and troubleshooting activities, we use Ping. There are different Linux Ping Commands used…
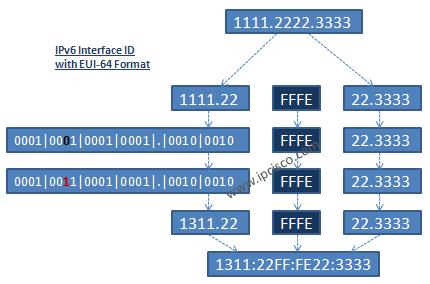
IPv6 Link Local Address
What is IPv6 Link Local Address? IPv6 has different address types. One of the important and widely used IPv6 Address type is IPv6 Link Local Address. Every IPv6 enable interfaces must have a Link-Local Address either with manual configuration or auto-address configuration. IPv6 Link…
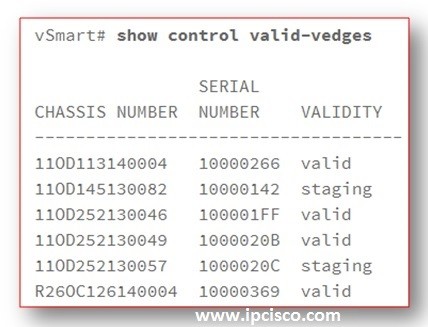
Cisco SD-WAN Verification
Cisco SD WAN Verification Commands In this lesson we will focus on How to Verify Cisco SD WAN Configuration. Here, we will see Cisco SD WAN Architecture vBond Orchestrator, vSmart Controllers, vManage and vEdge SD-WAN devices’ show commands and their outputs. Now, let’s see Cisco…
Cisco vSmart Controller Configuration
How to Configure vSmart Controller? The Virtual Machines that we will use as Cisco (Viptela) vSmart Controller device come with a factory default configuration. We should do the initial configuration of some key parameters on Cisco vSmart Controller. With this initial configuration, our vSmart Controller…
Cisco vBond Initial Configuration
How to Configure vBond Orchestrator? vBond Orchestrator comes with a factory default configuration at the beginning. So, to enroll to the Cisco SD-WAN, it needs to be configured a little. This is the initial configuration of Cisco vBond. After this initial configuration, for full configuration,…
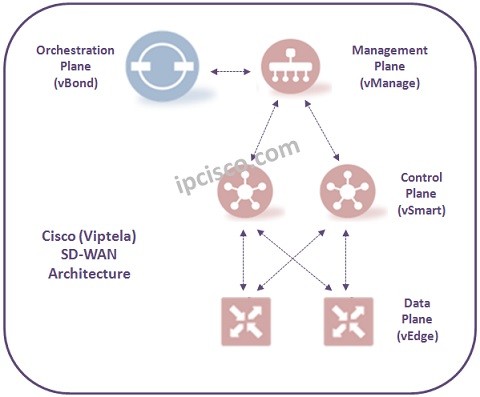
Cisco SD-WAN Components
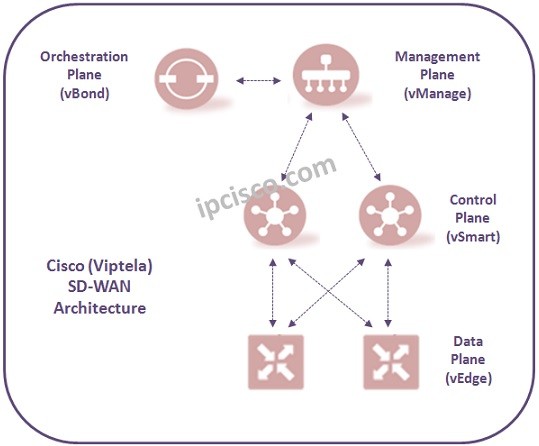
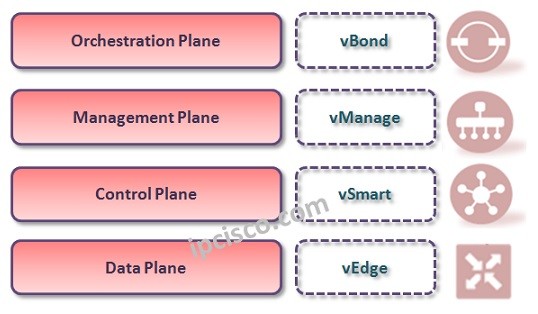
Cisco SD-WAN Components In Cisco SD-WAN Architecture, there are main components work on different SD-WAN Architecture Planes. These SD WAN Components and their location in the SD-WAN Architecture ig given below: vBond vManage vSmart Controller vEdge At 2017, Cisco acquired Viptela. At that…
SD-WAN Architecture
Cisco SD-WAN (Viptela SD-WAN) Architecture In SD-WAN Cisco (formerly SD-WAN Viptela), Cisco SD-WAN Architecture consist of four main SD-WAN Planes. Each of this SD-WAN Planes has specific duty in Cisco SD-WAN Architecture (Formerly Viptela SD-WAN Architecture). These SD-WAN Planes are given below: Orchestration Plane…
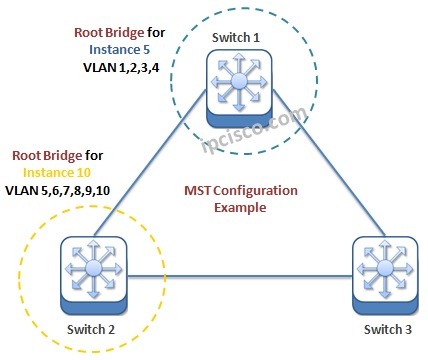
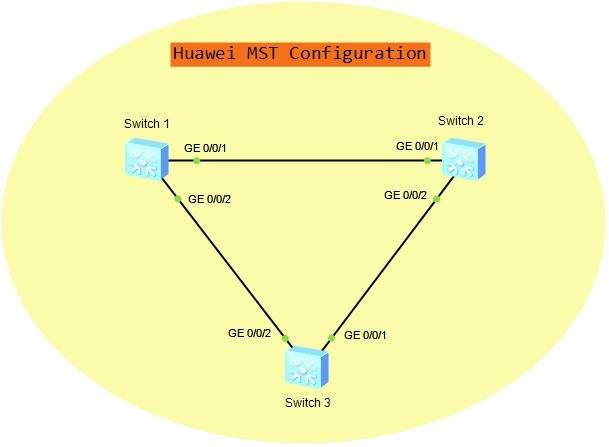
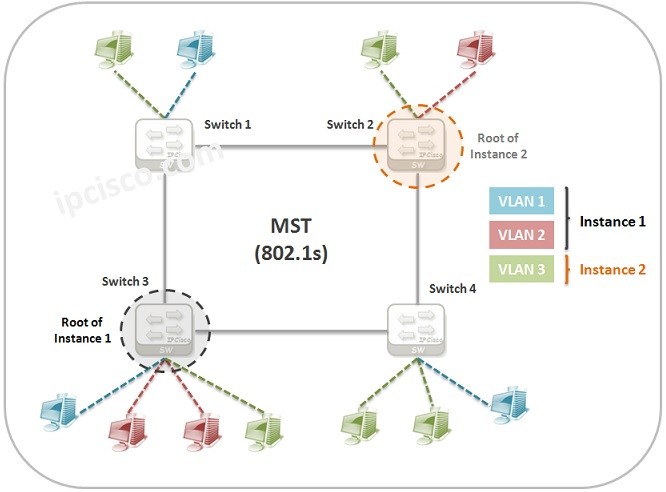
MST Configuration on Cisco
In this configuration example, we will learn How to Configure Spanning-Tree MST Mode on Cisco switches. BEfore, we have leared what is STP and MST. Now, we will learn Cisco MST Configuration. To configure MST (Multiple Spanning Tree), we will use the below topology. Now,…
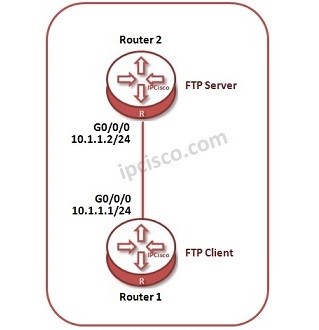
Huawei FTP Configuration
In this Huawei FTP Configuration example, we will configure a router as FTP Server and then we will try to connect this FTP Server router from another router. Here, this another router will be our FTP Client. For our configuration, we will use the…
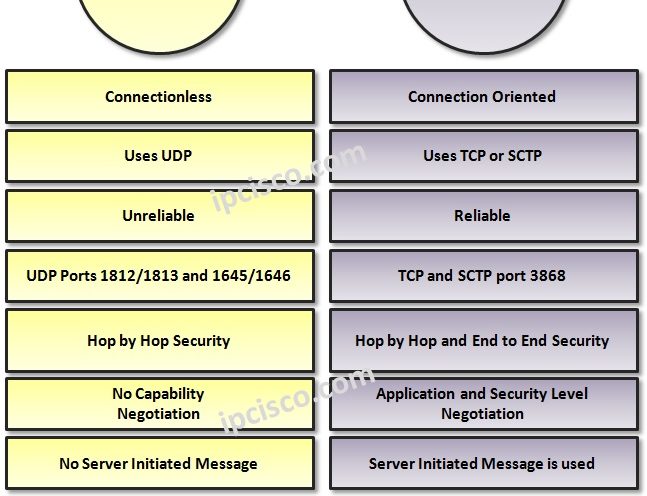
Diameter Protocol Overview
With the development of network world, new requirements has appeared in AAA. For this requirements a new protocol was developed as an enhanced version of RADIUS. This protocol is Diameter Protocol. Here, we will focus on this protocol details and Radius vs Diameter. Diameter…
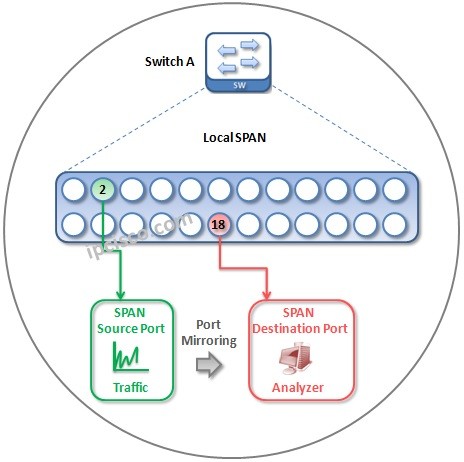
Cisco SPAN Overview
Cisco SPAN Overview SPAN (Local Switched Port Analyzer) is used to monitor specific souce ports’ or specific VLANs traffic, mirror this traffic and then sends the traffic to a destination port on Cisco switches and Cisco routers. SPAN is used generally for troubleshooting and monitoring…
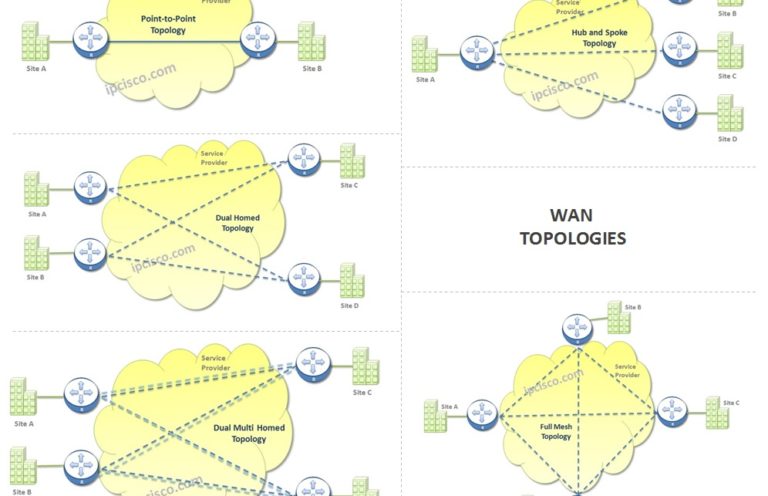
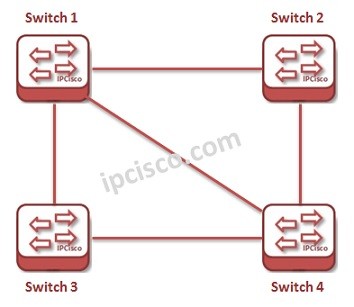
WAN Topology Types
WANs (Wide Area Networks) interconnect different networks over long distances. Various wan topologies used to build a WAN network. In this Cisco CCNA Certification Lesson, we will focus on these main WAN topology types. So, what are these WAN types? The main WAN types…
MSTP Configuration on Huawei eNSP
MSTP is an enchanced STP version. With MSTP, both multiple STP instances can be used and one more VLANs can be added to these instances. In this lesson, we will configure MSTP on Huawei switches with Huawei eNSP. For our Huawei MSTP Configuration Example, we…
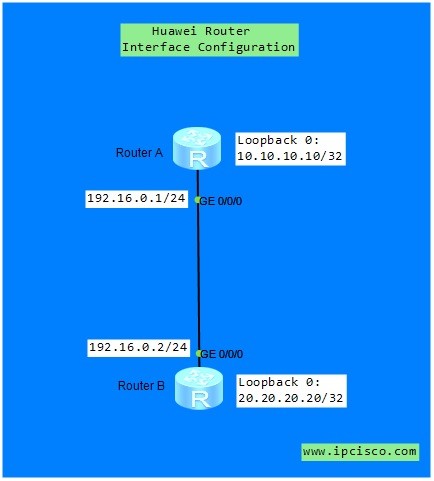
Huawei Router Interface Configuration with eNSP
Huawei Router Interface Configuration Huawei Router Interface Configuration is one of the first configuration that Junior Network Engineers learn on Huawei Routers. Here, we will show how to configure Huawei Router Interfaces with given IP addresses. You can test youself with Huawei HCIA Questions Page.…
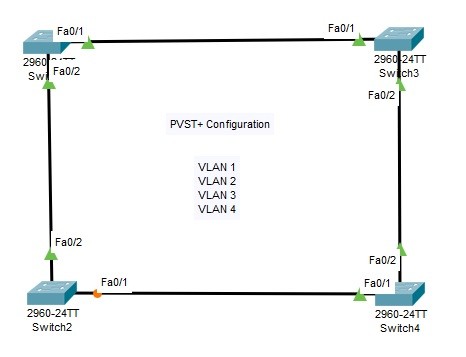
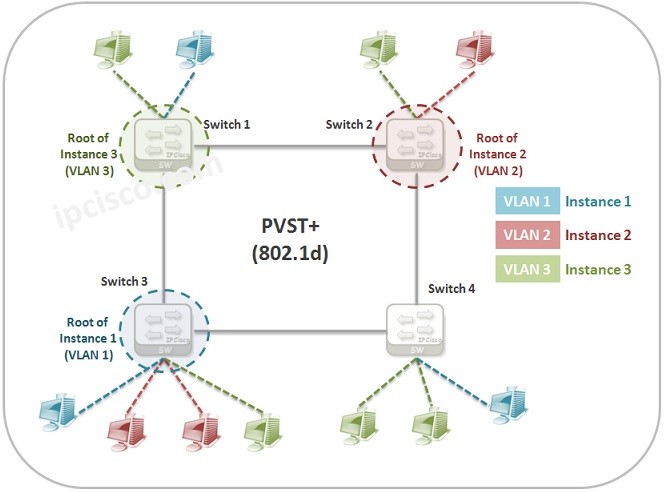
PVST+ and Rapid PVST+Configuration on Packet Tracer
PVST+ Configuration on Packet Tracer In this Spanning Tree Configuration Example, we will configure STP with STP Mode PVST+. As you know, Per VLAN STP Plus is the STP Mode that uses one STP instances per VLAN. For this Configuration Example, we will…
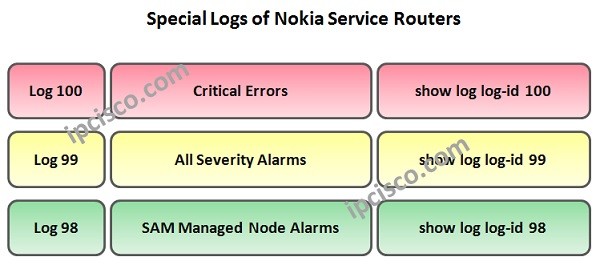
Logs in Nokia Service Routers
Router Logs are very important for a Network Engineer during troubleshooting. A good Network Engineer, check the right logs and determine the required actions according to the logs. All the events, errors , etc are in the logs. If you know where to check, you…
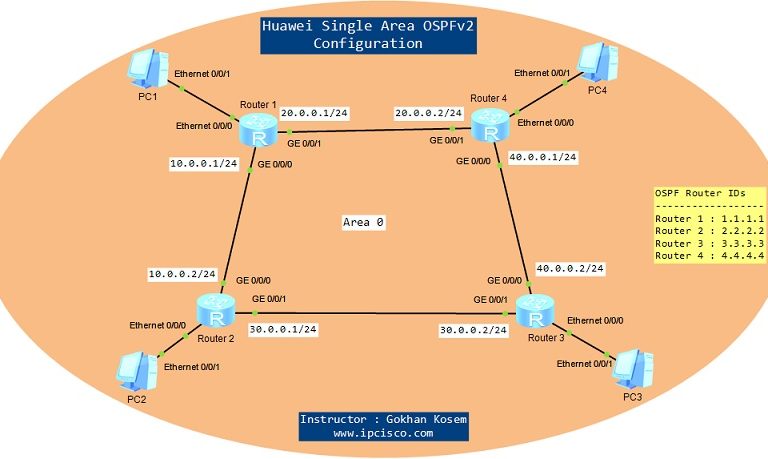
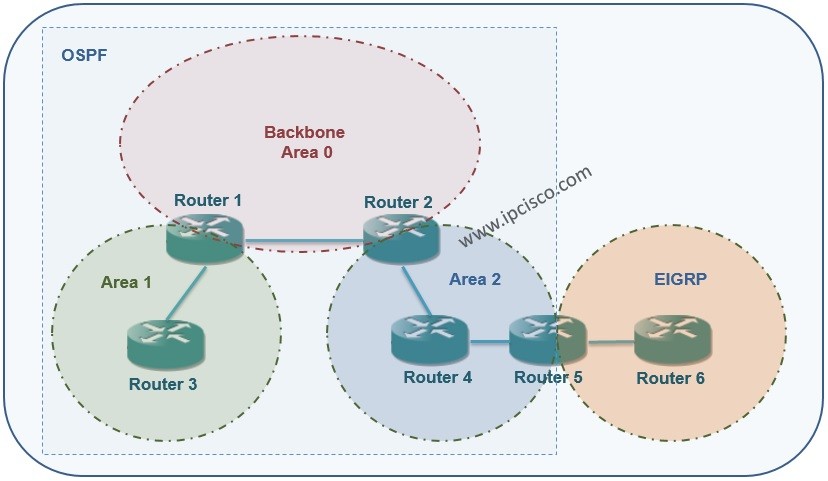
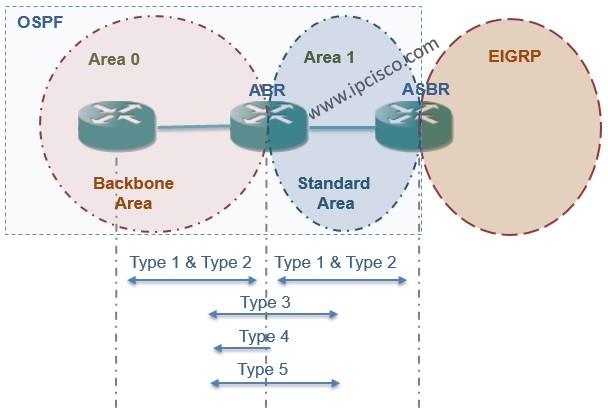
OSPv2 Configuration on Huawei eNSP
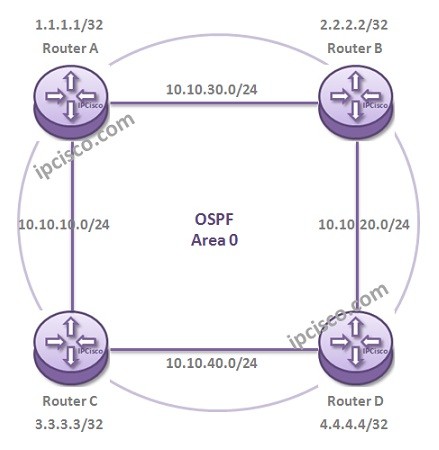
In this OSPF Configuration Example, we will configure OSPFv2 on Huawei Routers. We will use eNSP for our Huawei OSPFv2 Configuration Example and our topology will be like below. Here, we will configure only one area, Area 0. So, this is a single Area OSPF…
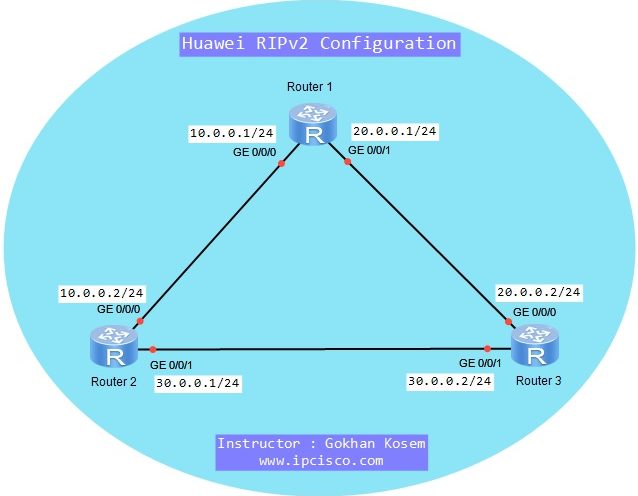
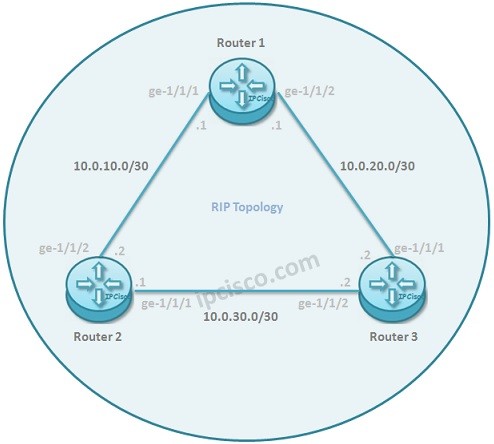
RIPv2 Configuration on Huawei eNSP
RIPv2 is an old Routing Protocol but it is the first Routing Protocol that all Network Engineers meet first. In this lesson, we will configure RIPv2 on Huawei Routers. For our Huawei RIPv2 Configuration Example, we will use the below topology consist of three routers.…
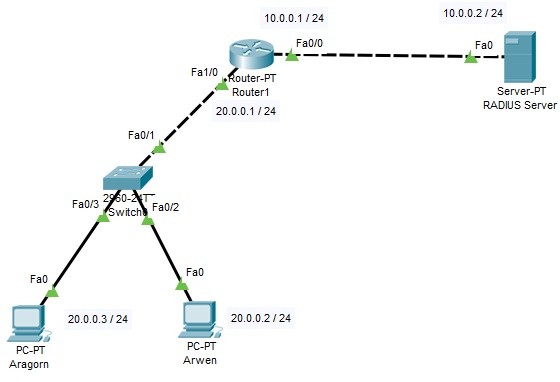
RADIUS Configuration on Packet Tracer
In this RADIUS Configuration Example, we will configure RADIUS Server and a Cisco Router for RADIUS Authentication, for the users connected to the router via Cisco switch. For out RADIUS Configuration Example, we will use the below topology on Cisco Packet Tracer. How…
MST (Multiple Spanning Tree)
MST Overview MST (Multiple Spanning Tree) is the version of STP that allows multiple VLANs to a single instance. It is the standard based protocol defined with IEEE 802.1s.You can also check the definion of wiki for MST. In normal STP (CST) and RSTP,…
PVST+ and Rapid PVST+
PVST+ (Per VLAN Spanning Tree Plus) PVST+ (Per VLAN Spanning Tree Plus) is a Cisco proprietary STP version. It is also the default STP version for Cisco devices. It is the standard named 802.1d. In another lesson, we will see the configuration of PVST+ on…
MLPPP Configuration on Cisco Packet Tracer
Packet Tracer MLPPP Configuration Example In whe previous lesson, we have learned what is MLPPP. Here, we will focus on how to configure MLPPP. In this MLPPP Configuration example, we will use the below simple topology. We will configure MLPPP on both of the routers…
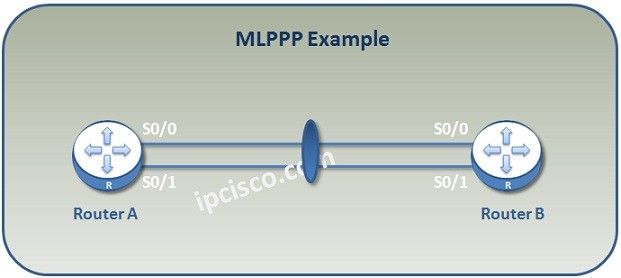
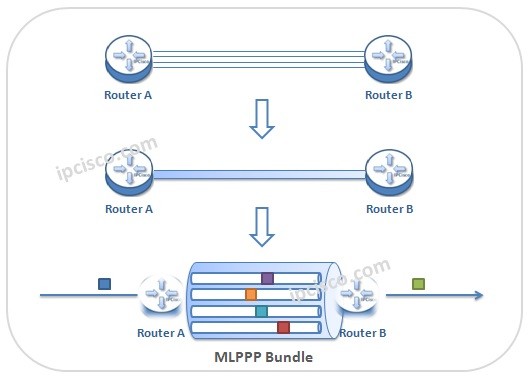
What is MLPPP?
What is MLPPP? MLPPP (Multilink Point-to-Point Protocol) is the protocol that bundles multiple serial wan links into a one Logical Bundle. As a name, PPP Multilink, MLP and MP are also used for MLPPP (Multilink Point-to-Point Protocol). Here, we will learn the theorical parts, to…
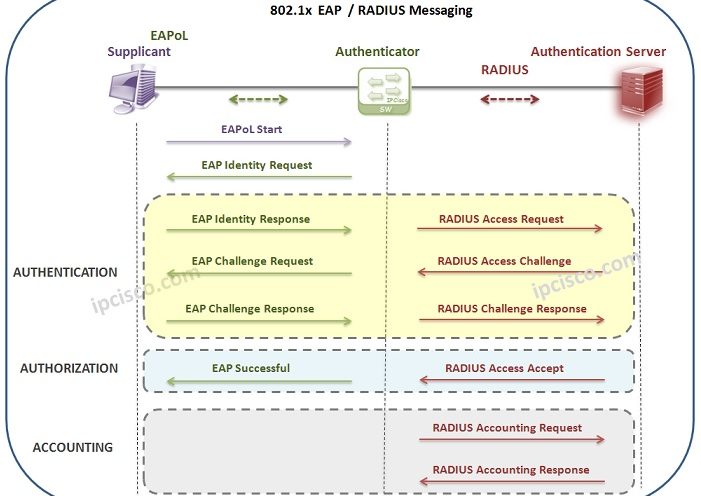
EAPoL (Extensible Authentication Protocol over LAN)
EAPoL is the abbreviation of Extensible Authentication Protocol over LAN. EAPoL (Extensible Authentication Protocol over LAN) is a network authentication protocol used in 802.1x (Port Based Natwork Access Control). In other words, it is the encapsulation protocol used between Supplicant and Authenticator. As we…
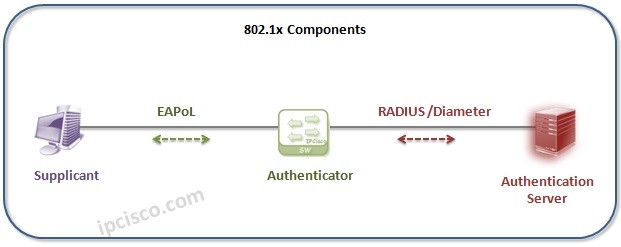
802.1x (Port Based Network Access Control)
802.1x (Port Based Network Access Control) 802.1x is a LAN Security Mechanism that provides port based access control in the network devices. In 802.1x mechanism, devices needs to be authenticated before accessing the network. 802.1x Roles In 802.1x mechanism, there are three roles.These 802.1x roles…
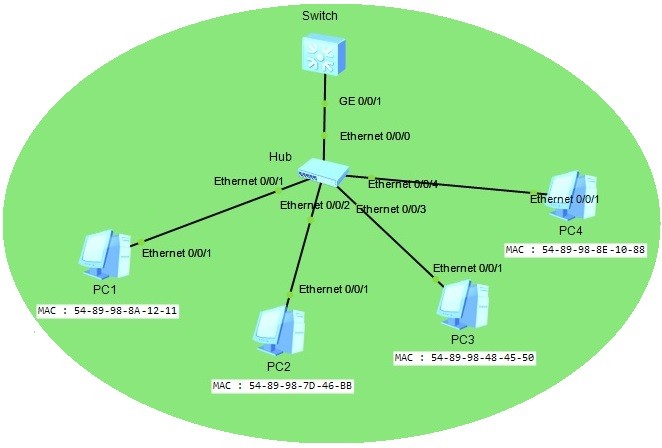
Huawei Port Security Configuration on Huawei eNSP
In this Huawei Port Security Configuration Example, we will configure Port Security on a Huawei switch. For our Huawei Port Security Configuration, we will use the below topology consist of one switch, one hub and four PCs. You can also view Cisco Port Security Configuıration…
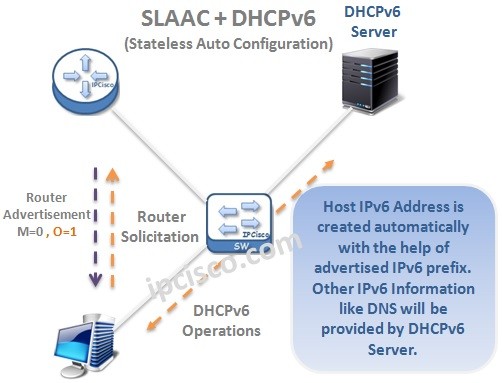
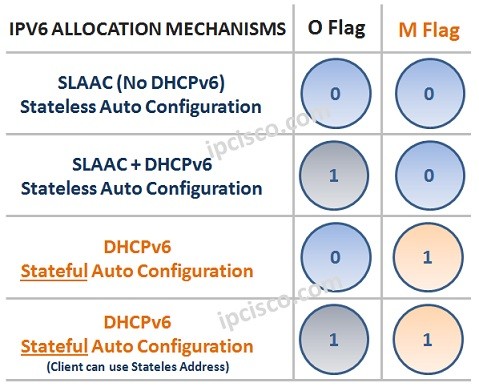
Stateless Address Auto Configuration (SLAAC)
Stateless Address Auto Configuration (SLAAC) is the IPv6 Auto Configuration technique that is done automatically on the hosts with the help of IP Prefixes coming from a router with Router Advertisements (RAs). In this type of Auto configuration, in Stateless Auto Address Configuration there is…
DHCPv6 Overview
Dynamic Host Configuration Protocol version 6 IP Allocation can be done with different mechanims in IPv6. Mainly, we can devide IPv6 Allocation mechanims into two. These are: • Manual • Dynamic Manual IP allocation is the way that network engineers manually assign IPv6 addresses. Dynamic…
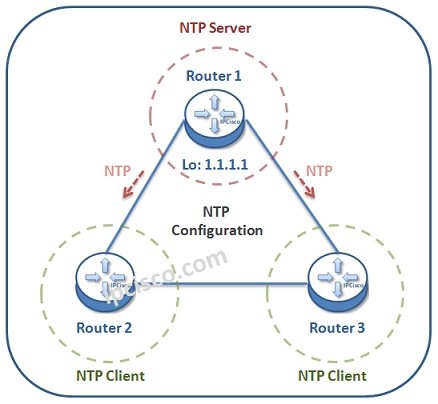
Cisco NTP Configuration
How to Configure NTP on Cisco? NTP is the aberviation of Network Time Protocol used to set time related configurations on network devices. In Cisco devices, NTP Configuration is done with a little various NTP commands. In this example, we will see how to configure…
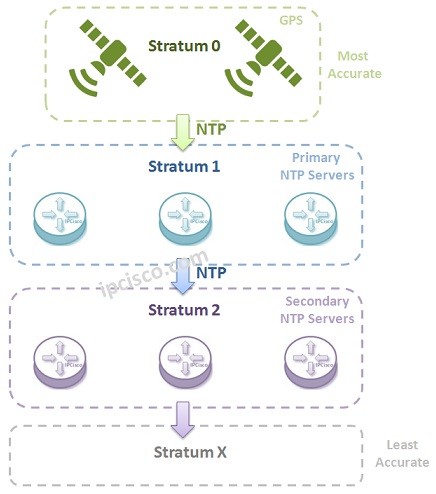
NTP (Network Time Protocol)
NTP Overview The time on the network devices are very important. In a network all the devices’ times need to be synronized. Using the same time on all the devices in network is especially very important for troubleshooting activities. This time synronization is done by…
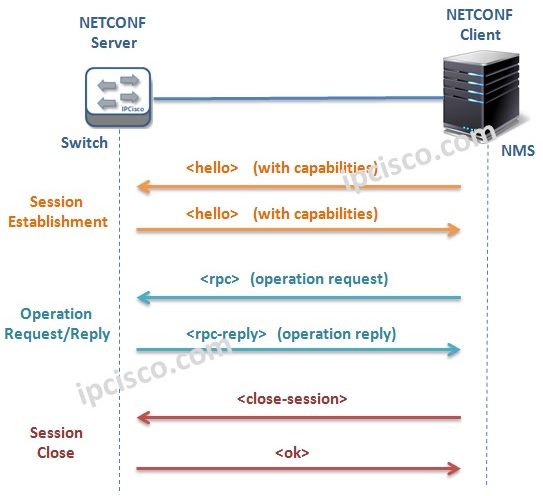
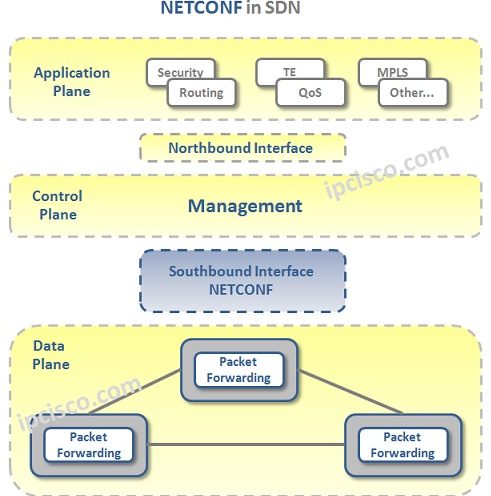
NETCONF Operation Steps
NETCONF Operations NETCONF Operation has three common steps. These steps are: • Session Establishment • Operation Request and Reply • Session Close Firstly, the Session is Established with the messages. Both NETCONF Client and NETCONF Server send message with their capabilities, what operations they support.…
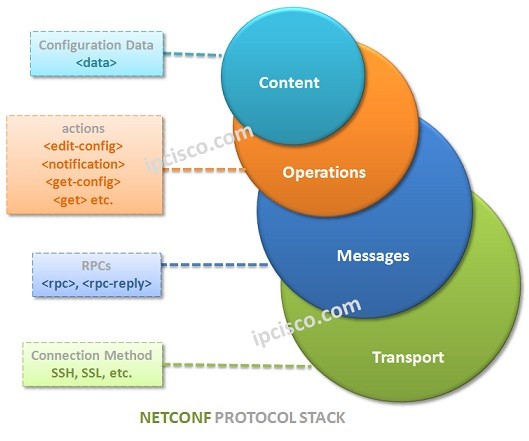
NETCONF Protocol Stack
NETCONF Protocol Stack consist of four main layers. These NETCONF Protocol Stack are: • Content • Operations • Messages • Transport At the Content Layer, YANG Modeling is used fo data modeling and protocol operations. The configuration for a NETCONF operation is XML based and…
NETCONF Overview
Network Configuration Protocol (NETCONF) is a standard based IETF Network Configuration Management Protocol. With this Network Configuration Management Protocol, we can install, modify and remove the configuration of the network devices. Additionally, NETCONF Protocol reduces the cost. It also reduces the given time to the…
MLD Configuration on Huawei Routers
In this lesson we will give an example topology consist of Huawei switches and multicast hosts and then we will configure MLD on these devices. For our example, we will use the below topology: Let’s configure MLD on the Switch 1. Enabling IPv6 Multicast Firstly,…
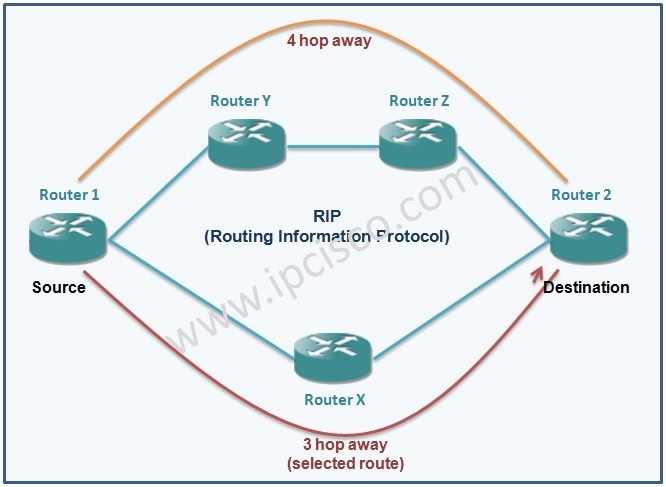
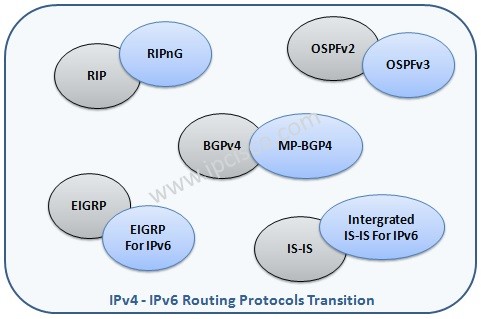
Dynamic Routing Protocol Types
Dynamic Routing Protocol Dynamic Routing is the routing process that is done via a Routing Protocols in networking. The Routing Protocols that is used for this aim is also called Dynamic Routing Protocols. In this lessons, we will focus on the types of Routing…
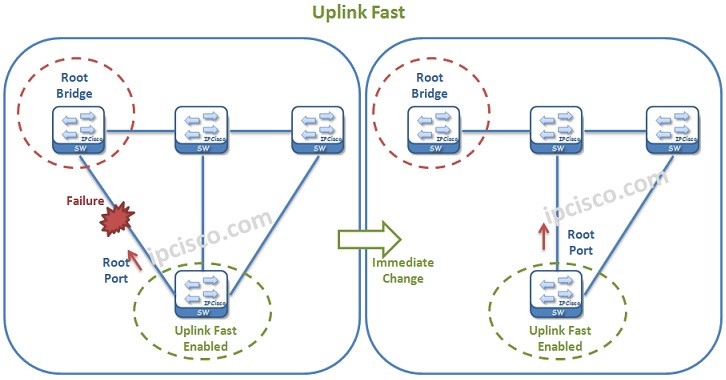
STP Convergence Mechanisms - Part 2
Loop Guard, Uplink Fast, Backbone Fast and UDLD In this lesson, we will learn other STP Convergence Mechanisms; Loop Guard, Uplink Fast, Backbone Fast and UDLD. Now, let's learn each of these mechanisms and their roles one by one. Loop Guard Loop…
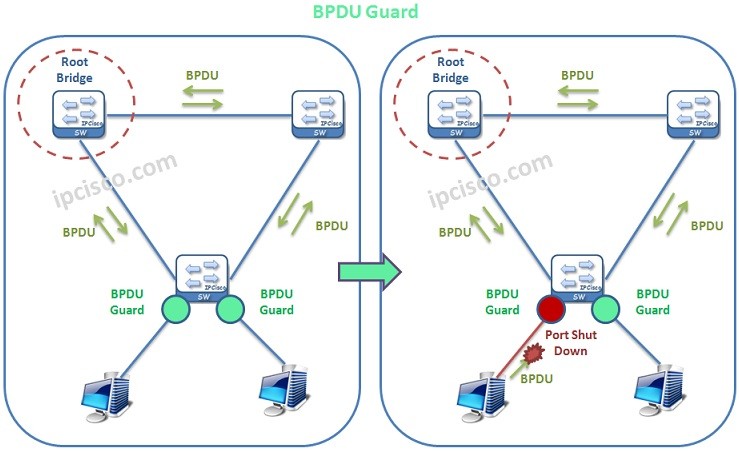
STP Convergence Mechanisms - Part 1
Portfast, Root Guard, BPDU Filter and BPDU Guard The are various mechanims used with STP to provide stable STP topology. In this lesson, we will focus on what are these STP Mechanims and what they do to provide a stable STP Topology. So,…
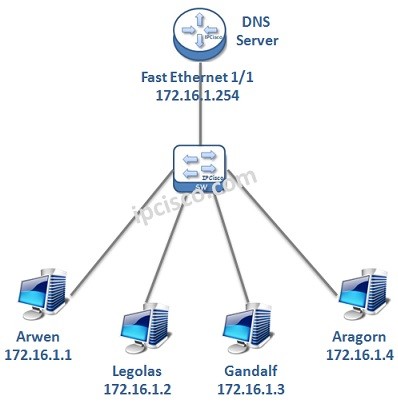
DNS Configuration on Cisco Routers
How to Configure DNS on Cisco Routers? To use DNS, firstly, we must configure a DNS Server. In a network, we can confgiure a router as a Domain Name System Server. In this lesson, we will talk about Cisco DNS Server Configuration, we will…
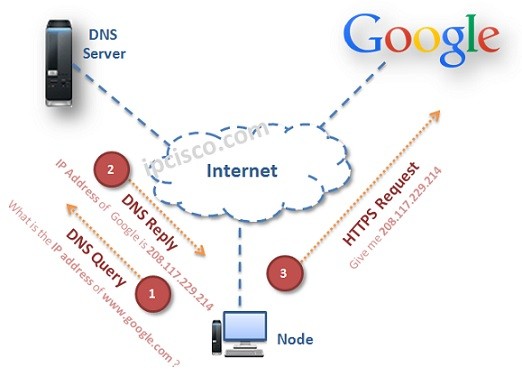
Domain Name System Overview
DNS Overview DNS (Domain Name System) is a common protocol that is used to translate hostnames to the IP addresses. Normally, we use website addresses on our browsers. These website addresses are resolved to IP addresses by DNS. Without DNS, we could not reach this…
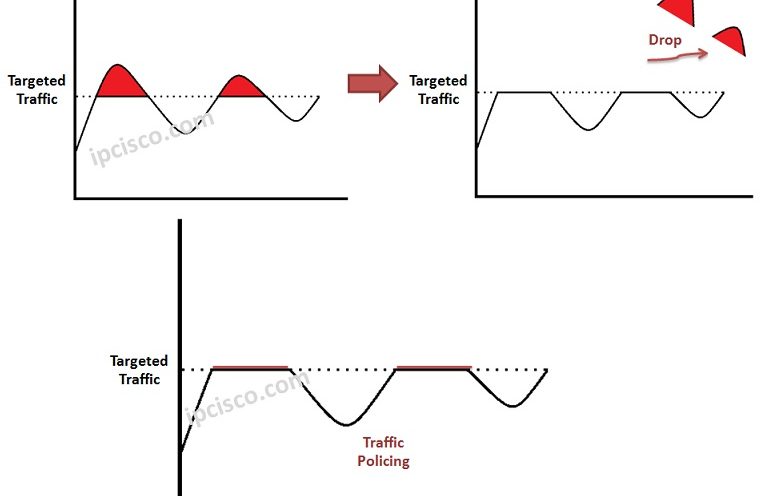
Policing and Shaping in QoS
In networks, the traffic increses for a variety of reasons. Some Quality of Service Adjustments are done to handle this increases. During these increases, if the capacity of the link is exceeded, then the traffic on this link is dropped. Without any arrangement, this drop…
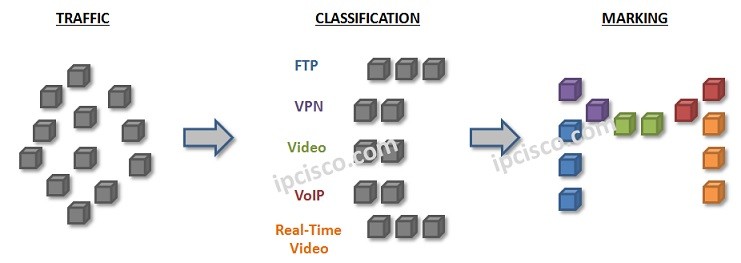
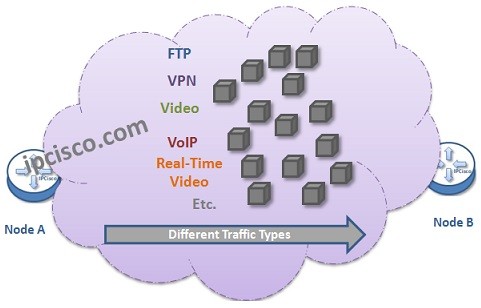
Classification and Marking in QoS
To use Quality of Service for a traffic, firstly traffic need to be identified. With this identification, traffic types are classified and then they are marked with an understandable way by the network. This process is basically called "QoS Classification and Marking". Another important mechanisms…
Quality of Service Overview
What Does QoS Stand For? This is th most ask questions by Network Engineers, especially the Newbies, What Does QoS Stand For?QoS (Quality of Service) is the general name of a concept , which is used to optimize networks with different priority levels to different…
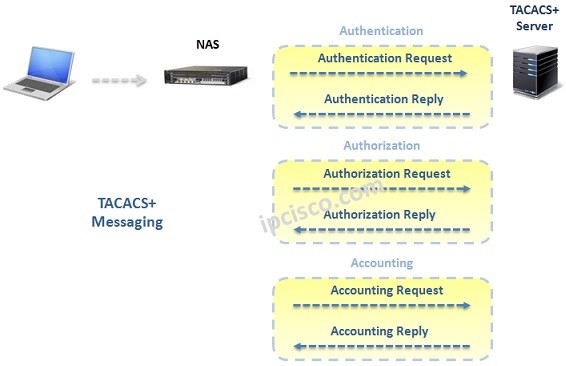
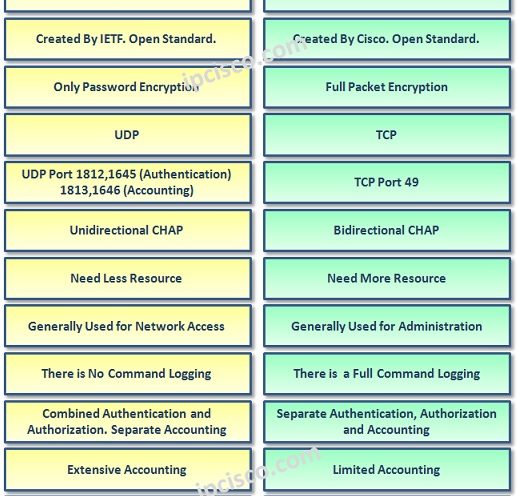
TACACS+ Overview
What is TACACS+? TACACS+ (Terminal Access Controller Access-Control System) is a AAA protocol that is developed by Cisco. After a while TACACS+ has became a standard protocol that is supported by all vendors. There is also another standard protocol called RADIUS. If you would like…
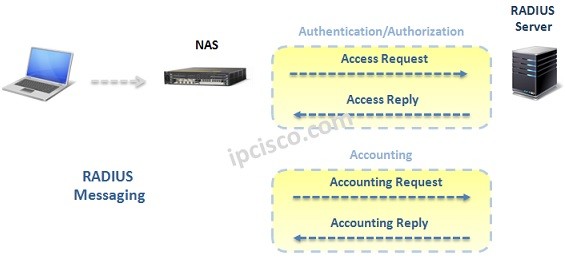
RADIUS Overview
What is RADIUS? RADIUS (Remote Access Dial-In User Service), RADIUS Protocol is a AAA (Authentication, Authorization, Accounting) protocol that is developed by IETF. RADIUS is a standard base AAA Protocol supported by all vendors. Mainly, the job of RADIUS is providing Secure Network Access. RADIUS…
AAA Protocols : RADIUS and TACACS+
TACACS versus RADIUS Networks need to be protected against any unknown access. In other words, network administrators need to control the users that can access to the network. They need to check who they are, what are they allowed for and what did they do.…
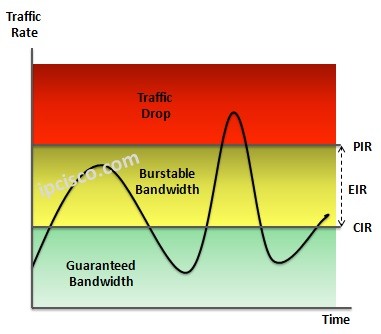
What is CIR and PIR?
In Metro Ethernet links, the traffic rates are not stable always. Sometimes the traffic rates increase, sometimes they decrease. To overcome and manage this issue, some key parameters are used. This parameters provide to determine guaranteed (without loss) traffic rates, burst traffic rates and drop…
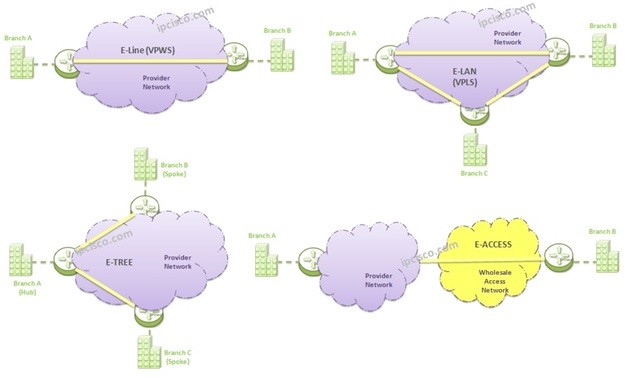
Metro Ethernet
Metro Ethernet Metro Ethernet Overview Simply, Metro Ethernet is an enhanced version of Ethernet that is used between long distances with higher bandwidths. Metro Ethernet can be used both by companies to connect their sites and by end users to connect Internet. Ethernet is a…
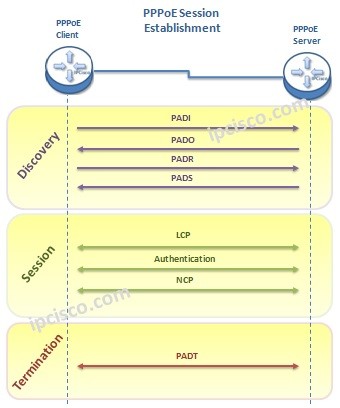
Point-to-Point Protocol over Ethernet (PPPoE)
What is PPPoE? Point-to-Point Protocol over Ethernet (PPPoE) is a network protocol which encapsulates PPP frames inside Ethernet. With PPPoE, multiple hosts in an Ethernet LAN are connected to the Provider Network and throughout this network, they connect Internet. Here, this connection is done over…
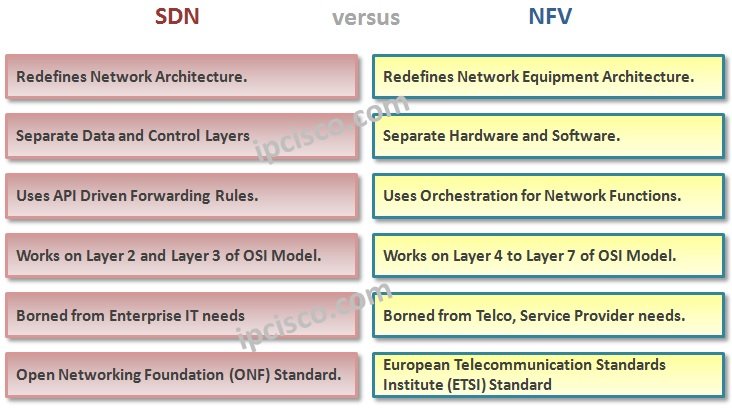
NFV and SDN
NFV and SDN are two important concepts for today’s and future network. So, why are they used together? To understand this, let’s firtly look at their main benefits. SDN (Sotware-Defined Networking), • Offer a new architecture by decoupling Control Plane and Data Plane • Add…
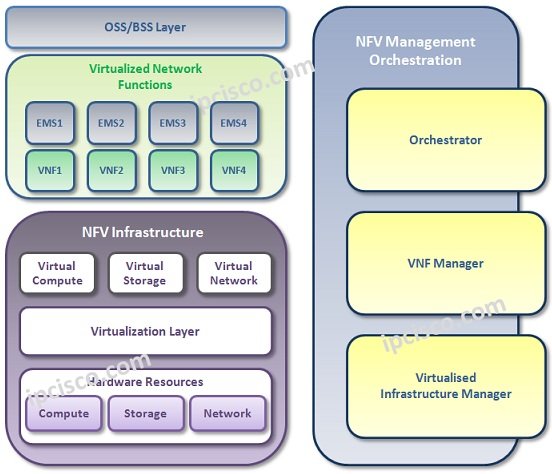
NFV Infrastructure
Network Functions Virtualization (NFV) system consists of three key Infrastructure elements. These elements are: • NFVI (Network Functions Virtualization Infrastructure) • VNFs (Virtual Network Functions) • MANO (Management and Orchestration) Let’s talk about each of these elements one by one. NFVI (Network Functions Virtualization Infrastructure)…
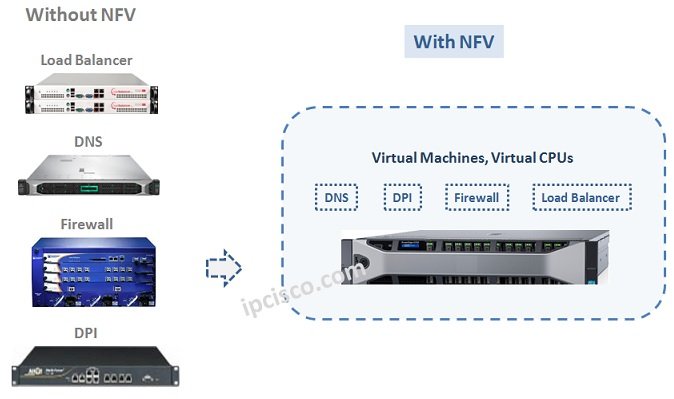
NFV Overview
Basically, Network Function Virtualization (NFV) is a network concept that replaces specialized hardwares (routers, firewalls, load balancers etc) used in classical network architecture with softwares running on servers that does the same jobs. NFV was defined at 2012 by a group named Industry Specification Group…
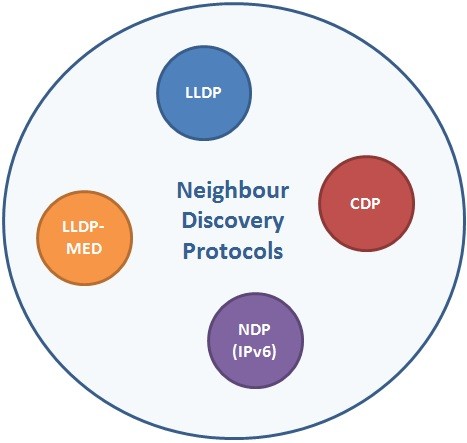
IPv6 NDP (Neighbour Discovery Protocol)
What is IPv6 NDP? IPv6 NDP (Neighbor Discovery Protocol) is the Protocol that provide Network Nodes’ Discovery as its name implies. In the IPv4 World, we were using ARP, but in IPv6 world there is no ARP. Instead, ICMP based NDP is used for Neighbor…
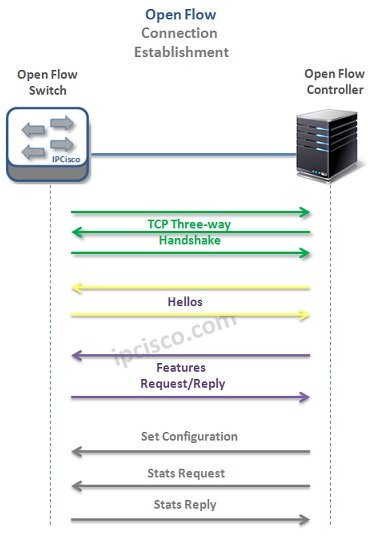
Open Flow Messages
Open Flow Control Messages are based on TCP. To set up Open Flow communication, Open Flow Controller listens TCP ports 6633/6653. There are five main parts in Open Flow Messages. These are given below: • Version • Type • Message Lenght • Transaction ID (A…
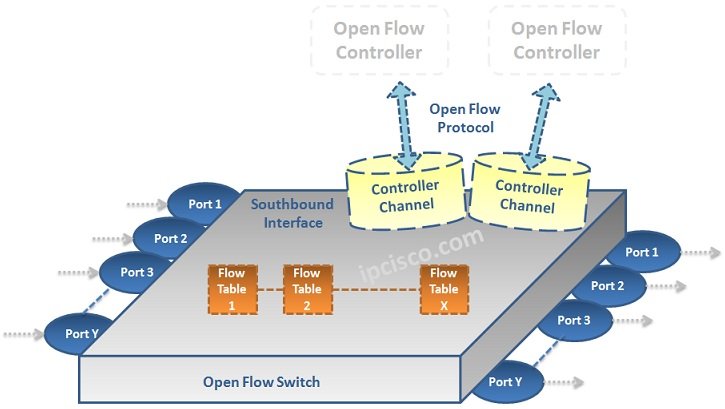
Open Flow Components
There are two main components used with Open Flow. These are: • Open Flow Switches • Open Flow Controllers Open Flow Switches Open Flow provide the seperation of Control Plane and Data Plane. Open Flow Switches are used in Data Plane Section. Open Flow Switches…
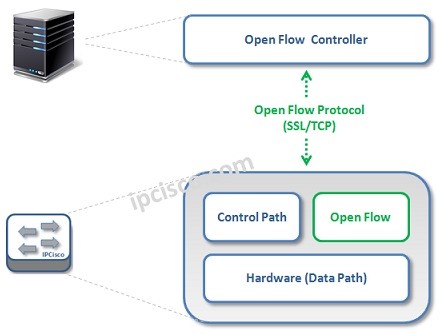
Open Flow Overview
Open Flow is a Standard based Layer 2 Communication protocol used between Controller and Switch in SDN. It allows to access to the Forwarding Plane of the network devices. OpenFlow was standardised by a non-profit consortium, Open Networking Foundation (ONF) that has many network vendors…
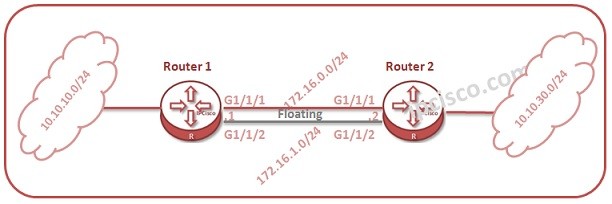
Floating Static Route and Default Route Configuration
In this HCIA (HCNA) lesson we will focus on Huawei Floating Static Route and Default Route on Huawe Routers. We will give examples for How to configure Huawei Floating Static Route Configuration and Default Route Configuration. Let's start. You can test youself with Huawei…
Huawei Static Routing and Load Balancing
Huawei Static Routing Static Route is a manual simple route configuration. In Huawei Routers, Static Routing is similar to the other platforms like Cisco Static Routing, Nokia Static Routing etc. The concept is simple: Write “ip static route” Add “the Destination IP and…
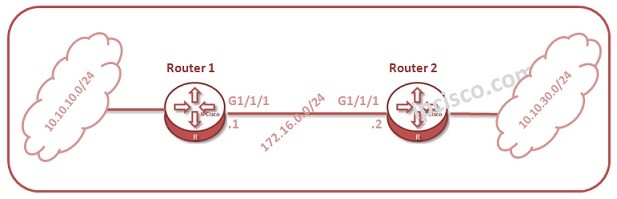
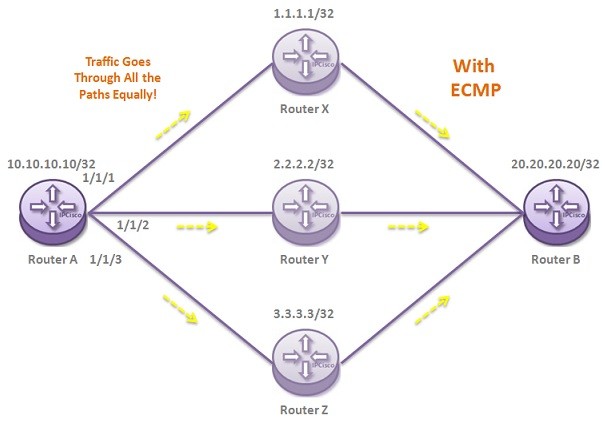
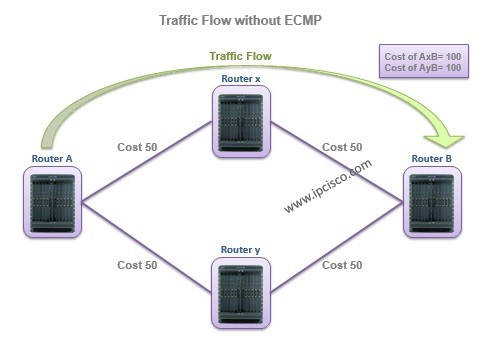
ECMP Configuration on Nokia Routers
In this lesson, we will talk about ECMP (Equal Cost Multipath) Configuration on Nokia Routers. To explaint ECMP better, we will use the below MPLS Topology. As you can see, from Router A to Router B, there are three different ways. Normally, without ECMP, the…
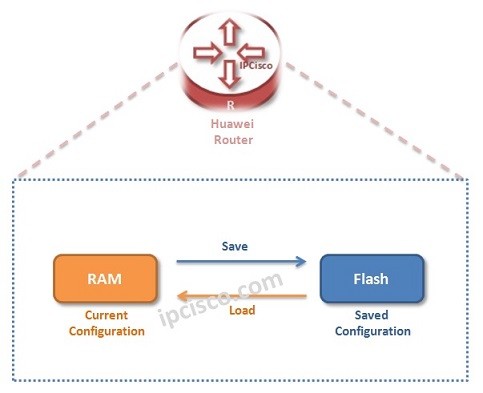
Huawei VRP (Versatile Routing Platform)
What is Huawei VRP (Versatile Routing Platform) Huawei VRP Overview VRP (Versatile Routing Platform) is the Operating System that many Huawei devices operate. This is like Cisco’s IOS, Nokia's (Alcatel-Lucent’s) TiMOS and Juniper’s JUNOS. There is only one difference. There is no “OS” at the…
Huawei Router File System
In all network device, there is a File System. In Huawei routers and switches there is also a File System. File System stores many important files for the system like sytem files, configuration files, software upgrades etc. File System Commands Almost everyone has used window…
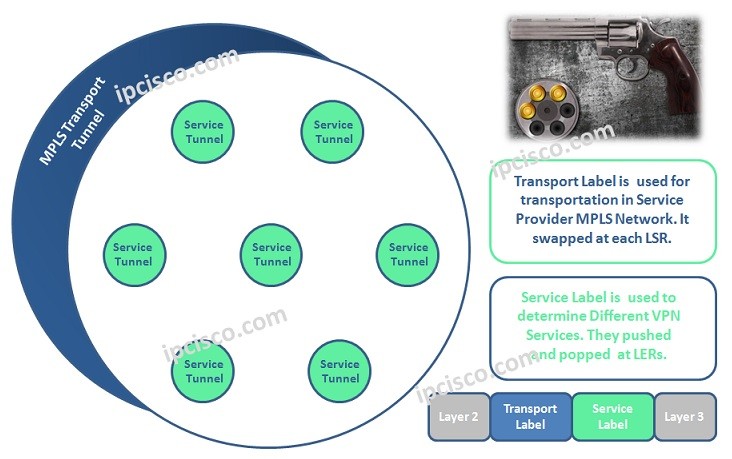
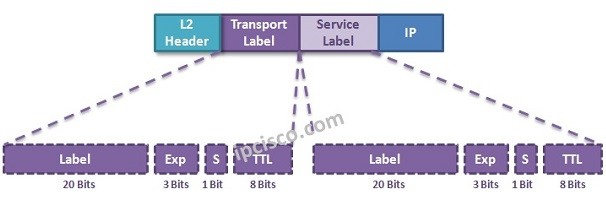
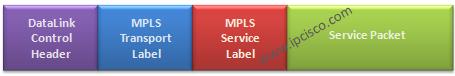
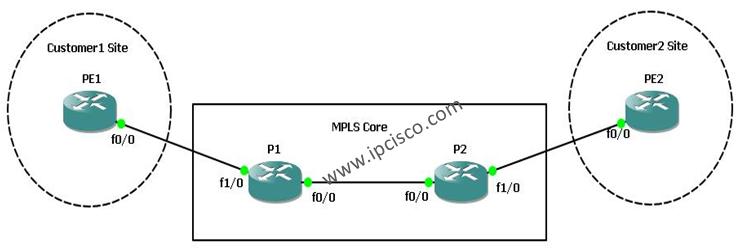
MPLS VPN Labelling
MPLS mechanims uses two types MPLS Label to accomplish MPLS VPN Services. These are the two tunnel mechanims in MPLS mechnism. A Tunnel and many sub service tunnels in it. Two types MPLS Labels that are used in MPLS VPN Services are : • Transport…
MPLS Label Switching
MPLS Technology uses different routers for different roles. There are some common router types that are in these roles. The names of these routers are changing in different vendor naming, but the main role is same. These common routers are given below: • C (Customer…
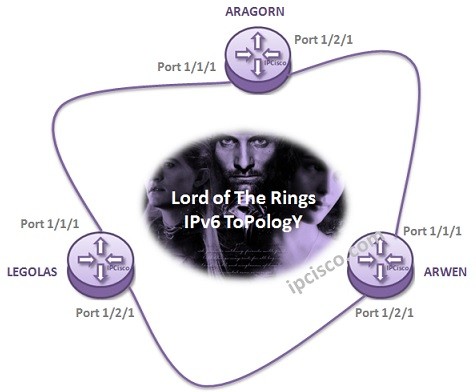
IPv6 Configuration on Nokia Routers
In this Nokia Configuration Example, we will see IPv6 Configuration on Nokia Routers (Formerly Alcatel-Lcuent Routers). For this simple IPv6 Address configuration example, we will use the below Lord of The Rings Topology : ) To compare with Juniper IPv6 Configuration, you can also check…
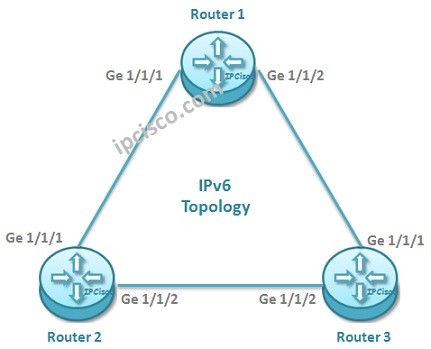
IPv6 Configuration on Juniper
In this configuration example, we will configure IPv6 on Juniper Routers. For our Juniper IPv6 Configuration Example, we will use the below IPv6 Topology. For our Juniper IPv6 Configuration Example, we will use the below IPv6 Addresses. Router 1 Interface Ge 1/1/1 2001:aaaa::1/64 (To Router…
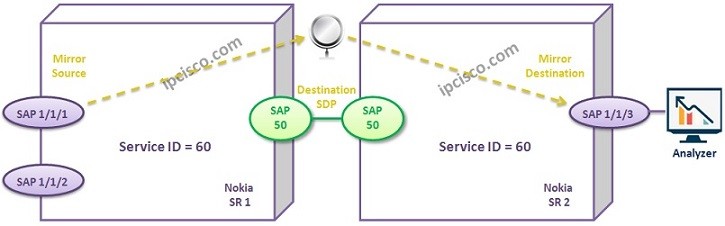
Remote Service Mirroring Configuration
Remote Service Mirroting is the other Service Mirroring type. As we have talked about before, Remote Service Mirroring is the service mirroring that is done between different devices. In this lesson, we will configure an example topology for Remote Service Mirroring. For our example, we…
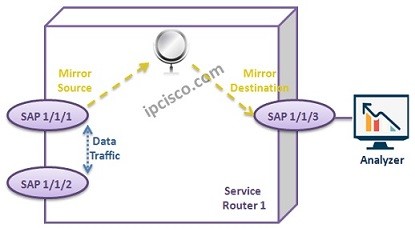
Local Service Mirroring Configuration
Local Service Mirroring Configuration In this article, we will focus on Nokia (Alcatel-Lucent) Service Mirroring Configuration. As we have talked about before, there are two Service Mirroring Type. Local Service Mirroring and Remote Service Mirroring. Here, we will configure Local Service Mirroring. Local Service Mirroring…
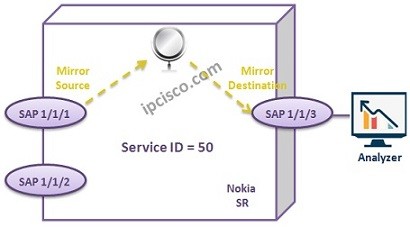
Nokia Service Mirroring
During troubleshooting activities, different tools are used to determine the cause of a problem. Mirroring is also a troubleshooting tool for these activities. In Nokia (Alcatel-Lucent) world, mirroring term corresponds “Service Mirroring”. As you can understand from the maining, basically, mirroring means copying the same…
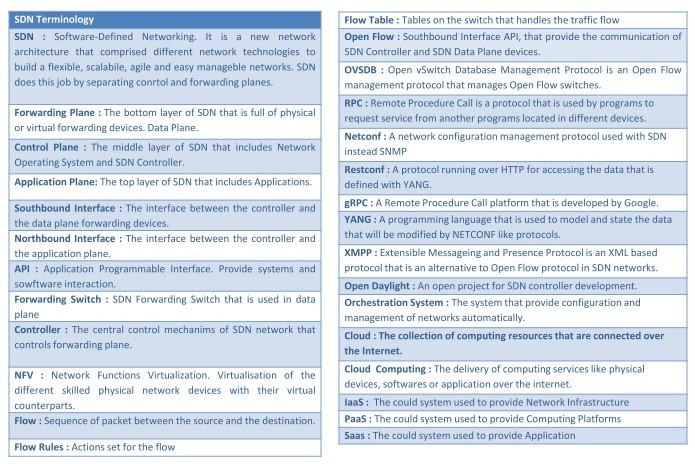
SDN Terminology
SDN Terminology In this SDN Terminology lesson, we will define the main terms used in SDN (Software-Defined Networking). SDN : Software-Defined Networking. It is a new SDN network architecture that comprised different network technologies to build a flexible, scalabile, agile and easy manageble networks. SDN…
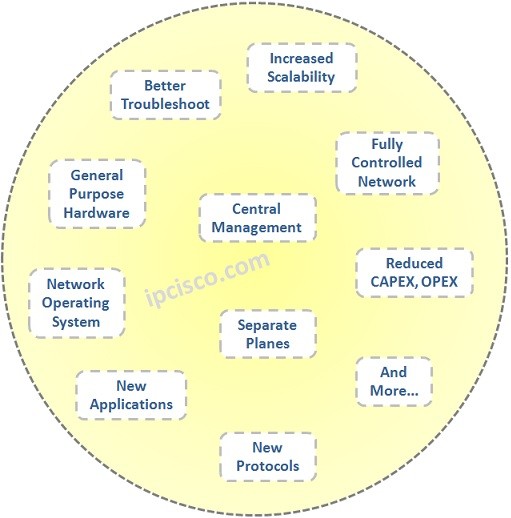
What Will SDN Bring?
New Features Coming With SDN Software-Defined Networking (SDN) brings many innovation to the Traditional Networks. It provides this with newly defined architecture. So, what will sdn bring? What are these SDN features? These are: • New architecture that seperate Control Plane and Data Plane, •…
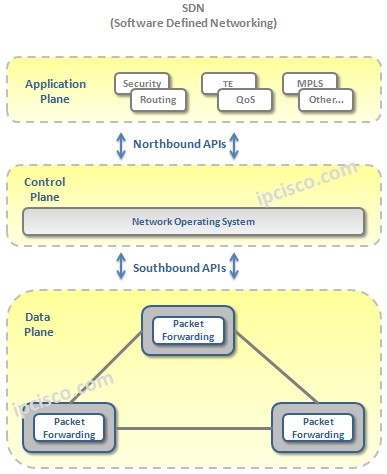
SDN Architecture Components
SDN Architecture Components SDN Architecture consist of different components. Here, we will see all these SDN Architecture Components and their duty one by one. What are these SDN Components? The basic SDN Terms, SDN Components are: • Network Devices (Data Plane) • SDN Conroller (Control…
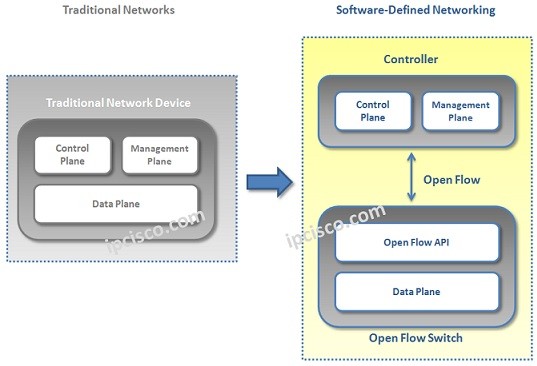
Traditional Network Drawbacks Versus SDN
In this lessons, we will talk about SDN versus Traditional Networks. We will give the drawbacks of traditional networks and give the benefits coming with SDN. Till recent years many companies were using Traditional Network Architectures. They are still widely used in the World. But…
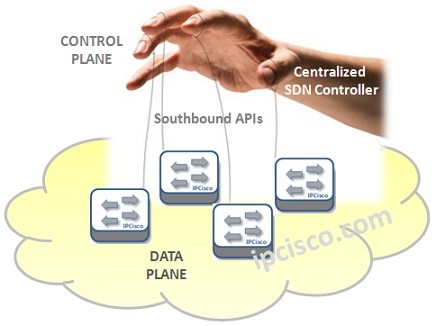
What is SDN ?
SDN Overview SDN (Software-Defined Networking) is a new network architecture that comprised different network technologies to build a flexible, scalable, agile and easy manageble networks. With its new view, SDN decouple network into two plane as Control Plane and Data Plane. This provide a central…
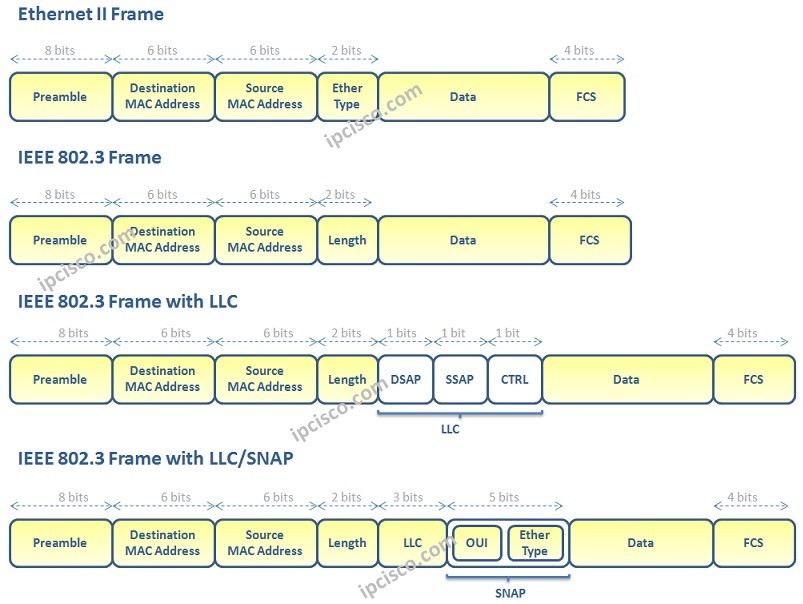
Ethernet Basics
Ethernet is the most used technology in LANs in network world. There are various technologies can be used on LANs like Ethernet, Token Ring, FDDI. But the most popular and widely used one is Ethernet. In your career, you will work on Enternet more than…
Local Area Networks
There are three common network types according to their coverage size. These are, LANs, MANs and WANs. LAN is the smallest sized network in these three network type. LAN (Local Area Network) is a small network that is built within a small geographical area. A…
Switches
Switches Switches are one of the most important network equipments of a computer network. It is the main device of a LAN (Local Area Network). In this lesson we will see Switches. You can alse check wiki definition, here. Switch is a Layer 2,…
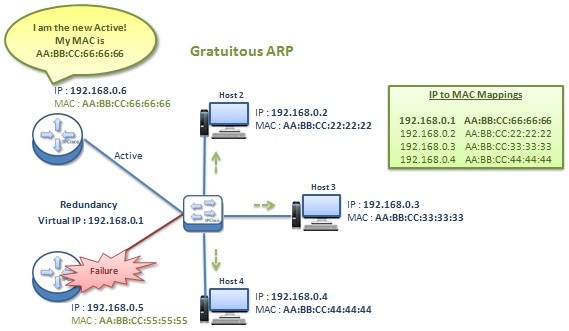
Gratuitous ARP
Gratuitous ARP, is the ARP that is used to inform the network about IP to MAC Mappings after a change. It is sent as Broadcast message to all the nodes in the network. The usage of Gratuitous ARP is a little diffeerent than ARP (Address…
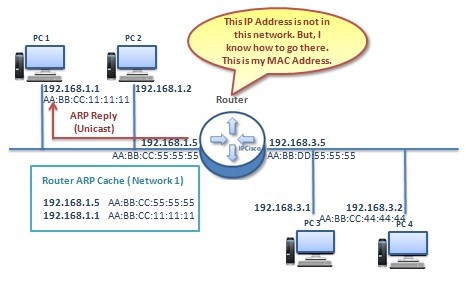
Proxy ARP
Basically Proxy ARP is the ARP that is used between one more networks. In other words, we can say that Proxy ARP provides data link dicovery between different networks. Here, we will explain Proxy ARP with an example. For our Proxy ARP example, we will…
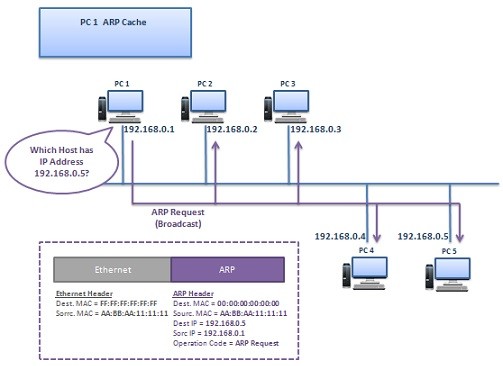
Address Resolution Protocol (ARP)
ARP (Address Resolution Protocol) is a Layer 2 Protocol. Layer 2 uses Physical addresses (MAC addresses) for the communication. Here, ARP Protocol is used to convert a given IP address to the related hardware address (MAC Address) to provide this. This important duty makes this…
Huawei AAA Configuration
AAA Configuration is done basically in similar ways in different vendor equipments. But for specific vendors, the configuration commands are a little different than the other. Here, we will focus on Huawei Routers and we will configure AAA on a Huawei Router. We will learn…
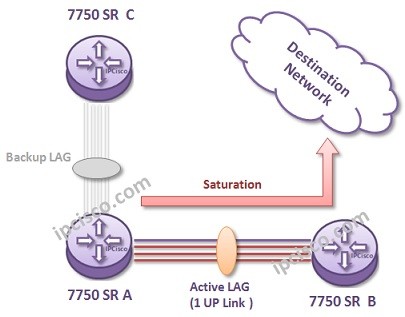
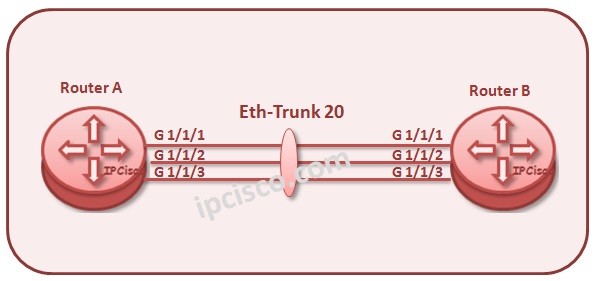
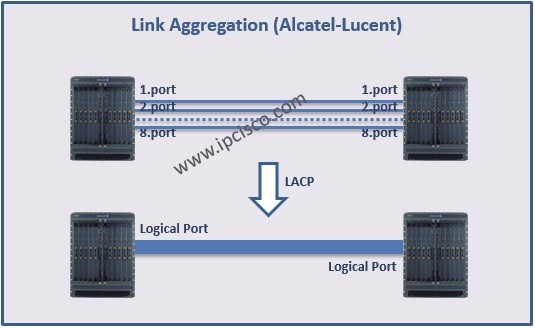
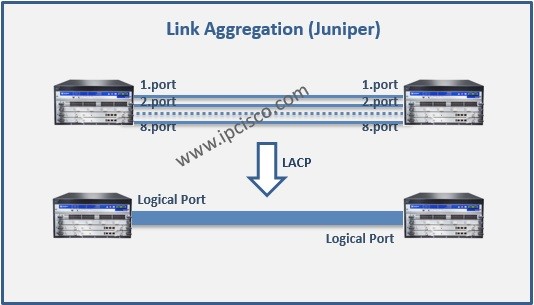
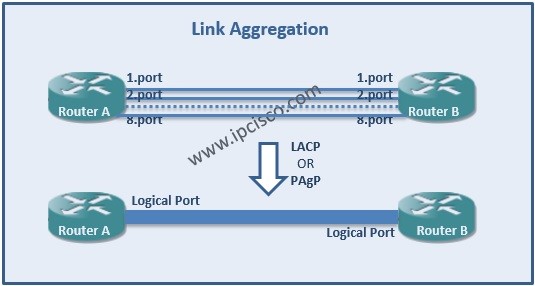
Ethernet Redundancy with LAG
Redundacy is very important for a network. In many networks, redundacy is provided in different type of topologies or protocols. Here, we will talk about redundancy on Ethernet. In this lesson, we will learon one of these redundancy mechansims, Link Aggregation (LAG). There are two…
GLBP Configuration on Cisco
GLBP Cisco Configuration Example GLBP is a Cisco Proprietary Firsth Hop Redundancy Protocol. In this lesson, we will configure GLBP on Cisco devices with a GLBP Cisco Configuation Example. For our GLBP Example, we will use the below topology. For GLBP Cisco Configuration, there are…
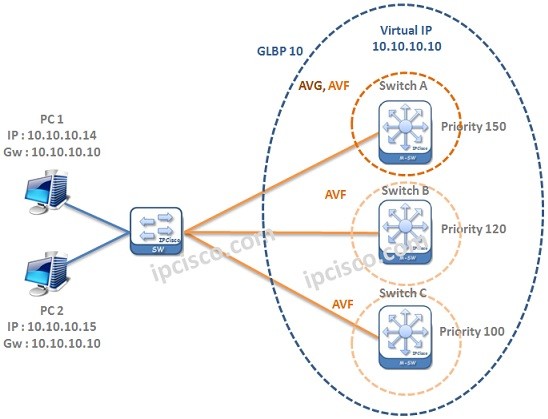
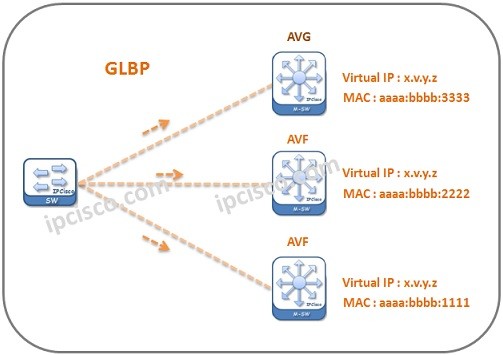
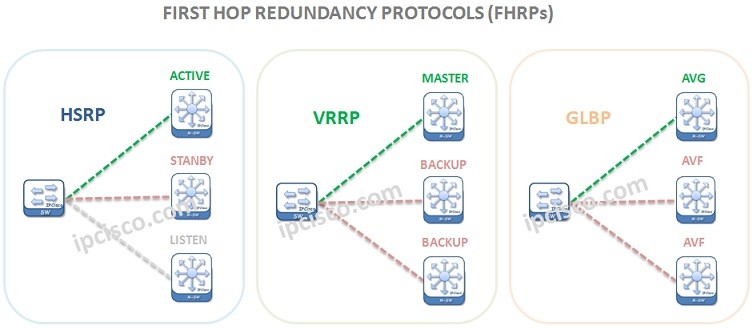
GLBP (Gateway Load Balancing Protocol)
GLBP Overview GLBP (Gateway Load Balancing Protocol) is an another First Hop Redundancy Protocol. It is a Cisco proprietary protocol like HSRP. So ,you can only use Gateway Load Balancing Protocol on Cisco devices. Here, we will learn the details of the protocol and we…
First Hop Redundancy Protocols (FHRPs)
Redundancy is a common point for today’s High Available Networks. First Hop Redundancy is one of the redundancy mechanisms that provide high available and always on networks. These redundancy mechanims provide redundancy by providing multiple alternative paths to the destinations and ensure single point of…
HSRP Configuration on Cisco IOS
HSRP Configuration Example on Cisco Routers In this section we will do an HSRP Cisco Configuration to understand the issue better. To do this we will use the below HSRP topology. At the end of this article, you will find the GNS3 configuration lab of…
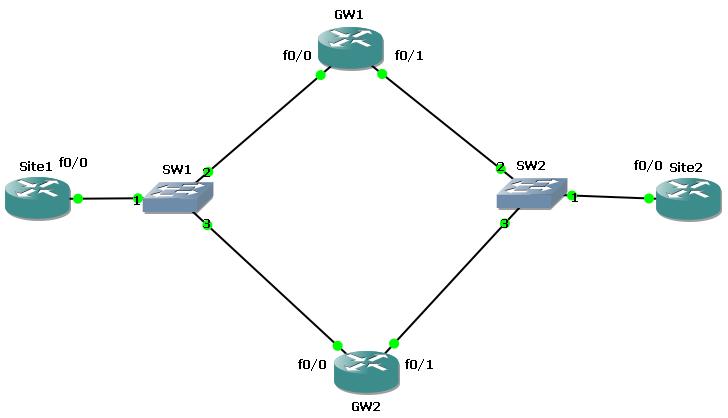
VRRP Configuration on Cisco
How to Configure VRRP on Cisco Switches? In this VRRP exampleCisco Configuration Example, we will work on Cisco IOS and configure VRRP (Virtual Router Redundancy Protocol) on Cisco Routers. Configuring VRRP Protocol is like configuring Cisco Proprietary protocol HSRP. There are only small command differences.…
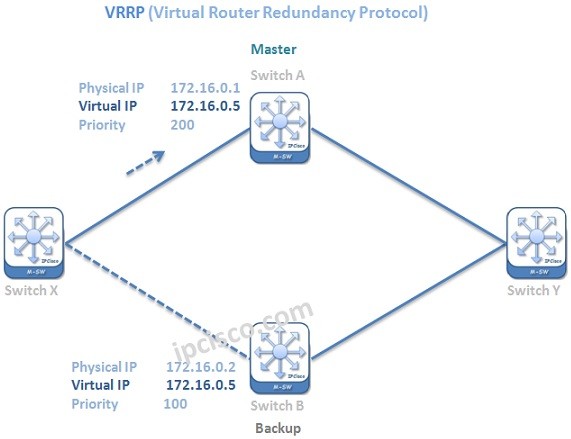
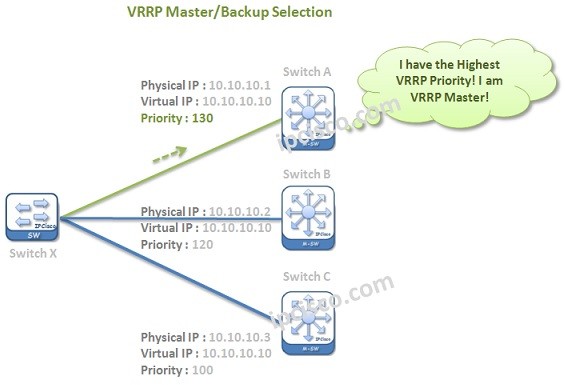
VRRP (Virtual Router Redundancy Protocol)
VRRP Overview VRRP (Virtual Router Redundancy Protocol) is a standard based First Hop Redundancy Protocol. It eliminates the single point of failure by using multiple optional devices. Traffic prefers going through the selected Master device. You can reaach the related rfc here. If a failure…
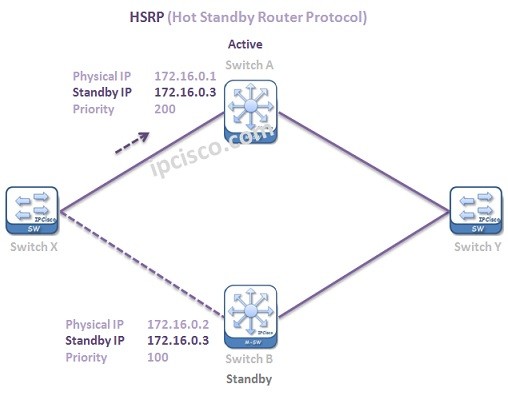
HSRP (Hot Standby Router Protocol)
What is HSRP? HSRP (Hot Standby Router Protocol) is a Cisco proprietary First Hop Redundancy Protocol (FHRP). Hot Standby Router Protocol first hop redundancy mechanism provides an alternative path as a redundant and a proactive action for any failure on a device. In this HSRP…
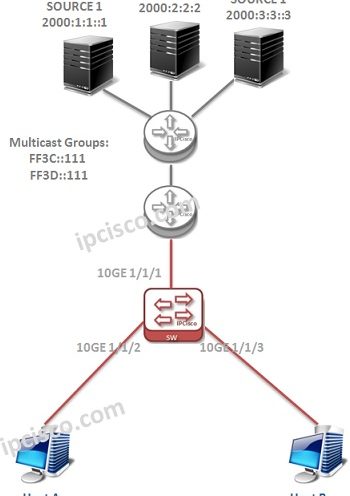
MLD Operations
MLD Operations In this lesson, we will talk about the specific operations of MLD. We will see; • MLD Querier Selection • MLD General Query, Group Query and Report Mechanism • MLD Multicast Group Joining Operation • MLD Multicast Group Leaving Operation • MLDv2 Source…
MLD Configuration on Cisco
MLD Configuration on Cisco In this lesson we will configure Multicast Listener Discovery (MLD) on Cisco devices. Out Multicast Network will be like below: Now, let’s start to configure MLD. MLD Version The default version of MLD is version 2. But to show you, we…
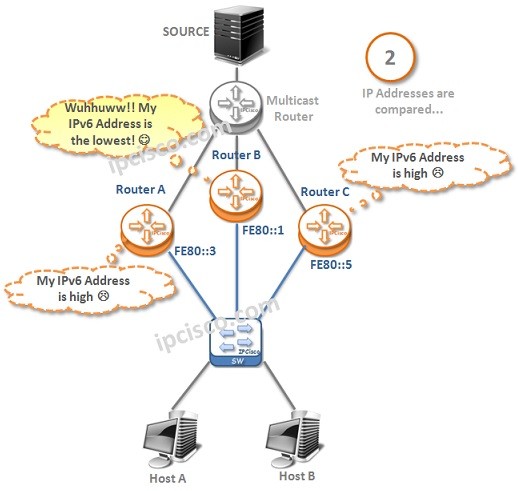
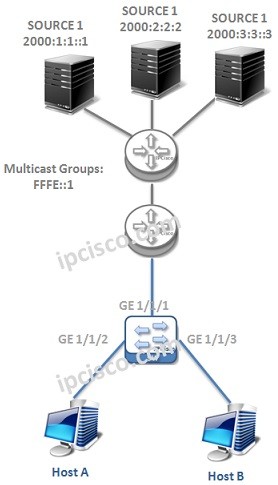
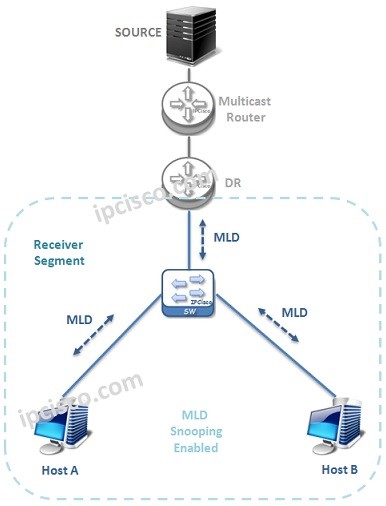
MLD (Multicast Listener Discovery)
What is MLD? Multicast Listener Discovery (MLD) is the IPv6 Multicast Group Membership Protocol. It works between the Multicast Routers and the Multicast hosts with Query,Report and Leave Messages. MLD works between MLD Querier router and the hosts. It controls Multicast member joins and leaves.…
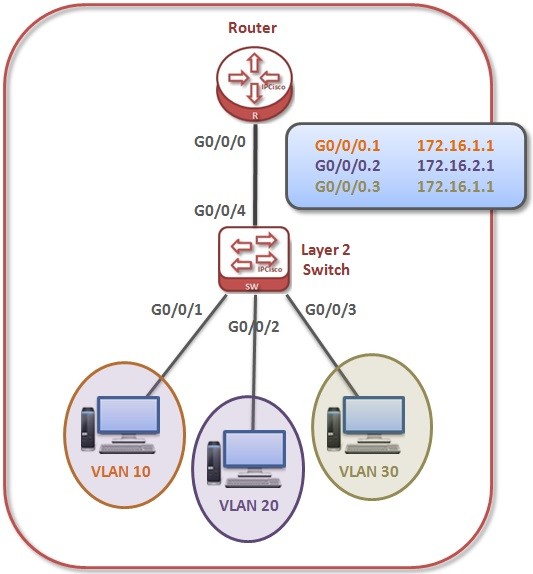
VLAN Routing with Layer 2 Switch and Router on Huawei
Huawei VLAN Routing with Layer 2 Switch is done with the help of a Layer 3 device, a router. Mainly, in the router, in layer 3, gateways are created for the VLANs. These gateways are the subinterfaces under the physical interface. For each subinterface, an…
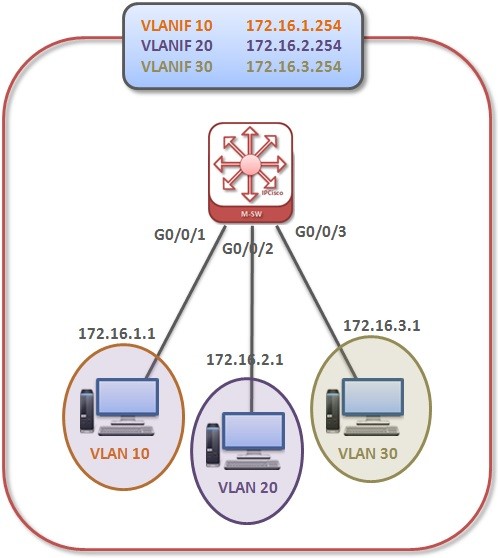
VLAN Routing with Layer 3 Switch on Huawei
In this lesson we will learn Layer 3 VLAN Routing with VLAN Routing Huawei Configuration Example. We do not need any other Layer 3 device for VLAN Routing with Layer 3 Switch. Because Layer 3 switch can achieve this routing facility. Here, instead of subinterface,…
Static Routing on Juniper Routers
Static Routing on Juniper Routers Static Routing is the manual route configuration on routers. In JUNOS, static route configuration is done similarly with other Network operating systems. After “static route” command, the destination network is mentioned and then next-hop ip address is given. This static…
Huawei Access-Lists (ACL)
Huawei Access-Lists In this configuration example, we will learn the Access List (ACL) Configuration on Huawei Routers. Configuring Access Lists has some basic steps and we will cover all these steps in this article. First of all, let’s remember the Access List types. There are…
Basic Nokia Service Router Configuration
How to Configure a Nokia Service Router? Command Line Interface (CLI) is the interface that we can configure, manage and maintenance router operations manually. Each Network Engineer works with Command Line Interface (CLI) in daily configuration activities.In this lesson, we will learn Basic Nokia…
Basic Terms for Internet
Like millions of people on the world, as a network engineer we are also using Internet. But a little different from other people, we also need to know some common terms of our main working area, Internet. Let’s begin and see what are the Basic…
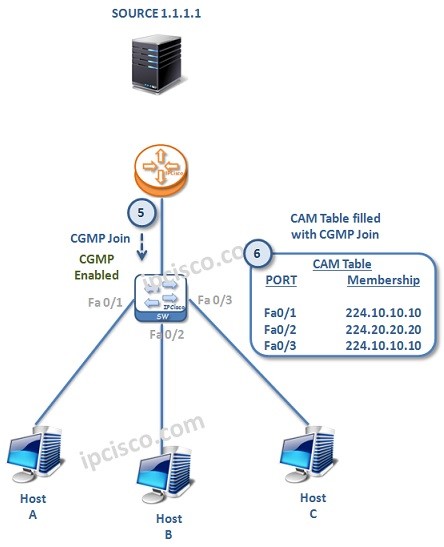
Cisco Group Management Protocol (CGMP)
Cisco Group Management Protocol (CGMP) Cisco Group Management Protocol (CGMP) is a Cisco proprietary Layer 2 protocol used for Layer 2 efficiency at layer 2. Basically whenever a host want to join a multicast group, it send IGMP Join message to the target group. This…
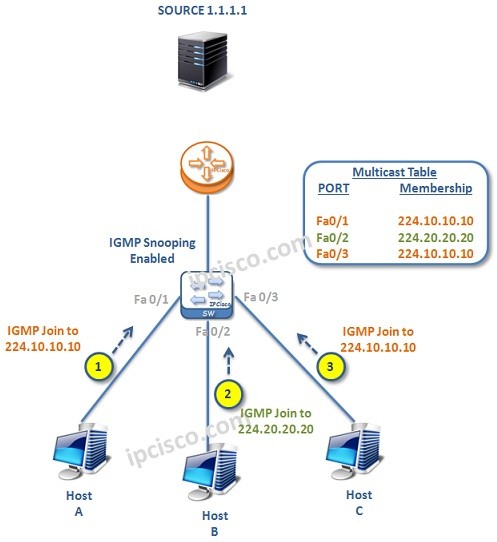
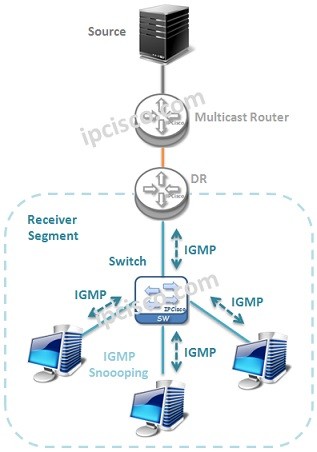
IGMP Snooping
What is IGMP Snooping? IGMP Snooping is a Multicast mechanism that runs on Layer 2 switch. This mechanism checks the IGMP join, leave messages and record the information about user about the group that it joins or leaves. With this mechanism, Multicast Group Joins and…
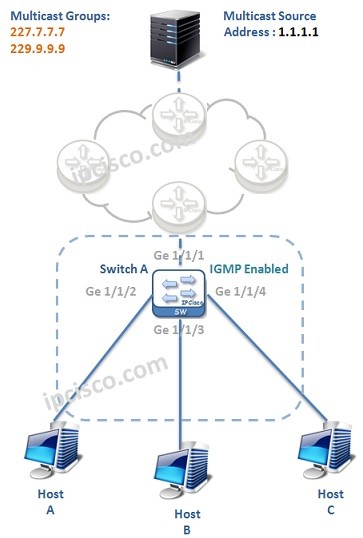
Cisco IGMP Configuration Example
In this configuration example, we will configure Cisco Catalyst Switch for IGMP (Internet Group Management Protocol). As you know IGMP is used to manage host memberships to the multicast groups. This is done at the edge switch in the multicast network. So, we will do…
IGMP (Internet Group Management Protocol)
What is IGMP? IGMP (Internet Group Management Protocol) is a Host-Router Multicast Signalling Protocol that provides dynamically registration of the hosts to the desired Multicast Groups. With IGMP, Host requests to join to the Multicast Groups. This join request comes to the DR (Designated Router).…
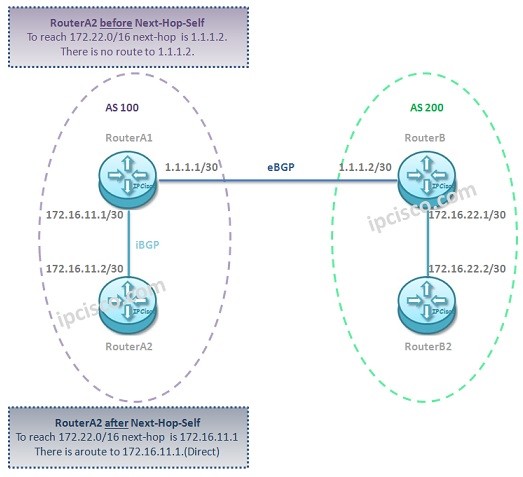
Next Hop Self Command on Juniper Routers
BGP Next Hop Self Configuration on Juniper Routers In BGP Configuration, there are some key commands and concepts used for a better BGP operation. BGP Next Hop Self is one of these commands used in Juniper routers. When an eBGP route advertised to vie iBGP,…
Routing Policy Configuration on Juniper Routers
Routing Policy Configuration on Juniper Routers Routing Policies are the rules that allows you to control and modify the default behaviour of the routing protocols like RIP, OSPF, IS-IS etc. With this control and modify mechanims, you can arrange the routing facilities for your network…
RIP Configuration on Juniper
RIP Configuration on Juniper In this lesson, we will configure Juniper routers for RIPv2. RIP is the simplest Routing Protocol and configuring RIP on Juniper Routers need a couple of simple steps. We will see each of these steps one by one. For our Juniper…
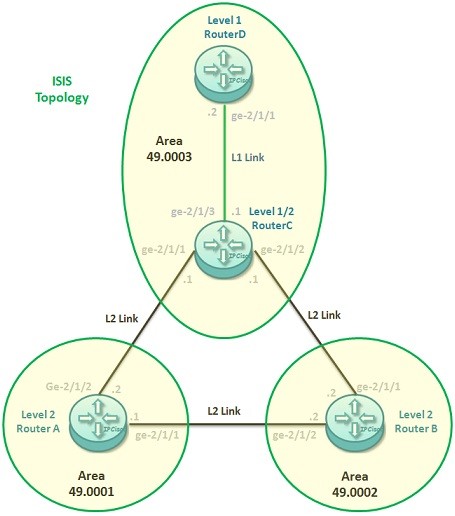
ISIS Configuration on Juniper
How to Configure ISIS on Juniper Routers? IS-IS Protocol is a very good Routing Protocol. But it is rarely used nowadays. Instead ISIS Protocol, OSPF is generally used Routing Protocol. By the way, there are still some common Service Providers are using ISIS. So, it…
Routing Tables of Juniper
Routing Tables of Juniper There are multiple Routing Tables in Juniper Routers. These Routing Tables and their roles are given below: • inet.0 - Stores IPv4 Unicast Routes. • inet.1 - Stores IPv4 Multicast Routes. • inet.2 - Stores IPv4 Unicast Routes used for Multicast…
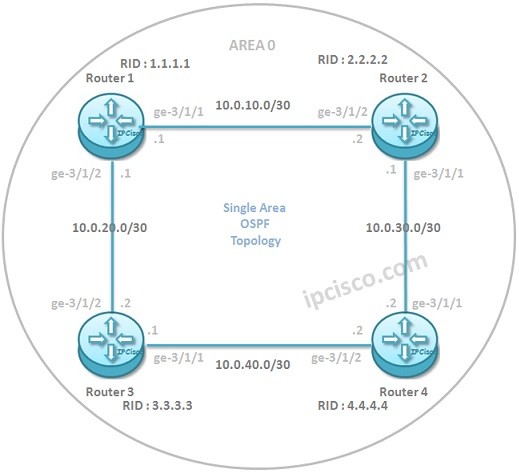
Single Area OSPF (OSPFv2) Configuration on Juniper
Configuration on Juniper In this lesson, we will see the OSPFv2 Configuration on Juniper for Single Area OSPF. For this OSPF Example, we will use the below topology consist of four OSPF routers. All of the Interfaces of these routers ( each one has two…
Basic BGP Configuration on Juniper
BGP is one of the widely used Routing Protocol. It is also known as Internet Protocol. In this Juniper BGP Configuration Example, we will configure BGP on Juniper Routers. We will use the below simple topology for our Juniper BGP Configuration Example. We will see…
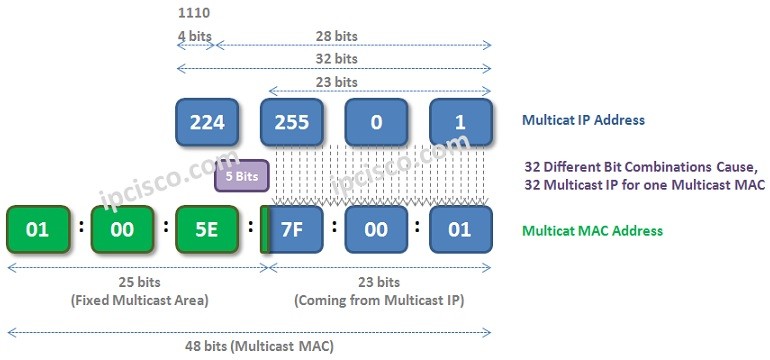
Multicast MAC Addresses
What is Multicast MAC Address? Multicast MAC Addresses are the MAC addresses start with 0100:5e . As you know, MAC address has 48 bits and consist of vendor code and host code. But for one MAC address, only the last 23 bits of that MAC…
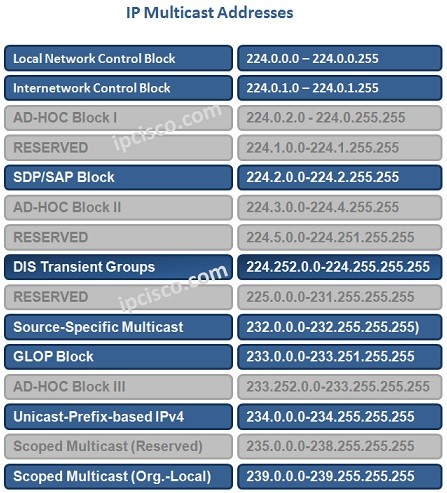
Multicast IP Addressing
Multicast Addresing is the addressing that is used for Multicast Groups. We can divide Multicast Addressing into two: IPv4 Multicast Addressing IPv6 Multicast Addresing These addresses identifies the destination of Multicast traffic. In other words, they show the Multicast Groups. The Multicast Source adresses uses…
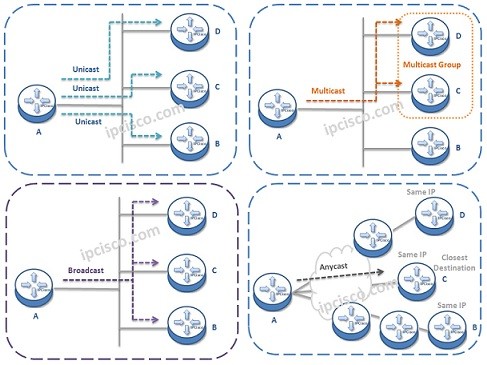
Unicast, Broadcast, Multicast, Anycast
There are different transmission techniques in communication if we divide communication according to the receivers. These communication techniques are: Unicast Multicast Broadcast Anycast Unicast is the communication that there is only one receiver. This is one-to-one communication. Multicast is the communication that there is…
BFD Operation
BFD (Bidirectional Forwarding Detection) mechanism uses packets to inform both ends that the protocol is configured. With these packets, BFD provide basic connectivity and the parameter negotiation. The main role of BFD is detecting the link failures by sending BFD packets in regular intervals. It…
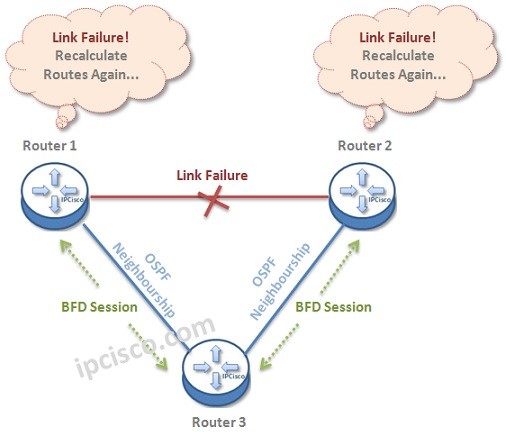
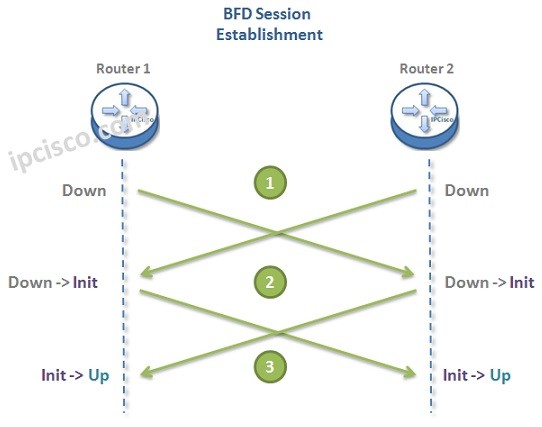
Bidirectional Forwarding Detection
What is BFD? For networks, failure detection is very important. There are vairous mechanisms used for this purpose. One of them is BFD (Bidirectional Forwarding Detection). In this lesson, we will learn bfd meaning, what is BFD and why we use this mechanism between nodes.…
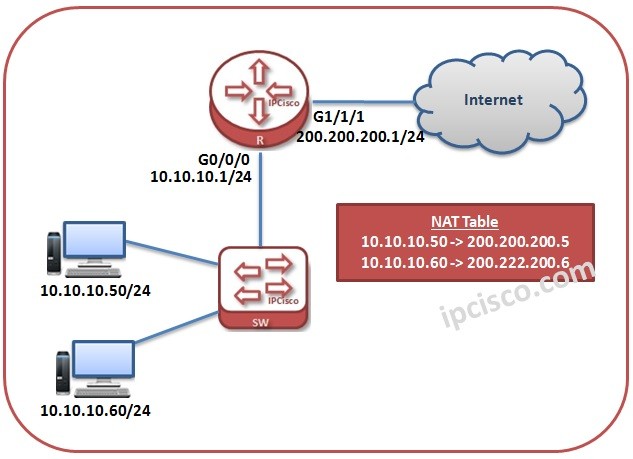
NAT Configuration on Huawei Routers
Huawei NAT Configuration NAT (Network Address Translation) is a concept used to translate Private block IP addresses to the Public IP Addresses. By doing this, it provides internet connection to the devices that has Private Blcok IP Addresses. In this lesson we will learn…
Link Aggregation on Huawei Routers
Link Aggregation is one of the important lessons of networking. This is also used too much in network operations. In this lesson, we will talk about Huawei Link Aggregation Configuration. We will show Huawei Link Aggregation Configuration with two examples. One of these examples will…
TCP versus UDP
TCP vs UDP Before, we have talked about TCP and UDP as an overview. Here, we will compare these two protocols’s main characteristics and we will see TCP vs UDP. This comparison is very important and generally a question asked in a Network Engineering Technical…
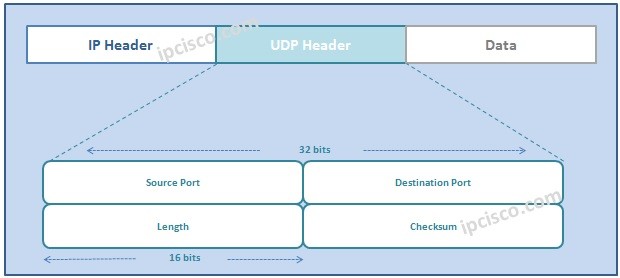
UDP (User Datagram Protocol)
UDP Protocol UDP Protocol (User Datagram Protocol) is another Tranport Layer Protocol. It is simpler than TCP. We will also see the differences of these two protocols in TCP vs UDP lesson. It is generally used in unsenstive communications and real time applications that do…
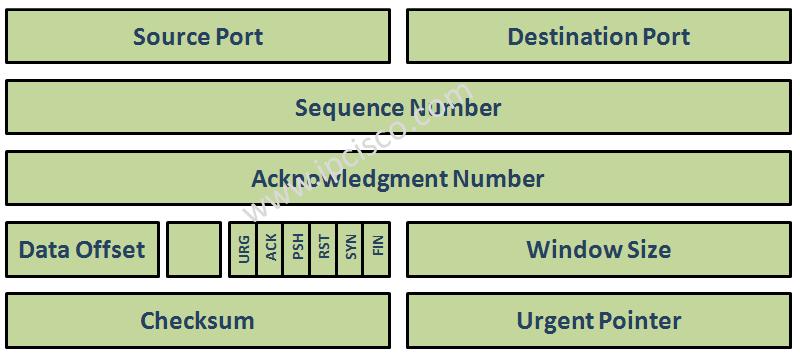
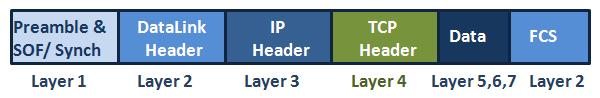
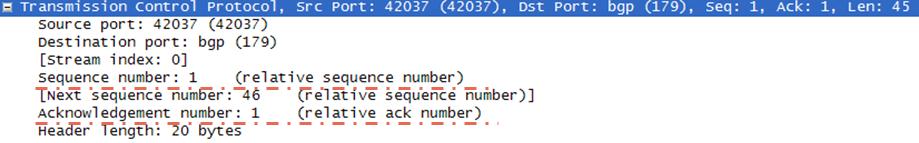
TCP (Transmission Control Protocol)
Transmission Control Protocol (TCP) TCP (Transmission Control Protocol) is the most important Transport Layer Protocol. It is also one of the important Protocols of network world and Cisco CCNA Certification. The other Transmission protocols are UDP and SCTP. We will talk about these protocols in…
Switch Virtual Interfaces
Inter VLAN Routing, in other words Routing between VLANs can be achieved by SVIs (Switch Virtual Interfaces). Here, we need to have a Multi Layer Switch. Layer 2 switches can also have SVI, but only one.This is the default switch management SVI created for VLAN…
Inter VLAN Routing with Router on Stick
What is Inter VLAN Routing? VLANs are used to separate different subnetworks in a big network. If you divide a network with VLANs, each of these new VLANs become a different network. Devices reside in different networks, can not communicate with the other devices reside…
Network Cabling
Cabling is the Layer 1 of OSI Model. One of the most important part of a network. With the media the network traffic can travel from one end to the other end. This can be done through wireless networks also. But cabling is always used…
Hubs, Switches and Routers
We have talked about the Network Devices before. Now, let’s go deeply with some of the important ones. Hubs, Switches and Routers. Here, we will focus on Ethernet Hub vs Switch vs Router. We will learn the main similarities and the differences of these three…
Network Devices
In computer networks, many different network devices are used. These devices used in computer networks has different characteristics. Each of them provide a specific role. What are these network equipments? Basically these network equipments are : • Hubs • Bridges • Layer 2 Switches •…
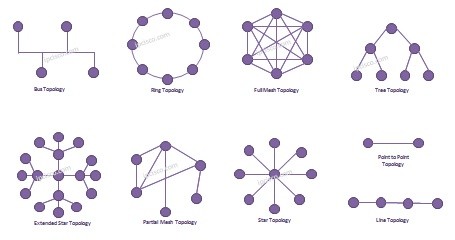
Network Topologies
Network Topology Types Basically a network topology means that, connection style of the network nodes. To build a Network, we need a network topolog. There are different LAN Network Topologies that can be used for different network scenarios. What are these Network Topologies? …
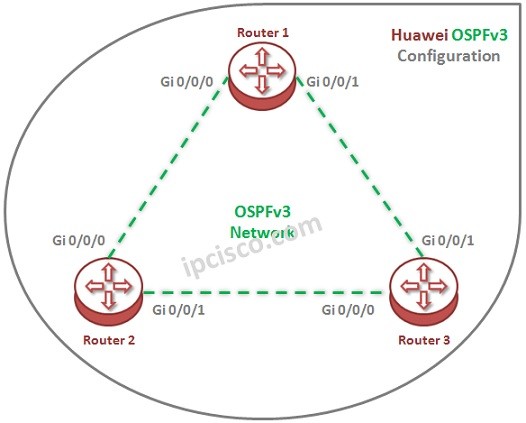
OSPFv3 Configuration on Huawei
In this Huawei OSPFv3 Configuration lesson, we will configure OSPFv3 on Huawei routers. For our OSPFv3 Configuration Example, we will use the below OSPFv3 Network Topology: Let’s start our Huawei OSPFv3 Configuration on these three Huawei Routers. You can download this configuration on Huawei…
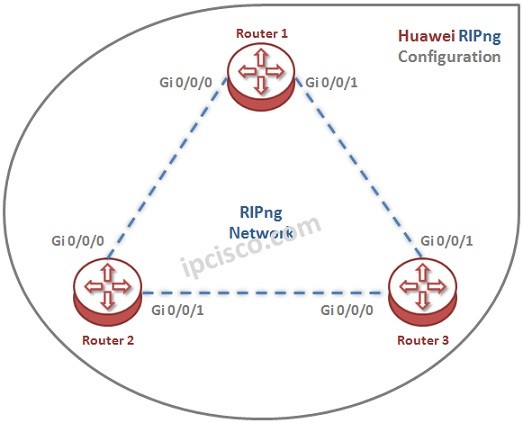
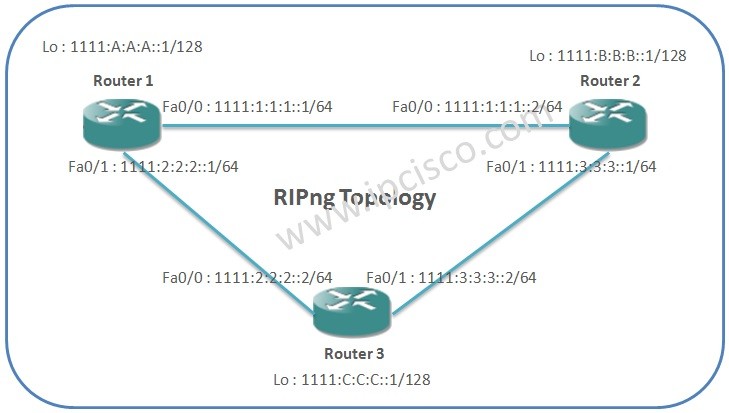
RIPng Configuration on Huawei
In this lessons RIPng Configuration Huawei Example, we will focus on the configuration of the basic IPv6 Routing Protocol, RIPng. We will learn RIPng Configuration on Huawei routers. In another lesson, we will learn also OSPFv3 Configuration on Huawei routers. For our RIPng Configuration…
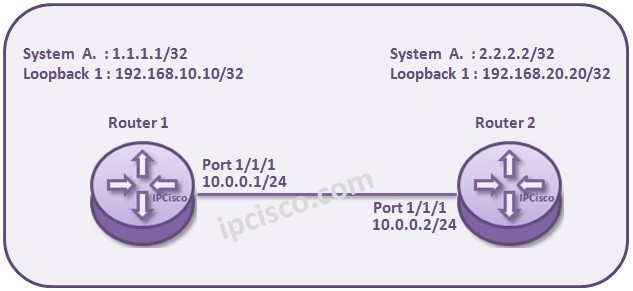
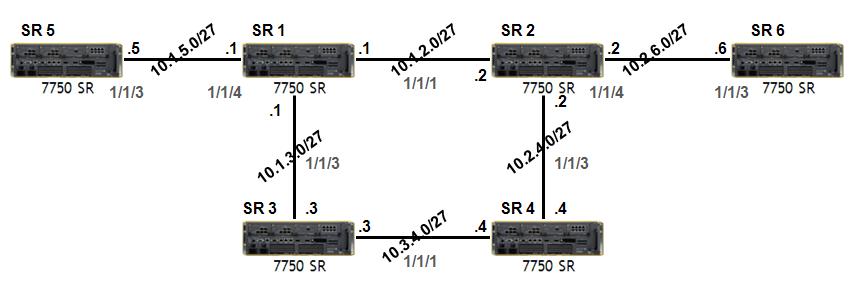
Basic BGP Configuration on Nokia 7750 SR
How to COnfigure BGP on Nokia 7750 Service Routers? In this lesson, we will see How to Configure BGP on Nokia 7750 Service Routers. Here, we will use Nokia 7750 Service Routers. For our Nokia BGP Configuration Example, we will use the below topology.…
Single Area OSPF Configuration on Nokia 7750 SR
How to Configure OSPFv2 on Nokia Service Routers? In this lesson, we will see How to Configure Single Area OSPF on Nokia (Formerly Alcatel-Lucent) Service Routers. We will learn Nokia OSPF Configuration. Here, we will use Nokia 7750 Service Routers. For our Single Area…
Nokia 7450 ESS Family
Nokia 7450 ESS Family Nokia 7450 ESS (Ethernet Service Switch) Family is the high capacity Multi Layer Switch Family that are mainly used in Backbone Networks of various Service Providers. There are various members of 7450 SR Family. Each of these has different capability and…
Nokia 7750 Service Router Family
Nokia 7750 Service Router Family Nokia 7750 SR (Service Router) Family is the high capacity Service Router Family that are mainly used in Backbone Networks of various Service Providers. There are various members of 7750 SR Family. Each of these has different capability and capacity.…
Nokia 7950 XRS Family
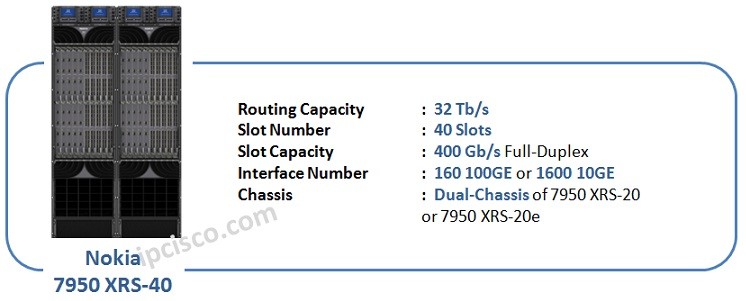
Nokia 7950 XRS Family Nokia 7950 XRS (Extensible Routing System) Family is the last and highest capacity Routers of Nokia (Formerly Alcatel-Lucent). These high capacity Nokia Routers are used in the Backbone Networks of Service Providers. There are various members of Nokia 7950 XRS Family.…
Nokia Routers and Multi Layer Switches
Nokia Routers and Multi Layer Switches Nokia (Formerly Alcatel-Lucent) has a very competitive and reliable network devices like its top rival vendors,Cisco, Juniper and Huawei. Especially Routers and Multi Layer Switches of Nokia are high capacity and widely used network equipments in many Service…
Nokia IP Filter Configuration Example 2
Almost all Network Engineers have realized that, they can access specific subnets and devices but they can not access the others. One of the ways to do this is IP Filters. With IP Filters, specific subnets can be restircted for some services and can be…
Nokia IP Filter Configuration Example 1
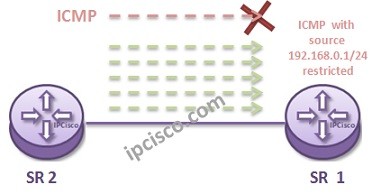
Here, we will show the IP Filter Configuration on Nokia (Formerly Alcatel-Lucent) Service Routers with an example. To do this, we will create an IP Filter on S1. And then deny the incoming ICMP traffic from a specific source prefix. For example such a configuration…
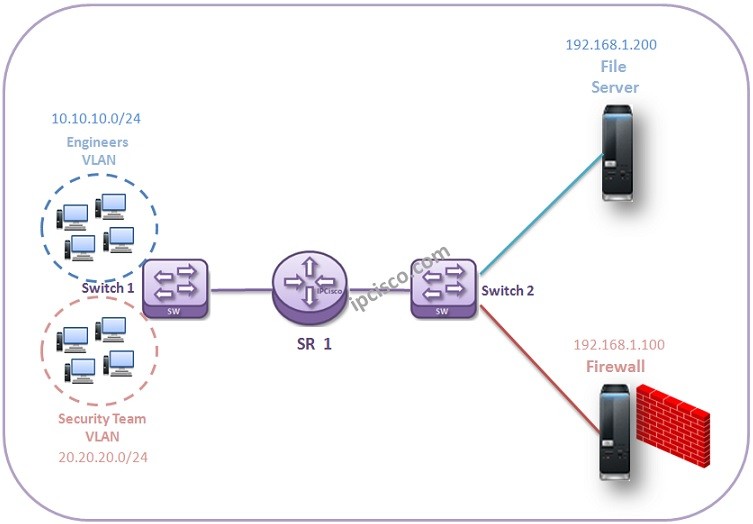
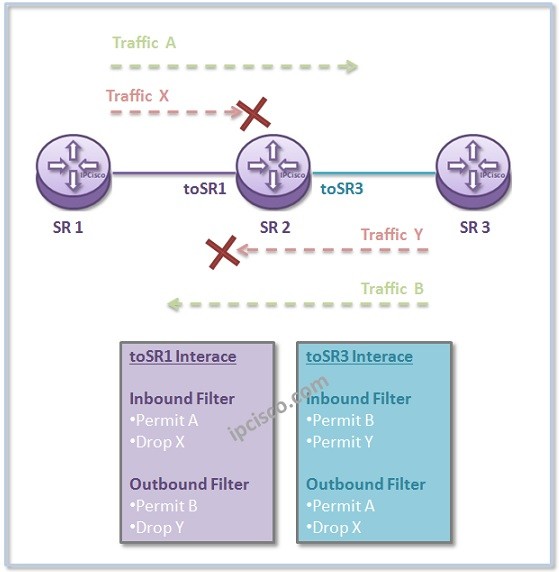
IP Filters (Access-Lists)
IP Filters, are the rules that force the router to permit or to deny mentioned IP addresses, ports, protocols etc. from a source to a destinatio in Nokia (Formerly Alcatel-Lucent) world. IP Filters is known as Access-List (ACLs). But while working with Alcatel-Lucent devices, generally…
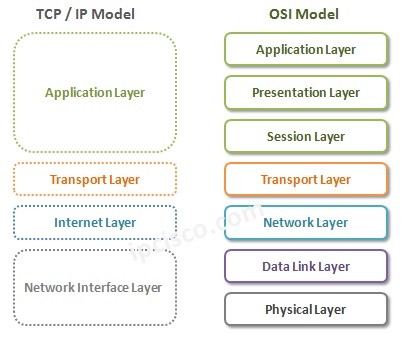
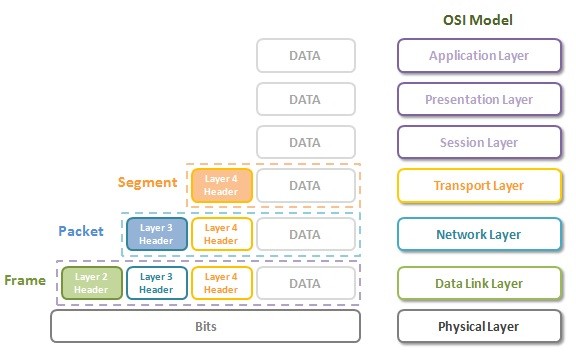
TCP/IP Model
TCPIP Model Overview TCP IP Model is another important referance model beside OSI Model in network world. OSI Referance Model was Seven Layered model, TCPIP Model is Four Layered or Five Layered Model. The four layer model is old one. The new one is five…
OSI Referance Model
OSI Model and TCP/IP Model Communication in a network has different layers and these different layers are mentioned in two different models. In other words,there are two common models in computer networking. These two common models are OSI Model and TCP/IP Model. As a beginner,…
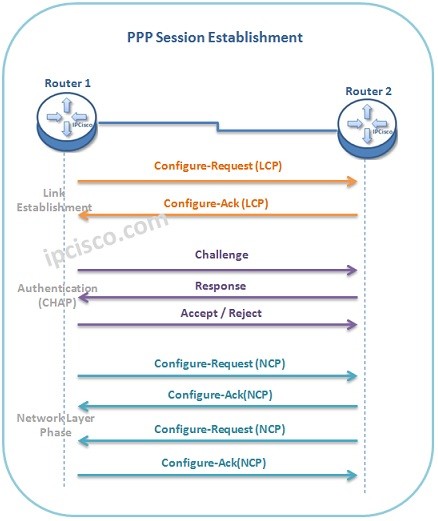
HDLC and PPP
HDLC (High-Level Data Link Control) HDLC (High-Level Data Link Control) is a Layer 2 WAN Encapsulation Protocol that is used on syncronous data links. It is the simplest WAN Protocol that can connect your remote offices over leased lines. HDLC has two versions. One of…
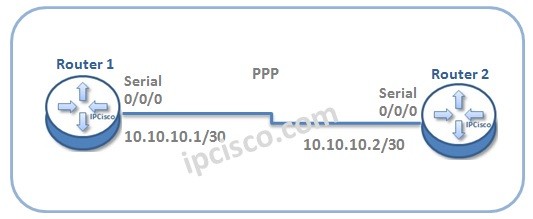
PPP Configuration on Cisco
PPP Configuration on Cisco Routers In this lesson, we will talk about PPP Configuration (Point-to-Point Protocol Configuration) on Cisco Routers. We will learn configuration commands for this general standard wan connection. In our PPP Configuration example, we will use the below basic topology: Now, do…
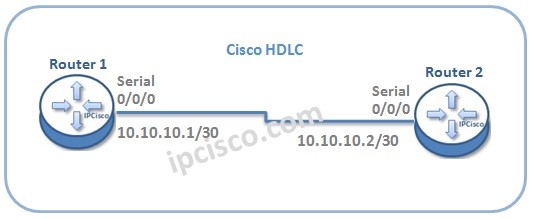
HDLC Configuration on Cisco
In this lesson, we will talk about HDLC configuration on Cisco Routers. Cisco HDLC has a different proprietary field in the data field of the protocol. For our Cisco HDLC Configuration example, we will use the below basic topology: Let’s start to configure Cisco HDLC…
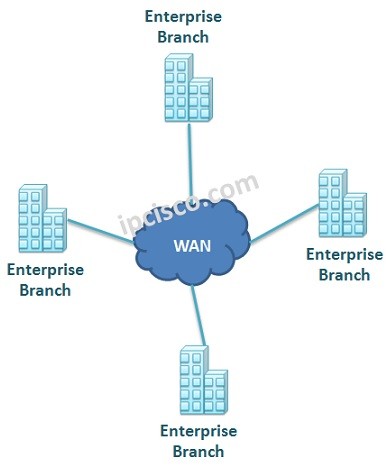
WAN and WAN Technologies
WAN & WAN Technology WAN Technology (Wide Area Network) is the network that connects the geographical far areas. It can be used for a client to connect to the corporate network, connections between the branch offices of a company and similar wide area connections etc.…
PPP Configuration on Huawei
In this lesson, we will talk about PPP configuration on Huawei Routers. For our PPP Configuration example, we will use the below basic topology: Orderly, we will do the below configuration for our PPP Configuration Example: 1) Enabling PPP 2) PAP and CHAP…
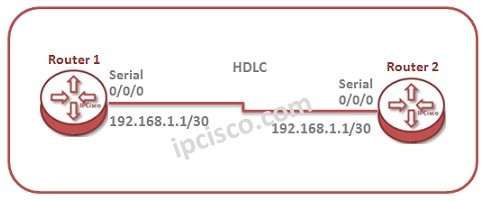
HDLC Configuration on Huawei
In this lesson, we will talk about HDLC configuration on Huawei Routers. For our HDLC Configuration example, we will use the below basic topology: Orderly, we will do the below configuration for our HDLC Configuration Example: 1) Enabling HDLC 2) Verifying HDLC…
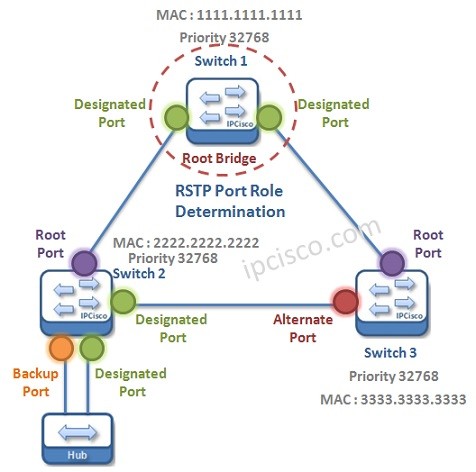
Rapid Spanning Tree Protocol (RSTP)
Rapid Spanning Tree Protocol (RSTP) is the second STP type. It is a fast converged version of Spanning Tree Protocol as its name implies. RSTP bypass the Blocking State and Listenning State of STP, and provide Forwarding State in 15 Seconds. So, the convergence time…
Spanning Tree Protocol Operation
Spanning Tree Protocol (STP) Operation is done with various sub processes. In this lesson, we will talk about each of these sub processes and explain STP Operation detailly. We will configure STP with Packet Tracer in another lesson. STP Switch Types First of all…
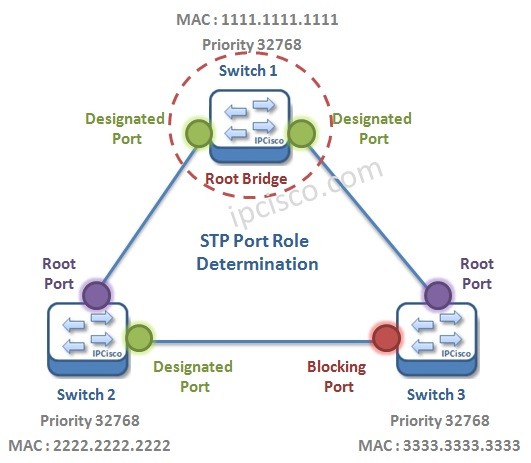
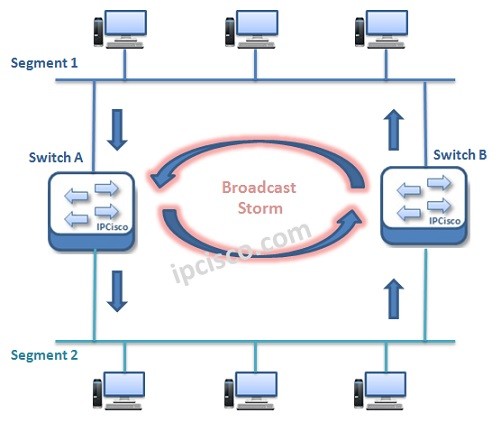
Spanning Tree Protocol (STP)
STP Overview In Layer 2 domain, redundancy is an important case. To provide redundant links, multiple connections are done between switches. But this redundancy mechanism can cause an undesirable situation that is called “L2 Loop”. To provide L2 redundancy and to avoid L2 loops, Spanning…
RSTP Configuration on Huawei
In this lessons, we will focus on RSTP (Rapid Spanning Tree Protocol) Configuration on Huawei Switches. For our Huawei RSTP Example, we will use the basic topology below. Let’s start to configure RSTP on one of these Huawei Switches, Switch 1. You can download…
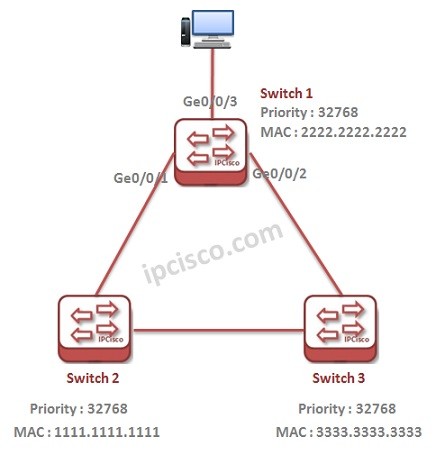
STP Configuration on Huawei
Huawei STP Configuration In this lessons, we will focus on STP (Spanning Tree Protocol) Configuration on Huawei Switches. For our Huawei STP Example, we will use the basic topology below. In another lesson, we will also learn Huawei RSTP Configuration. Let’s start to…
IES (Internet Enhanced Services) Configuration
In this article, we will focus on how to configure IES (Internet Enhanced Services) on Nokia Service Routers, we will learn Nokia IES Configuration. Here, our Service Router will be Nokia SR 7750. For our IES Example, we will use the below topology: Now, let’s configure…
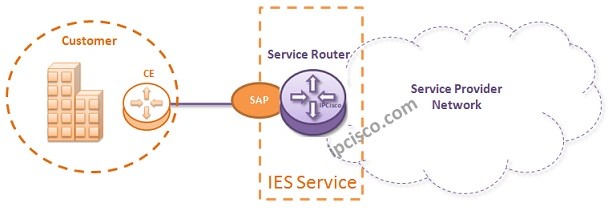
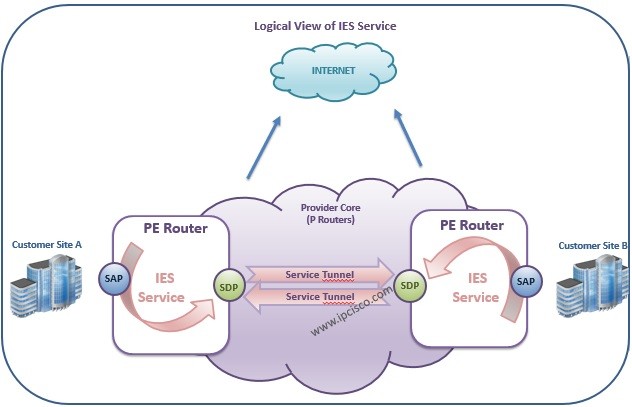
IES ( Internet Enhanced Services)
Internet Enhanced Services (IES) IES (Internet Enhanced Services) is an Nokia (Formerly Alcatel-Lucent) Service that provide Internet Access to the Customers. Here, from the customer view, IES is a connection point of the customers. In this lesson we will learn the theorical parts, configuration…
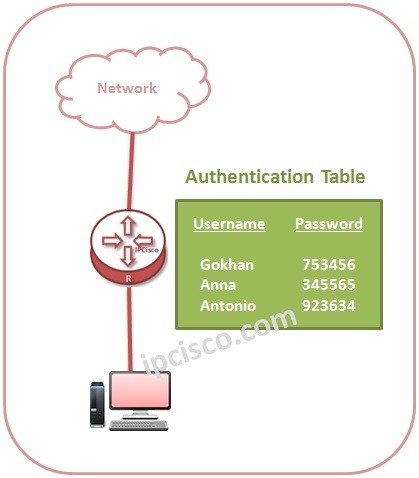
Authentication, Authorization, Accounting (AAA)
What is AAA? AAA is the abbreviation for Authentication, Authorization and Accounting terms. This mechanims provide security and some user specific steps for a user that access to the Enterprise Network. In an Enterprise Network, AAA is a very important security implementation. YOu can reach…
Interface Configuration on Nokia Routers
To configure an interface on Nokia Routers, on ALU TiMOS, is a little different that we do on Cisco routers, on Cisco IOS. In Nokia Service Routers, ports are like the interfaces in Cisco devices. Only its name is changing. Beside, the “Interface” name is…
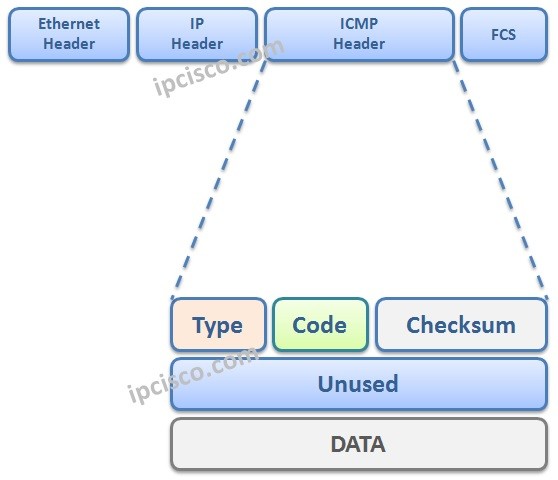
ICMP (Internet Control Message Protocol)
Internet Control Message Protocol is a Layer 3 Protocol. In IP networks, devices send ICMP encapsulated in IP packet. The general role of ICMP Protocol is generate error packets about the network devices and it is used in troubleshooting activities. As a summary, ICMP supports…
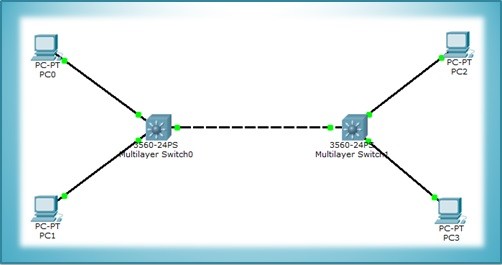
GVRP Configuration on Cisco
In this configuration example, we will focus on how to configure GVRP on Cisco. Here, for our GVRP Configuration Example, we will use the below topology. Let’s start our GVRP Configuration on each of these Switches. Switch A Confguration Firstly, we will create our VLANs…
GVRP Configuration on Huawei
GVRPis the standard based counterpart of Cisco VTP. In this configuration example, we will focus on how to configure GVRP on Huawei switches. For out Huawei GVRP Configuration example, we will use the topology below. On important reminding. Do not think that there…
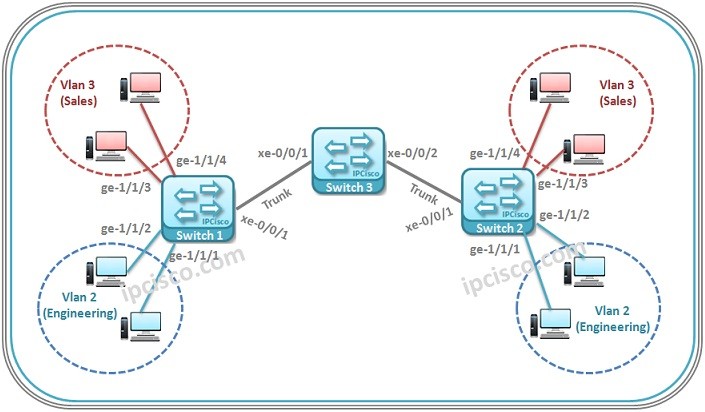
MVRP Configuration on Cisco
In this configuration example, we will focus on how to configure MVRP on Cisco switches. Here, we will use Cisco Catalyst 6500 series switches. For our MVRP configuration example, we will use the below topology. Let’s start our MVRP configuration. Switch A Configuration We will…
MVRP Configuration on Juniper
MVRP is the protocol that provides dynamic VLAN registration and creation. The counterparts of MVRP are Cisco VTP and standard GVRP. MVRP is an enhanced version of these protocols. Here, we will focus on how to configure MVRP in Juniper switches. We will use EX…
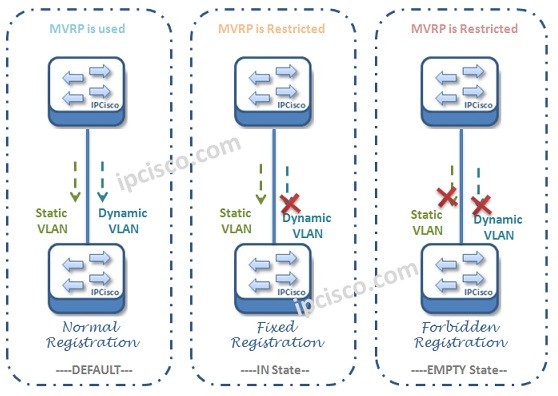
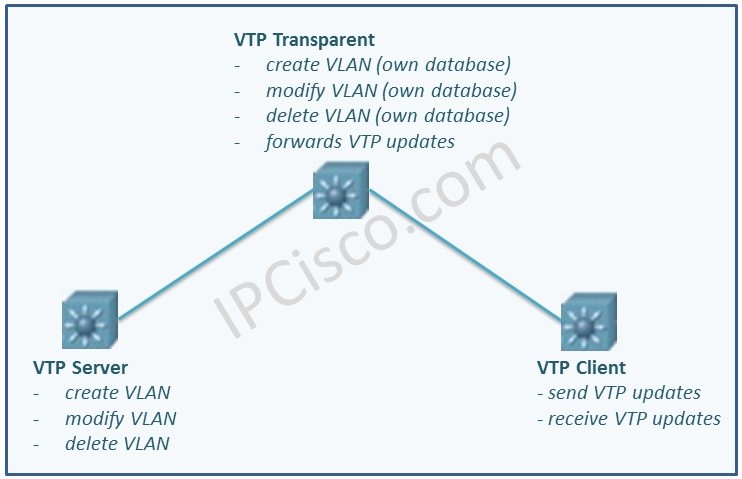
MVRP (Multiple VLAN Registration Protocol)
MVRP Overview MVRP (Multiple VLAN Registration Protocol) is the counterpart protocol of Cisco VTP and GVRP (GARP VLAN Registration Protocol). It is the last standard VLAN Registration Protocol, so it has richer properties than the other protocols. MVRP is the IEEE 801.ak standard. MVRP reduces…
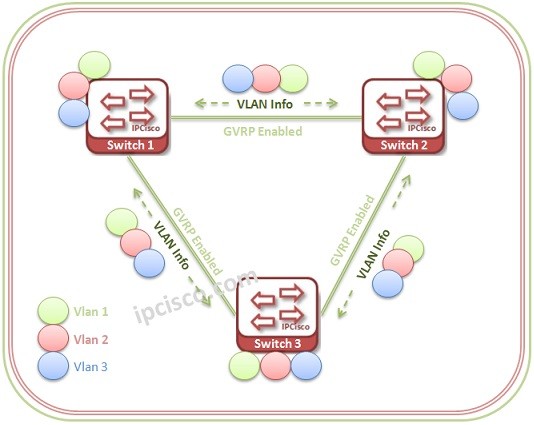
GVRP (GARP VLAN Registration Protocol)
GVRP Overview GVRP(GARP VLAN Registration Protocol) is a protocol that is used to control VLANs, dynamic VLAN registration and VLAN prunning in a network. GVRP does this dynamically VLAN management with exchanging VLAN information and prunning unnecessary broadcast and unicast traffic over 802.aQ trunk links.…
IPSec VPN Configuration On Huawei
In this lesson we will see IPSec VPN Configuration On Huawei Routers. IPSec configurations has some basic steps. These steps are given below: IPSec Authentication and Encryption Configuration IPSec Policy Configuration IPSec Interface Association IPSec Configuration Verification For our Huawei IPSec VPN Configuration,…
IPSec VPN Overview
IP Sec VPN provides a Private and Secure IP communication over a Public Network Infrastructure. With this technology, different sites or users in different geographical areas can communicate over a network and this provides a very good resource utilization. Here, we will learn tjheorical parts…
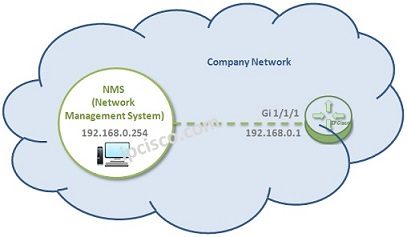
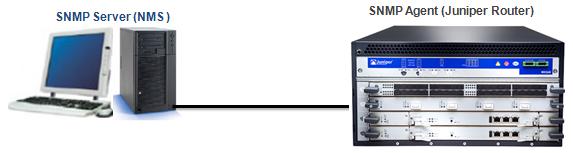
SNMP Configuration on Huawei
How to Configure SNMP on Huawei Routers? In this article we will focus on Huawei SNMP, How to Configure SNMP on Huawei devices. We will use the below simple topology and we will manage a router in Network Management System via SNMP. Here…
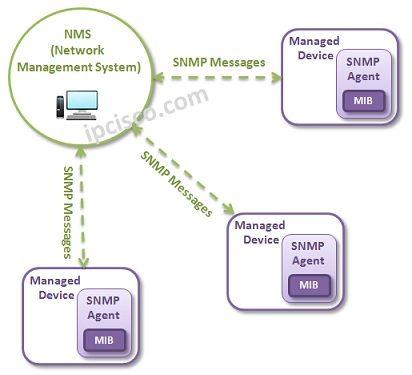
SNMP – Overview
Simple Network Management Protocol (SNMP) is the main protocol of Network Management. With SNMP, network devices are easily managed and conttolled by a central mechanism. It is an application protocol that provide the messaging between the controlled device and the management system. In this lesson,…
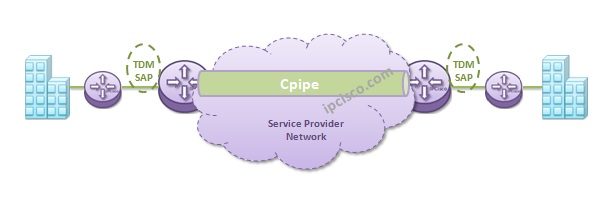
VPWS (Virtual Private Wire Service) – Fpipe, Apipe and Cpipe Configuration
VPWS Configuration Examples In the previous articles, we have seen Epipe Configuration Examples, Local Epipe and Distributed Epipe Configurations. Here, we will focus on another VPWS types, Fpipe, Apipe and Cpipe. Fpipe Configuration VPWS Fpipe Configuration is similar to Epipe Configuration with…
VPWS – Distributed Epipe Configuration
Distributed Epipe Configuration In the previous Epipe Example, we have talked about "Local Epipe Configuration". So, we have used only one device and our Epipe service was in this device. Here, we will use two router and we will show the "VPWS Distributed Epipe Configuration".…
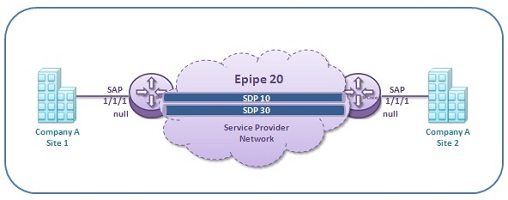
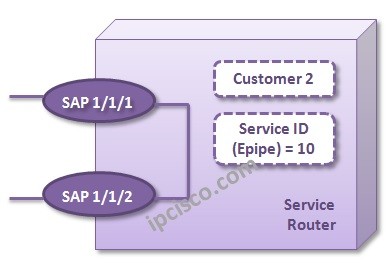
VPWS – Local Epipe Configuration
Local Epipe Configuration In the previous part we have talked about the VPWS service of Nokia. Now, we will focus on the configuration of the VPWS Service on Nokia devices. In this lesson, we will learn Local Epipe Configuration. In the next lesson, we will…
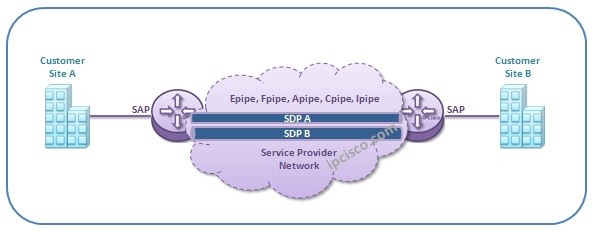
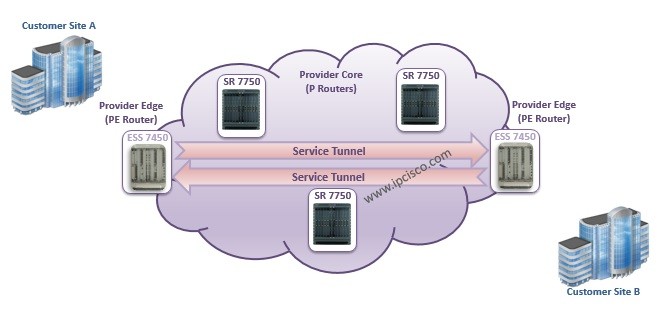
VPWS (Virtual Private Wire Service)
What is VPWS? VPWS (Virtual Private Wire Service) is Point-to-Point Layer 2 MPLS VPN Service of Nokia Service Routers. The other Layer 2 VPN Service is VPLS that is explained in another lesson. Here, we will focus on Virtual Private Wire Service . In another…
Huawei GRE Tunnel Configuration
How to Configure GRE Tunnel on Huawei Routers? In this lesson, we will use Huawei Routers, to configure GRE Tunnels. For our example, we will use the topology given below: You can also view Cisco GRE Configuration Example. You can download…
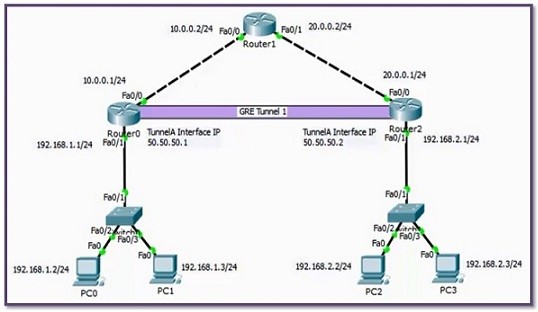
GRE Tunnel Configuration with Packet Tracer (Cisco)
Packet Tracer GRE Tunnel Configuration In this confgiuration example, we will see how to configure Cisco GRE (Generic Routing Encapsulation) Tunnel with Packet Tracer. For our GRE Tunnel Configuration example, we will use the below topology and the given IP addresses. You can DOWNLOAD the…
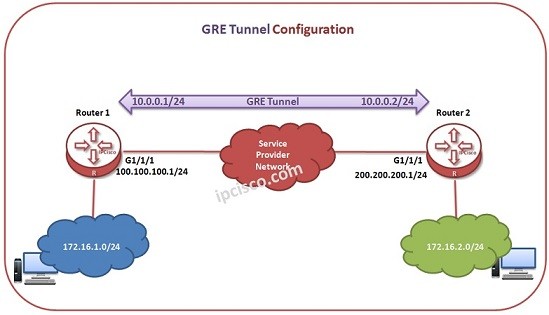
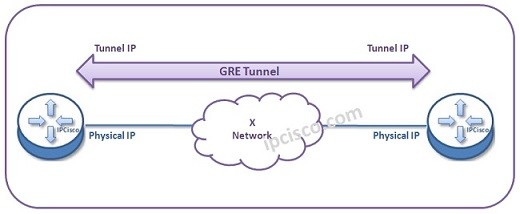
GRE Tunnel Overview
GRE (Generic Routing Encapsulation) GRE (Generic Routing Encapsulation) is the mechanism that encapsulate one protocol in another protocol and provides connection between the nodes. This is done basically IP over IP. A Service Provider Network or Internet is used for GRE (Generic Routing Encapsulation). GRE…
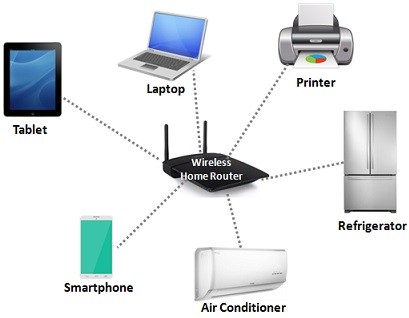
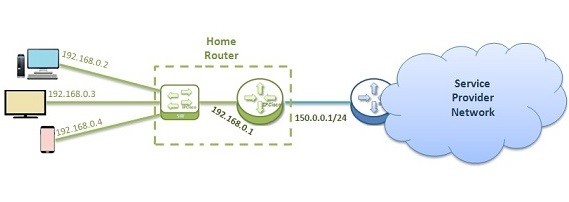
Home Network IP Address Allocation and Internet Connection
The Internet Connection of our home's need some basic devices, protocols and steps. In this article, we will see how our small networks connect to the Internet. For detailed explanation of the network protocols or concepts here, you can check the related article on ipcisco.com.…
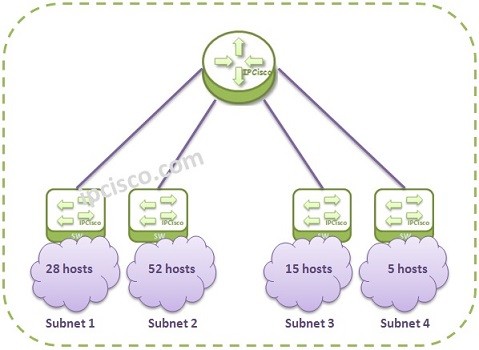
IP Subnetting and Subnetting Examples
IP Subnetting As we talked about before, there are two parts in an IP Address. One for them is Network part and the another is Host part. With IP Subnetting, we are adding one more part. This is "Subnet Part". From the Host part,…
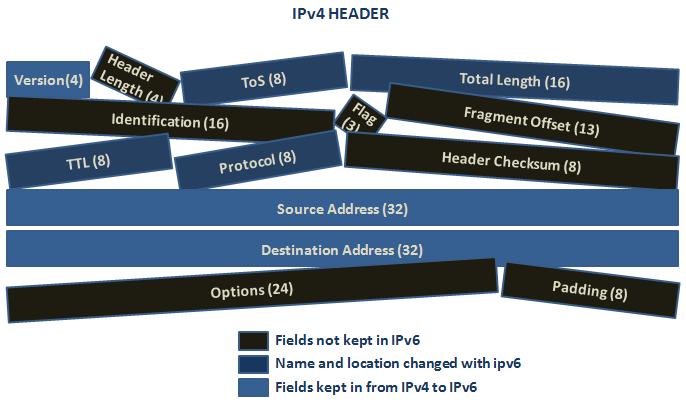
IP Addressing (IPv4)
IPv4 Addressing IP Addressing is one of the key point that a network engineer need to learn first. In this article we will start with the distribution of the IP addresses and we will see all the details of IP Addressing. Here, we will mainly…
IP and Layer 3 Overview
Layer 3 is one of the important Layer of OSI Model. This corresponds Internet Layer of TCP/IP Model. Layer 3 or Internet Layer handles end to end delivery of the data. In other words it provides Routing. Routing is one of the main lessons of…
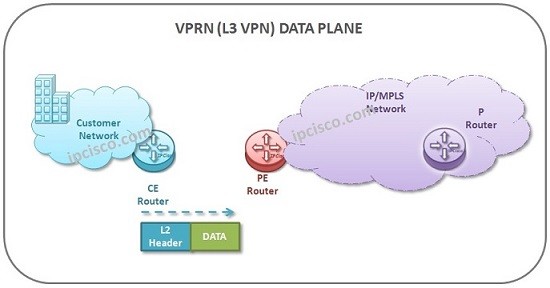
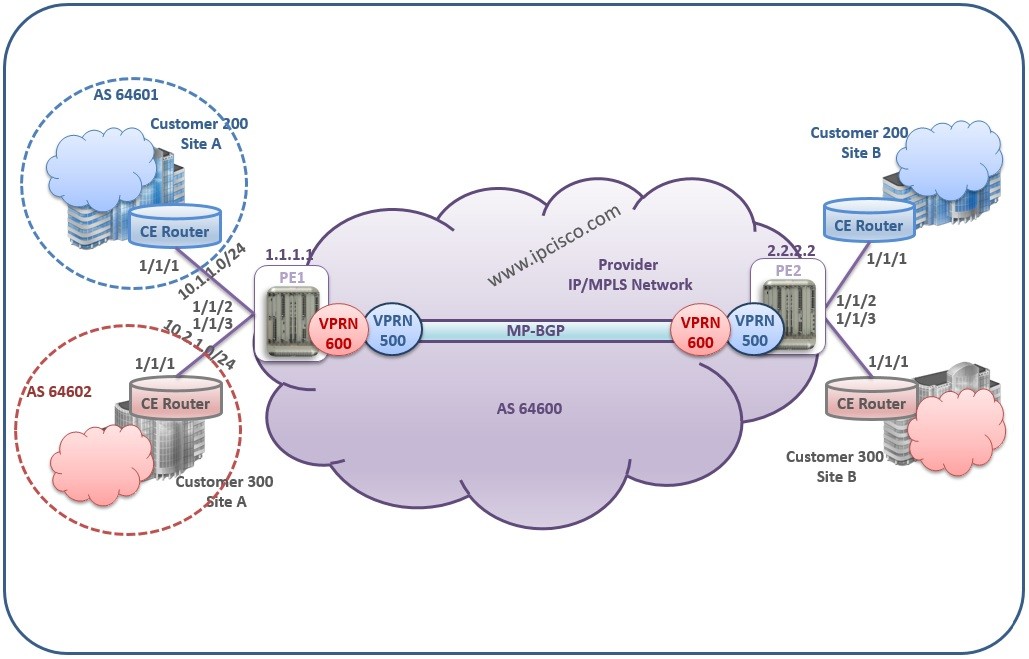
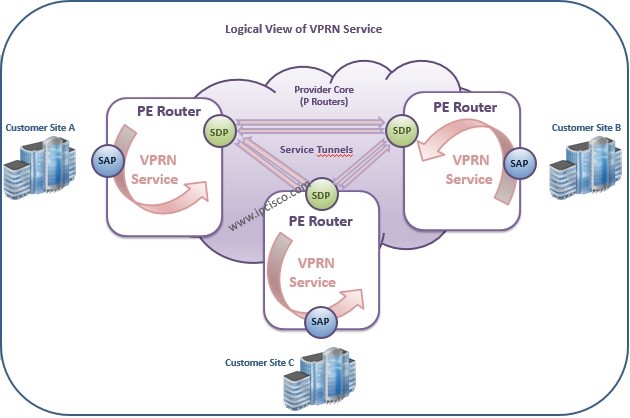
VPRN Data Plane Activities
VPRN Data Plane is the place that the traffic is sent and received generally. As we mentioned before, CE devices are the devices that are not MPLS capable.They do not know labels. So, they send the data to the PE device as unlabeled. PE router…
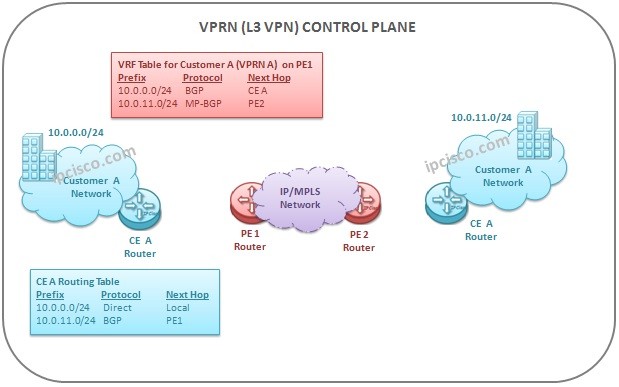
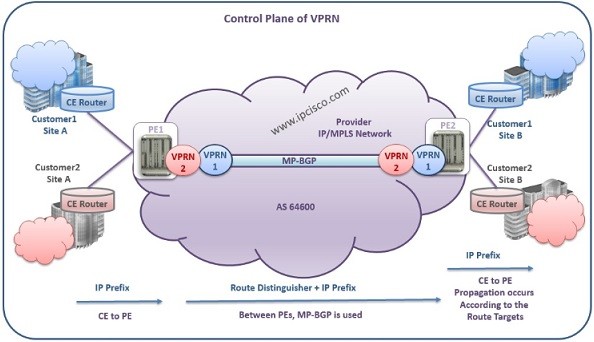
VPRN Control Plane Activities
VPRN Control Plane As a basic definition, VPRN Control Plane is the time that routing exchange activities are done in VPRN Network. These are the necesssary routing information exchange of the VPRN routers in IP/MPLS Network. Beginning with CE devices, PE devices continue this exchange…
VPRN Labels
VPRN is an IP/MPLS Layer 3 VPN Service. So, it uses the same Labels used in IP/MPLS. In MPLS and VPLS articles we have talked about MPLS Labels. Here, we will explain these Labels again for VPRN Service too. Basically, VPRN uses two MPLS labels.…
How Does VPRN Work?
How Does VPRN Work? In this lesson we will learn How VPRN Works and we will focus on VPRN Operation. Basically in a VPRN Architecture, there is a Service Provider Network and there are multiple branches of multiple customers. Service Provider consist of P and…
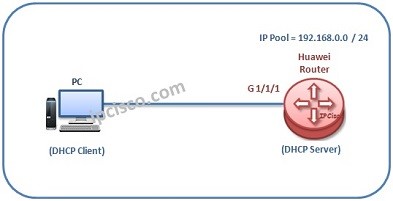
DHCP Configuration On Huawei Routers
Huawei DHCP Configuration In this DHCP example we will configure, Huawei DHCP, a Huawei Router as a DHCP Server. After the configuration, a host device, here a PC, will receive its IP information from DHCP Server Huawei Router. For our DHCP configuration example,…
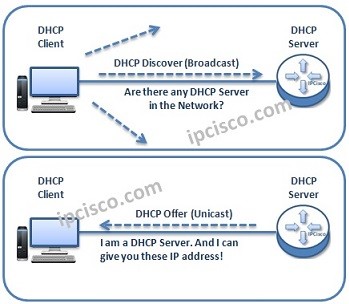
DHCP IP Allocation Operation
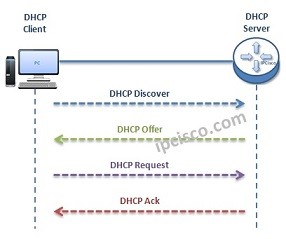
How Does DHCP Achieve IP Allocation Operation? DHCP does its job with Messages like many protocol. Here, as we mentined before, DHCP uses DHCP Messages. Let’s see how these DHCP Messages are used in DHCP IP Allocation Operation. Here, firstly we will explain the main…
DHCP (Dynamic Host Configuration Protocol)
What is DHCP? In a network all the Layer 3 devices need to have an IP address. We can give these IP addresses manually one by one or dynamically and automatically with IP address allocation mechanism, DHCP (Dynamic Host Configuration Protocol. Here, beside IP addresses,…
VPLS Labelling (Tunnel and Service Labels)
As we discussed in the MPLS articles before, for MPLS VPN we need labels. VPLS is also a MPLS VPN Service, so we need to use labels in VPLS too. There are two MPLS Labels used in VPLS. These MPLS Labels are: Outher…
VPLS MAC Learning
VPLS is a Layer 2 VPN Technology. Because of its Layer 2 nature, "MAC Learning" is very important for VPLS. So, how does VPLS learn MAC Addresses? MAC Learning in VPLS is similar to the MAC learning mechansim in an Ethernet Switch. The concept…
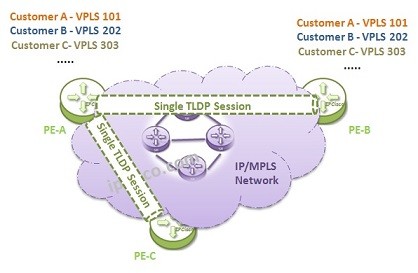
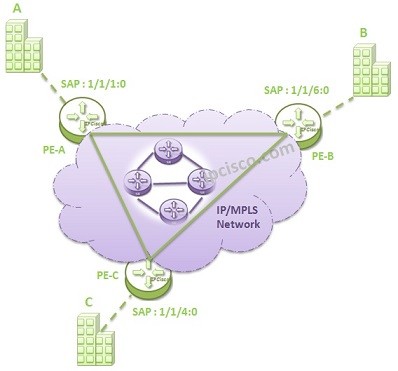
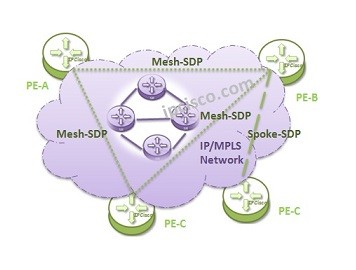
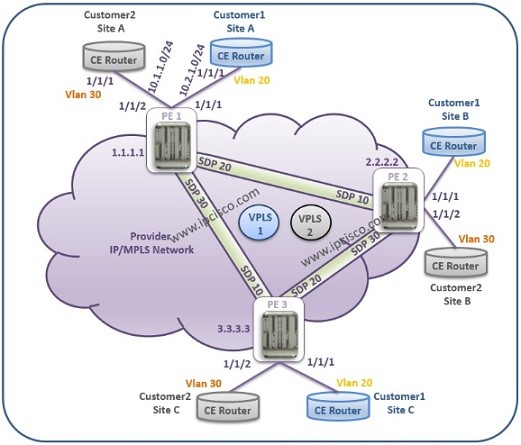
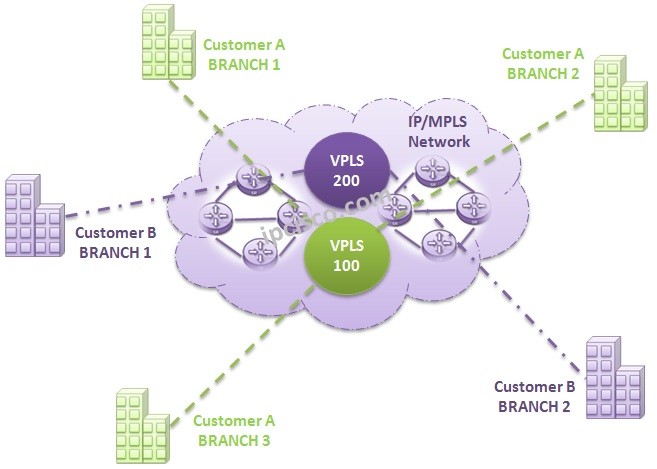
VPLS Topologies
There are different types of VPLS. In other words, there are different VPLS Topologies. In this lesson, we will talk about these VPLS Topo0logies. VPLS can be defined on One Service Router or on Multiple Service Routers. Basically we can divide VPLS into two…
ISIS For IPv6 Configuration Example on Cisco IOS
How to Configure ISIS For IPv6 on Cisco? In this Cisco ISIS for IPv6 configuration example, we will configure ISIS with IPv6 extension configuration commands. For our example we will use the below four-routered topology. Here, we will have 3 different area. There is a…
ISIS for IPv6
Intermediate System to Intermediate System for IPv6 ISIS is one of the important Link-State protocols. With entrence of IPv6 to the network world, ISIS also need to uptade itself for this new Routed protocol. So, ISIS for IPv6 is developed. Basically, ISIS for IPv6 is…
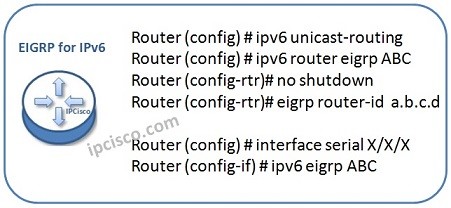
EIGRP For IPv6 Configuration On Cisco IOS
EIGRP for IPv6 is one of the most used routing protocol with IPv6. In this example, we will see how to configure EIGRP for IPv6 on Cisco routers. For our example, we will use the topology below. Here, simply we have four routers connected serially…
EIGRP for IPv6
We can define “EIGRP for IPv6” as the enhancements that is done in EIGRP for IPv6 support. Basically, EIGRP protocol is the same protocol but it has some additional properties at this time. Differences of EIGRP and EIGRP for IPv6 EIGRP and EIGRP for IPv6…
RIPng Configuration Example on Cisco IOS
RIPng Configuration On Cisco IOS The configuration of RIPng is a little different from its predecessor, RIPv2. First of all, RIPng is IPv6 avare routing protocol and before RIPng configuration, IPv6 must be configured in your system. In this article, we will configure RIPng according…
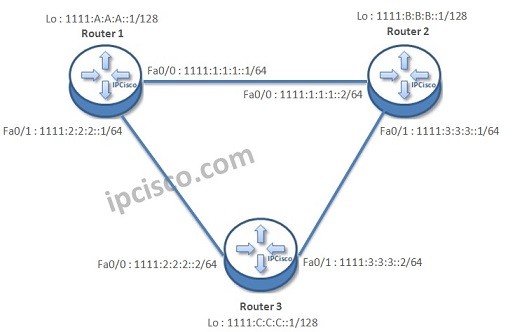
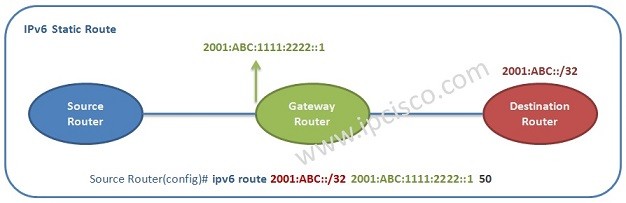
IPv6 Static and Default Route Configuration on Cisco IOS
IPv6 Static Route Configuration on Cisco IOS As you know, static route is the route that you manually define on a router.This is done when we do not want to use Routing Protocols for small part of a network. Or, in large networks some small…
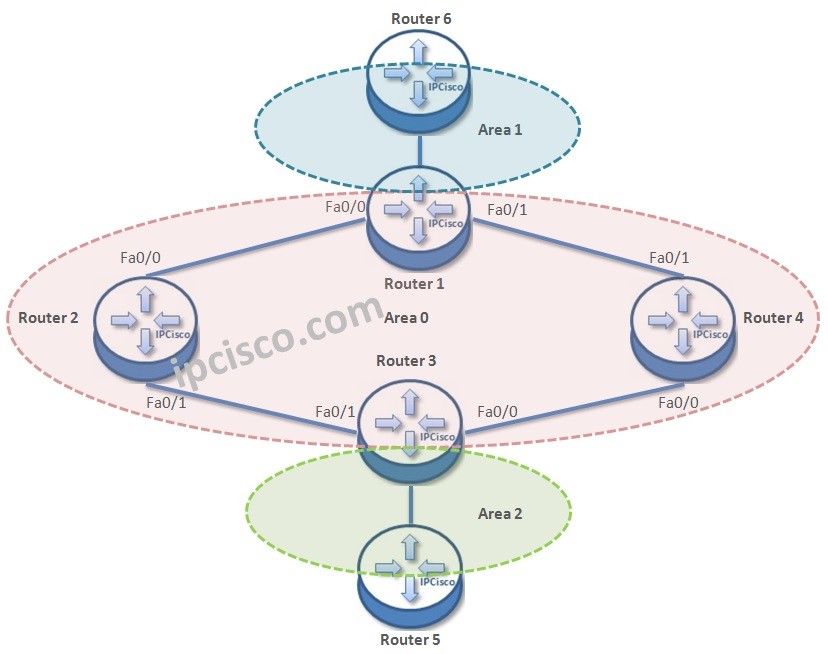
OSPFv3 Configuration Example on Cisco IOS
OSPFv3 Cisco Configuration OSPFv3 is the IPv6 cabaple version of OSPF. The previous version of OSPF was OSPFv2. OSPFv2 is for IPv4. Here, we will configure OSPFv3 for the below topology. As you can see, there are three areas and six routers in this topology.…
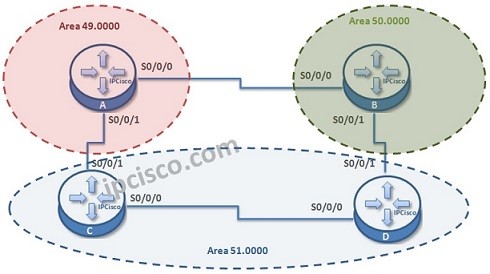
ISIS Configuration Example on Cisco IOS
In this Cisco ISIS configuration example, we will configure an ISIS domain and see how to establish ISIS Routing. For our example we will use the below four-routered topology. Here, we will have 3 different area. We are using multi area model to show you…
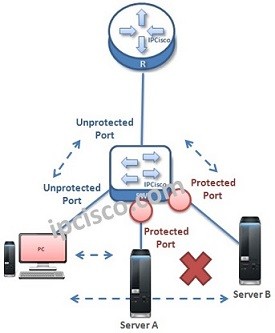
What is Protected Port ?
Protected Ports are one of the security mechanisms used on switch world. By default all the switch ports are unprotected and equal. But with Protected Port Configuration, some ports are filtered an restricted to access each other. If you configure a port as protected, data…
Private VLAN Cisco Configuration Example
Cisco Private VLAN Configuration Example For Private VLAN configuration, we will do a configuration example with one switch and one router. Here, we will use the same topology that we have used before for Private VLAN overview. Our topology, ports and VLANs will be like…
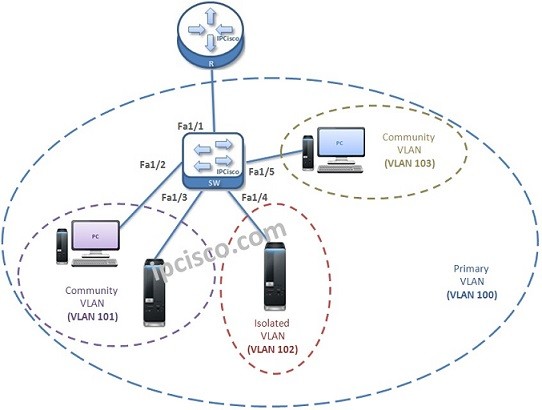
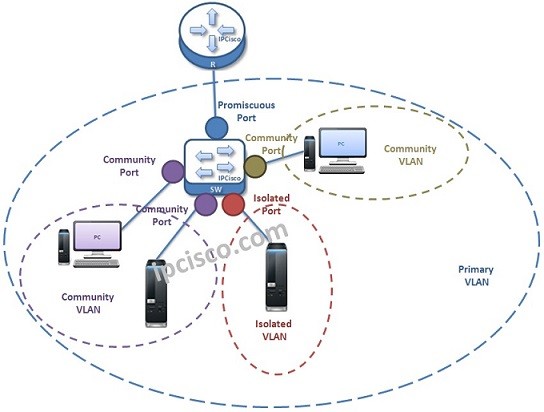
Private VLANs (pVLANs)
VLANs used to divide the Broadcast Domains. With this division, different departments, networks are isolated each other and become another Broadcast Domain. Sometimes, this separation is not enough and additional separation is needed. Private VLANs (pVLANs) are used at these times. Basically we can say…
VLAN Configuration on Huawei Switches
How to Configure VLAN on Huawei Switches? VLAN Configuration on Huawei switch is not too different than Cisco VLAN Configuration. But there are some differences. In this lesson, we will see the VLAN configuration steps on Huawei devices. For our example, we will use the…
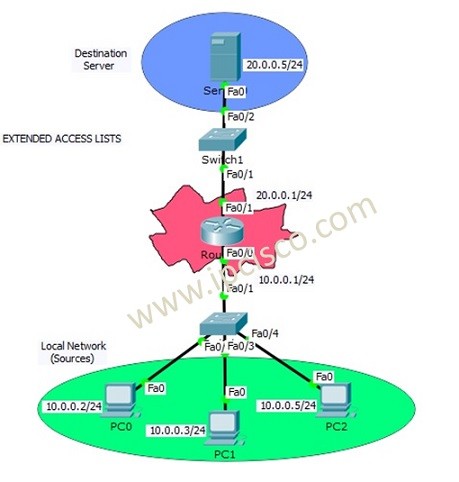
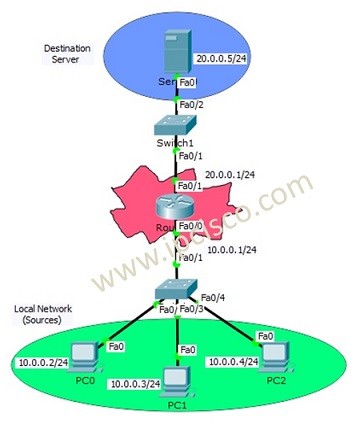
Extended Access List Configuration With Packet Tracer
Packet Tracer Extended Access Lists Configuration We have learned Access Control Lists overview and Standard ACL Configuration at the previous lessons. In this lesson we will focus on Cisco Extended ACL Configuration with Cisco Packet Tracer. We will use the below topology for our packet…
Standard Access List Configuration With Packet Tracer
Packet Tracer Standard Access List Configuration In this lesson we will see Cisco Standard ACL Configuration and how to configure Standart Access-List in Packet Tracer. There are three types Access Contol Lists in common. These access list types are : Standard Access List Extended Access…
Basic Cisco Router Security Configuration
How to Secure a Cisco Router Basically? Security is an important concern for a network engineer. How can a network engineer provide security of a router? In this Basic Cisco Router Security Configuration lesson, we will talk about, how to Secure a Router. We sill…
Traffic Engineering, RSVP-TE Path Manuplation and Constraints
Traffic Engineering is one of the most important routing lessons. With traffic engineering, as a network engineer you are directing your network traffic according to some constraints. By directing the traffic, you provide efficient usage of resources and become proactive for any congestion and packet…
IPv6 Routing Protocols – Part 4 (RIPng)
RIPng (RIP Next Generation)is the IPv6 available next level protocol of RIPv2. In modern large networks, generally RIP is not used and also RIPng. But as a basic protocol, it is still used in many small networks. Basically, the characteristics of these two version is…
COMPARISON OF TOP FOUR VENDORS’S COMMAND LINE
In IP world, there are many Network Equipment Vendors. But some of these Network Equipment Vendors are very Common in Network World and Well Known. These Well Known Vendors are : - Cisco - Juniper - Nokia - Huawei I have prepared a cheat sheet…
EIGRP Configuration With Packet Tracer
Packet Tracer EIGRP Configuration EIGRP (Enhanced Interior Gateway Routing Protocol), is a Cisco Proprietary Hybrid Routing Protocol. The configuration of EIGRP is similar to other Routing Protocols. In this example, we will configure EIGRP on Packet Tracer with Cisco Routers.. With this EIGRP…
EIGRP - Part 4 (Other EIGRP Properties)
Key Configurations on EIGRP EIGRP is an Enhanced Dynamic Routing Protocol that provide many methods for a good Routing Protocol implementation. In this lesson, we will focus on some of the key methods of EIGRP and we will learn these key methods with many EIGRP…
EIGRP - Part 3 (EIGRP Packet Types and Neighbourship)
EIGRP Packet Types EIGRP (Enhanced Interior Gateway Routing Protocol) uses EIGRP Messages to establish and maintain the EIGRP Neighborship. In other words, it uses different EIGRP Packet Types for its operations. EIGRP uses Five Packet Types for as EIGRP Messages. These EIGRP Packet Types…
EIGRP - Part 2 (EIGRP Tables)
EIGRP Tables EIGRP uses different tables for its Routing Operation. Mainly, three types of EIGRP Tables are used in EIGRP (Enhanced Interior Gateway Routing Protocol). What are the EIGRP Tables? These EIGRP Tables are given below: Neighbour Table Topology Table Routing Table EIGRP Table Types …
EIGRP - Part 1
EIGRP Overview EIGRP Protocol is one of the most used Dynamic Routing Protocol as IGP (Interior Gateway Protocol). Especially it is used for Routing purpose inside the networks that is mostly consist of Cisco devices. EIGRP (Enhanced Interior Gateway Routing Protocol) is a Hybrid Routing Protocol that show both Distance Vector and Link-State Routing Protocol properties.…
RSTP Configuration on Packet Tracer
Packet Tracer RSTP Configuration As you know, STP (Spanning Tree Protocol) is the key protocol of Switching world. With STP, link redundancy is provided and switching loops are avoided. STP has different versions. One of the STP version is RSTP (Rapid Spanning Tree Protocol). Like its…
STP Portfast Configuration with Packet Tracer
Packet Tracer STP Portfast Configuration In STP (Spanning Tree Protocol) there are different states. These STP states are: Blocking State, Listenning State, Learning State and Forwarding State. With STP Portfast, Listenning State and Learning State are bypassed. With this configuration, ports rapidly goes to Forwarding…
Switch Virtual Interface Configuration on Packet Tracer
Theorically switches work in Layer 2 (Layer 2 switches). When you talk about switches, generally you do not think IP addresses. One of the ways that make a switch IP available is, configuring Switch Virtual Interfaces (SVI). Switch Virtual Interfaces (SVI) is basically, an IP…
Inter VLAN Routing Configuration on Packet Tracer (Router on Stick)
Router on Stick Configuration on Packet Tracer VLANs are the virtual LANS that provide divide your big network, into smaller pieces. Many companies use to divide their networks into different departments. We have discussed the basic logic of VLANs in the previous articles.As you…
Routing With IS-IS Protocol - Part 5 (IS-IS versus OSPF)
IS-IS Protocol and OSPF have some similarities and differences. Lets firstly check the similarities of these two protocol one by one: - IS-IS Protocol and OSPF are both Link-State Interior Gateway Protocols. - IS-IS Protocol and OSPF are both uses Dijkstra SPF (Shortest Path First)…
Routing With IS-IS Protocol - Part 4 (IS-IS Adjacency)
There are three types adjacency in IS-IS Protocol.These are: - Level 1 routers form L1 adjacency with L1 and L1/2 Routers - Level 2 routers form L2 adjacency with L2 and L1/2 Routers - Level 1/2 routers form L1/2 adjacency with L1/2 Routers There is…
Routing With IS-IS Protocol - Part 3 (IS-IS Packet Types)
IS-IS Protocol uses L2 encapsulation Ethernet 802.3/802.2. It do not use Ethernet II. Ethernet II is used for IP traffic. IS-IS Protocol exchanges protocol information by using Link-State PDUs (Protocol Data Units). There are four types of PDU packets in IS-IS Protocol. These IS-IS packets…
Routing With IS-IS Protocol - Part 2 (IS-IS Addresses)
IS-IS (Intermediate System to Intermediate System) Protocol was developed as a OSI network protocol, not TCP/IP. So, normally IS-IS Protocol not uses IP address, but it uses NET (Network Entity Title) addresses. Let’s check this address issue a little. In IS-IS Protocol, NSAP (Network Service…
Routing With IS-IS Protocol - Part 1
What is Routing Protocol IS-IS ? In this lesson, we will focus on one of the Routing protocols. We will learn What is ISIS Protocol? Why We use this protocol. Here , we will focus on the theorical lessons of this protocol. We will learn…
Link Aggregation on Cisco IOS XR
Link aggregation, LAG, Bundle, EtherChannel, what ever you say, they have the same logic in real. So, the configuration logic of Link Aggregation (LAG) is not different than Ether Channel logic on Cisco devices that run Cisco XR software. Here, again the bundle is created…
Cisco VPLS Configuration
In this lesson, we will configure VPLS on Nokia Service Routers. Before any Service configuration, our IGP configuration must be done and the network must be converged. We had talked about this preparations in the previous articles. In this article, we will focus on VPLS…
VPLS Versus h-VPLS
VPLS (Virtual Private LAN Service) and h-VPLS (Hierarhical VPLS) has some common and different properties. So they have different aadvantages and disadvantages. In this article, we will focus on the comparison of these two concepts and we will see Hierarhical VPLS versus VPLS. The most…
Hierachical-VPLS (H-VPLS)
H-VPLS (Hierarchical VPLS) is the more scalable version of VPLS. Basically, H-VPLS has some architectural difference than flat VPLS. You can also view the lesson, that we have talked about Hierarhical VPLS versus VPLS. VPLS Architecture, Flat VPLS You can also view…
BGP Path Attributes - MED
BGP MED (Multi Exit Discriminator) Attribute is the BGP Path attribute which provides information to the external neighbours, about how to come their Autonomous System. This is opposite of Local Preference. BGP Local Preference Atribute says to the internal neighbours, “How to Exit AS”. BGP…
BGP Path Attributes - Origin
BGP Origin Attribute informs the Autonomous Systems (AS) about the originator of that route. It is a Well-Known Mandatory BGP Path attribute like AS Path Attribute and Next Hop Attribute. BGP Origin Attribute is supported in all BGP implementations and in all BGP Update packets…
BGP Path Attributes - AS Path
BGP AS Path Attribute AS Path Attribute is another Well-Known and Mandatory BGP Path Attribute. Here, as we have discusssed before, Well-Known means “it is supported by every BGP implementation” and Mandatory means “it must be included in every route entry”. AS Path Attribute is…
BGP Path Attributes - Local Preference
What is BGP Local Preference Attribute? In BGP Path selection algorithm, if your device is a different vendor product (not Cisco), the first BGP Path Attribute that is taken into account during path selection is Local Preference attribute. Local Preference is not a vendor specific…
BGP Path Attributes - Weight
BGP Path Attributes - Weight Attribute Weight Attribute is a Cisco proprietary BGP Path Attribute that is the first step in the BGP Best Path Selection Algorithm. In Cisco devices, BGP firstly check the Weight Attribute value and prefer the Highest Weight Attribute value. Then…
Neighbour Discovery Protocols - Part 6 ( LLDP Cisco Configuration)
In this configuration lesson, we will focus on Cisco LLDP Configuration. To understand LLDP better, let’s check the configuration of LLDP on the Cisco IOS. The most important commands related with LLDP configuration is showed below. LLDP Configuration TopologyLLDP is disabled by default. To…
Neighbour Discovery Protocols - Part 5 ( LLDP-MED )
As a standard and open protocol, LLDP is a good protocol. After the development of LLDP, some of the additional properties needed especially for Voice Over IP (VoIP). So LLDP extended. The extended version of LLDP is LLDP-MED (Link Layer Discovery Protocol - Media Endpoint Discovery).…
Neighbour Discovery Protocols - Part 4 (CDP Configuration with Packet Tracer)
Packet Tracer CDP Configuration As we have talked about in the previous lesson, CDPis a Cisco proprietary Neighbor Discovery Protocol. In this article, we will discuss how to configure CDP in Cisco IOS, we will learn CDP Cisco Configuration. LLDP is a standard neighbour discovery…
Neighbour Discovery Protocols - Part 3 ( CDP )
CDP (Cisco Discovery Protocol) is a Cisco specific Neighbour Discovery Protocol works on Layer 2. CDP (Cisco Discovery Protocol) is also licensed to run on some network devices of other vendors. There is also a standard Neighbor Discovery Protocol named LLDP that works on all…
Neighbour Discovery Protocols - Part 2 ( LLDP )
LLDP (Link Layer Discovery Protocol) is a Standard Neighbour Discovery Protocol that is used by all vendors. Like all other Neighbour Discovery Protocols like Cisco CDP, LLDP works on Layer 2 (Data-link Layer). By using this Neighbor Discovery Protocol, directly connected neighbours are discovered. You…
Neighbor Discovery Protocols - Part 1
Neigbour Discovery Protocols provides directly connected devices to discover and collect information about each other. Network devices can provide directly connected neighbour device’s identification, configuration and any capabilities. Neighbour Discovery Protocols work on Layer 2. There are different Neigbour Discovery Protocols for different…
RIP Configuration With Packet Tracer
Packet Tracer RIP Configuration In this RIP Cisco Configuration lesson, we will focus on how to configure RIP (Routing Information Protocol) on Cisco Routers. Generally in all network courses, RIP is used to explain routing protocol configuration basically. This is because of its basic configuration.…
Routing Information Protocol (RIP)
RIPv2 Overview RIP (Routing Information Protocol) is a Distance Vector Routing Protocol. It is the simplest Routing Protocol. So, Routing with RIP is generally used for small networks. For large networks and WAN links, it is inefficient. In this article, we will focus on RIPv2,…
How Will Be Our Lifes With IoT ?
IoT (Internet of Things) will create values in many parts of our lifes. From home to work, city to urban IoT will provide us many user friendly and effective applications. With IoT, world will enter a new era in technology. So what are IoT Benefits?…
The Future Technolgy : Internet of Things (IoT)
IoT is the abbreviation of Internet of Things. And Internet of Things is basically connecting IP available devices (even if they are not computers) over internet and letting them to talk eachother. By doing this, IoT (Internet of Things) aims to provide a big network…
Packet Tracer VLAN Configuration Example
Packet Tracer VLAN Configuration As an example, you can see a VLAN topology below. In this topology, 2 Cisco Catalyst 2950-24 switches and 6 PCs are used. Packet Tracer VLAN Topology ExampleYou can DOWNLOAD the Cisco Packet Tracer example with .pkt format at the…
How to Configure Cisco VLANs
Cisco VLAN Config Commands In this lesson we will learn How to Configure VLANs on Cisco devices. Here, we will see the necessary commands for Cisco VLAN Configuration. You can also check VLAN Configuration Example on Packet Tracer lesson to learn and practice more on…
DTP and VLAN Frame Tagging protocols ISL, dot1.q
VLAN Frame Tagging Protocols (ISL and dot1.q) In this lesson, we will learn VLAN Frame Tagging Protocols detailly. In the next lessons, you can also check Cisco VLAN Configuration Examples. What are these VLAN Frame Tagging Protocols? Let's see each of them. There are two…
VLAN Port Assignment and VLAN Port Types
In this lesson, we will focus on some of the key lessons of VLANs. We will learn how to assign ports to VLAN, VLAN Port types and VLAn Tagging. Static and Dynamic VLAN Assignments VLANs can be assigned statically and dynamically. Static configuration is more…
VLANs (Virtual Local Area Networks)
What is a VLAN? In this lesson, we will talk about one of the key lessons in networking, especially in switching. We will explain VLAN definition and we will answer the question what is a VLAN? In the following lessons, we will learn the details…
Nokia 5620 SAM (Service Avare Manager)
Nokia 5620 Service Aware Manager (SAM) is the network and service management application of Nokia. It is generally used on service providers’s big netwoks consist of Nokia devices like 7950 XRS, 7750 SR, 7450 ESS and so on. Nokia 5620 Service Aware Manager (SAM) uses…
BGP Path Attributes and BGP Administrative Distance
BGP Path Attributes BGP uses BGP Path Attributes to determine the Best Path to a destination. According to BGP Best Path Algorithm, BGP Path Attributes are used to determine the BGP Best Path selection. With these Path Attributes, network administrators can manage the BGP Traffic…
BGP - Part 2 (BGP Peers, BGP Sessions, BGP Messages)
What is BGP peer? To use BGP, the neighbourship between the BGP routers must be established. You can use the statement BGP neighbour or BGP peer for this establishment. There are two types of BGP peer. These are iBGP(interior BGP) peer and eBGP(exterior BGP) peer.…
BGP - Part 1
AS you know there are two types of routing protocols in general. These are IGP(Interor Gateway Protocols) and EGP(Exterior Gateway Protocols). In the previous posts we have talked about some of IGP protocols. In this post, we will talk on EGP. EGP is the abbreviation…
BGP - Part 3 (IBGP, IBGP Topologies and EBGP)
In the previous post, we have talked about BGP generally. In this post we will handle IBGP and EBGP detailed. IBGP and EBGP IBGP (Internal Border Gateway Protocol) * BGP, which is used in the same Autonomous System. Neighborship is established with the peer…
ECMP (Equal Cost Multi Path)
If the total IGP cost to a destination are same for two path, these paths are called Equal Cost Multi Path. Normally if there are two path that have same IGP cost, in Alcatel-Lucent Service Routers, lower interface wins and the traffic goes through it.…
LDP Configuration on Nokia Routers
To do an LDP Configuration Example , we will use the below basic topology. Here, we will configure these two routers to become an LDP peer and establish an LSP session. LDP Configuration Example Topology Configuration on Router A A:RouterA>config>router # interface “to_RouterB” address 10.0.0.1/24…
MPLS Label Distribution Protocol, LDP - Part 2
After LDP session establishment, labels are distributed from the Tail-End router to the Head-End router for each prefix. This process occurs at the opposite direction of the data plane. At the data plane the traffic flow goes form the Head-End to the Tail-End. But label…
MPLS Label Distribution Protocol, LDP - Part 1
LDP (Label Distribution Protocol) is one of the two label exchange protocols of MPLS. The other is RSVP (Resource Reservation Protocol). And there is also one more, Cisco specific protocol, TDP(Tag Distribution protocol). In this article, we will talk abbout the LDP. And the examples…
LTE Advanced (LTE-A) Features
As you know after LTE, LTE-A (LTE Advanced) is the next step of mobile technology. In this article, I will try to explain this LTE-A (LTE Advanced) features basically.Let's start ;) CA (Carrier Aggregation) Carrier Aggregation is the most important feature of 3GGP Release 10…
4G – LTE (Long Term Evolution)
As you know mobile telecommunication has evolved for years. With this evolution, new network elements were included or the existing ones were upgraded. Startig with 2G GSM technology, the evolution has continued orderly with: - 2.5G GPRS, - 2.75 EDGE, - 3G UMTS, - 3.5G…
OSPF Area Types on Packet Tracer (NSSA and Totally NSSA)
Not So Stubby Area (NSSA) Not So Stubby Area name is the most funny name in network world, I think : ) Funny and useful. With NSSA, the External LSAs (Type 5) that is not accepted by Stub Areas, accepted as Type 7. Normally, NSSA…
OSPF Area Types on Packet Tracer (OSPF External Routes)
As you know External Routes are the routes that provide connection to the other networks working with different IGP. Here, we are talking about OSPF and the networks routed by another routing protocol will be External for us. In this post, we will use the…
OSPF Area Types on Packet Tracer (Standard Area, Backbone Area)
In this article series we will concentrate on OSPF Area Types and their configuration examples on Packet Tracer. You can DOWNLOAD the Packet Tracer example with .pkt format HERE. As you know from the previous posts, OSPF has 6 different areas. These areas are: -…
VPRN Configuration on Nokia Service Routers
How to Configure VPRN on Nokia Service Routers? In this post, we will focus on the configuration of VPRN Service on Nokia (Alcatel-Lucent) Service Routers. Here, We will use Alcatel-Lucent 7450 Service Router as a PE Router. Our Provider Routers will be Nokia (Alcatel-Lucent) 7750…
VPRN (Virtual Private Routed Network)
VPRN Overview VPRN (Virtual Private Routed Network) is a Multipoint-to-Multiponit Layer 3 VPN Service that connects multiple branches in a single Logical Routed Architecture over IP/MPLS network of a Service Provider. This is called Layer 3 VPN generally, but Nokia (Formerly Alcatel-Lucent) defines this…
VPLS Configuration on Nokia Service Routers
In this lesson, we will configure VPLS on Nokia Service Routers. Before any Service configuration, our IGP configuration must be done and the network must be converged. We had talked about this preparations in the previous articles. In this article, we will focus on VPLS…
VPLS (Virtual Private LAN Service)
What is VPLS? Nokia VPLS (Virtual Private LAN Service) is a Multipoint-to-Multipoint Layer 2 VPN Service that connects multiple branches of a Customer, in a single logical switched architecture over Service Provider IP/MPLS network. Service Provider IP/MPLS network is our transit network here. Different brances…
Network Preparation for Nokia L2 VPN and L3 VPN Services
Network Preparation Before L2 VPN and L3 VPN Service Configuration In the first part of this article series we talked about service terms and some steps about service creation and the preparing the network for service creation. Here, in this article, we will talk about…
Nokia L2 VPN and L3 VPN Services
Nokia Layer 2/3 VPN Services In this article we will talk about Nokia VPN Service Types used in Nokia Service Routers. Why Nokia use "Service Router" term for their service routers? This is because, different Nokia VPN Services are given to customers through these routers. …
Nokia VPN Service Terms and Creation Steps
Service perspective is a Nokia's view for providing internet and VPN services to the customers. In other words Nokia MPLS VPN is called as Services. There are many services in Nokia Service Routers. For this services some configurations must be done under Nokia Service Routers.…
Nokia VPN Services Tunnel Structure
Nokia VPN Services Tunnel Structure In this lesson we will talk about the Tunnels used for VPN Services that is set up via MPLS (Multiprotocol Label Switching). Here there are some key points that you must know to understand VPN Service structure well. Think…
Link Aggregation Configuration on Nokia Routers
Link Aggregation (LAG) Configuration on Nokia Routers In the previous article we focused on how to configure Link Aggregation on Cisco and Juniper devices. Here you will learn How to Configure Nokia Link Aggregation on Nokia 7750 Service Router. Link Aggregation on (Alcatel-Lucent)…
Link Aggregation – Part 3 (LACP Configuration on Juniper Devices)
How to Configure LACP on Juniper Routers We have talked about LACP in the previous articles on Cisco Routers. Here we will focus on how to do LACP Configuration on Juniper devices on ethernet links. We will learn LACP Configuration on Juniper. As you…
LACP Configuration on Cisco Devices
We have learned LACP and Link Aggregation before detailly and in this article we will focus LACP Cisco Configuration. We will make a link aggregation protocol with two ports in one bundle. You can use more port up to 8 ports in Cisco devices. …
Link Aggregation – Part 1 (Link Aggregation Control Protocol, LACP)
Link Aggregation Control Protocol (LACP) Link Aggregation is bundling two or more links as one logical link for increasing bandwidth and availability. This can be done by one of the two protocols . One of them is the Cisco proprietary PAgP and the other…
Common Cisco Router Configuration on Packet Tracer
Basic Cisco Router Configuration In this Basic Cisco Router Configuration lesson, we will see how to configure a Cisco router basically with the help of Packet Tracer. This CCNA lesson will be an entrance to routers for a Cisco router newbie. Here, we will see Basic…
STP (Spanning Tree Protocol) Example on Packet Tracer
Packet Tracer STP Configuration In this post, instead of detaily talk about STP (Spanning Tree Protocol), we will focus on a basic Switching Loop topology and how STP mechanism helps to avoid this Switching Loop. You can DOWNLOAD the Packet Tracer example with .pkt format…
MPLS RSVP-TE Configuration on Nokia Routers
Prerequisites and Configuring RSVP-TE - Configure IGP. - Enable MPLS context. - Enable RSVP context. - Configure interfaces for MPLS ( automatically RSVP). Let’s check these step sone by one. Configuring IGP (Routing Protocol) is required for routing between the nodes. This is the first…
MPLS, RSVP-TE - Part 1
RSVP-TE(Resource Reservation Protocol-Traffic Engineering) is the enhanced RSVP for MPLS. RSVP-TE is not a real routing protocol, but it works with routing protocols. For RSVP-TE, bidirectional flow is required. To provide this, there must be two RSVP sessions. Because RSVP-TE is unidirectional. RSVP-TE brings some…
MPLS Label Distribution Protocol, LDP – Part 5 (Export and Import Policy, Prefix Aggregation)
LDP and Export Policy By default ALU only distribute a label only for its system addresses. To distribute additional other local prefixes, “export policy” is used. You can find an “export-policy” example below: A:>config router policy-options begin prefix-list “interface1” prefix 10.0.0.6/24 exit policy-statement “LDP_Export_Policy1” entry…
MPLS Label Distribution Protocol, LDP – Part 6 (T-LDP)
As we talked about, LSRs(P routers) are not service avare, they do not know anything about services. So they use only the outer label. But PE routers are service avare and they use outer and inner label together. With inner label, they classfy the different…
MPLS Label Distribution Protocol, LDP – Part 7 (CR-LDP)
Before discussing the CE-LDP, lets explaint “constraint-based routing” term. "Contraint-based Routing" is the routing which in which the routing process is done according to some constraints. Both QoS-based routing and policy-based routing belong to Contraint-based Routing. As you know these routing include QoS constraints or…
Switch Port Security Configuration with Cisco Packet Tracer
In this article, we will focus on detailed Port Security Cisco Configuration. For our Cisco Port Security Configuration, we will use the below topology. In this topology we will make examples for the configuration cases on Port Security. You can DOWNLOAD the Packet Tracer…
Switch Port Security - Part 1
Port Security is the security mechanism used in switches. With this mechanism, a specific port of a switch can be protected with undesirable access. Here, we will learn the theory of this lesson. We will focus on the properties of this mechanism and some of…
BGP Next Hop Self Command
In this post, we will talk about an important and mostly used command of BGP. This command is used under the BGP process in the router and the usage is like below: neighbor {ip-address | peer-group-name} next-hop-self In the routing, route advertisement is a common…
BGP Configuration Example with Packet Tracer
Packet Tracer BGP Configuration Example To understand BGP (Border Gateway Protocol) better, we will make a basic Packet Tracer BGP Configuration example. Because of the limited numbers of commands available on Packet Tracer, we will practice a very basic configuration for our BGP Config Example.…
Ping Command (Pinging Peers)
Ping Command and Ping Command Options Whenever other engineers see network engineers during troubleshooting, they think that, network engineers only ping from one node to another. But as you know a network engineer is more than a pingman :) This command is a basic but…
MPLS Protection and Restoration – Part 5 (Fast Reroute Protection Types)
Both One-to-One and Facility Backup can protect different network elements. And these can be achieved by two ways: - Node Protection : Protect against the failure of the next downstream router. The upstream router before the failure node establishes a protection tunnel that goes around…
MPLS Protection and Restoration – Part 4 (Local Protection, Fast Reroute)
The goal of the protection is minimizing the down time. To do this, protection must be done near to the failure. Local protection does this. By doing this types of protection, it avoids using entire path protection. Local protection reroutes the traffic rapidly around the…
MPLS Protection and Restoration – Part 3 (Path Diversity in Secondary Paths)
As we say in the following articles, while using Secondary LSP-Paths, sharing links between Primary and Secondary LSP-Paths must be avoided. We can say this term "Path Diversity".There are some methods to achieve Path Diversity. These methods are: Using Full Strict hop LSP-Paths Admin Groups…
MPLS Protection and Restoration – Part 2 (End-to-End Protection, Secondary Paths)
There are some different types traffic protections. In general we can divide these types into two groups. End-to-end Protection and Local Protection. End-to-end Protection is using Secundary LSP-Paths as a backup, beside Primary LSP-Path. Local Protection is the mostly used MPLS recovery mechanism, MPLS FRR…
MPLS Protection and Restoration – Part 1
As you know, we can prioritize some of the traffic with MPLS-TE because of their nature. The high priority can be given to the voice and video traffic. Because they are fragile traffic types. During a failure normally these real time traffics send first and…
MPLS Protection and Restoration – Part 9 (MPLS Convergence Factors)
After the link failure in MPLS network, there are some actions need to be done orderly for MPLS recovery. This actions need to converge the MPLS network again. These MPLS Recovery steps are: - MPLS Recovery Failure Detection : Detecting the failure point - MPLS…
MPLS Protection and Restoration – Part 8 (Actions After the Failure)
What Happens After the Failure Recovered By Fast Reroute (FRR) ? After detecting the failure in an MPLS network, in Fast Reroute (FRR) mechanism, PLR switches the traffic to the protected tunnel. At the same time it sends a PATH ERR message to the Head-End.…
MPLS Protection and Restoration – Part 7 (Verification Commands on Alcatel-Lucent Routers)
In the Alcatel-Lucent 7750 Service Routers, we can verify the Secondary LSP-Path configuration with the following commands. Verifying secondary LSPs use the following commands: show router mpls lsp show router mpls lsp path If Standby Secondary LSP-Path, the Primary andthe Secondary is up. if Non-Standby…
MPLS Protection and Restoration – Part 6 (RSVP Objects Used for MPLS Fast Reroute)
There some RSVP Objects used in Fast Reroute(FRR). Beside this, RSVP-TE extend for this purposes. There are also some extensions on RSVP-TE for automatic signalling in protection tunnels.So some additional objects and flags are coming for FRR. These two additional objects are FAST_REROUTE and DETOUR…
MPLS Protection and Restoration – Part 13 (Juniper Configuration Samples)
[edit] user@R1# edit protocols mpls label-switched-path lsp-path-name [edit] user@R1# edit protocols mpls label-switched-path lsp2-A-to-B To configure node-link protection for the LSP... [edit protocols mpls label-switched-path lsp-path-name] user@R1# set node-link-protection To configure link protection for the interface... [edit protocols] user@R1# edit protocols rsvp interface interface-name [edit…
MPLS Protection and Restoration – Part 12 (Juniper Configuration Samples)
[edit] user@R1# edit protocols rsvp interface type-fpc/pic/port [edit] user@R1# edit protocols rsvp interface fe-1/1/1 To configure link protection for the interface... [edit protocols rsvp interface type-fpc/pic/port] user@R1# set link-protection To configure link protection for LSPs requiring use of the bypass path... [edit protocols rsvp interface…
MPLS Protection and Restoration – Part 11 (Juniper Configuration Samples)
One-to-one (fast reroute) backup Configuratio To enter edit mode... [edit] user@R1# edit protocols mpls To configure the LSP... [edit protocols mpls] user@R1# set label-switched-path lsp-path-name to address [edit protocols mpls] user@R1# set label-switched-path A-to-B to 1.1.1.1 To configure one-to-one(fast rerote) backup... [edit protocols mpls] user@R1#…
MPLS Protection and Restoration – Part 10 (Juniper Configuration Samples)
One-to-one (Fast Reroute) configuration on JuNOS [edit] protocols { mpls { label-switched-path lsp-path-name { fast-reroute; } } } Many-to-one (Facility Backup) Link protection configuration on JuNOS [edit] protocols { rsvp { interface type-fpc/pic/port { link-protection; } } mpls { label-switched-path lsp-path-name { link-protection; } }…
Global Mobile Data Traffic Forecast by Cisco (2014–2019)
In this post, you can find several important points about mobile data traffic growth between 2014 and 2019. This summary info will provide you a general view on mobile data traffic growth. The original document is released by Cisco with the name Global Mobile Data…
VLAN Mapping (VLAN Translation) on Juniper
On Juniper devices, VLAN translation term is used for mentioning the swap of incoming VLAN id to a new VLAN id. In the below configuration examples, we will configure VLAN Mapping on Juniper devices. You can also check Cisco VLAN Configuration on Packet Tracer…
VLAN Mapping (VLAN Translation) on Cisco
Virtual LANs (VLANs) are very important for a network. Sometimes network engineers need to map VLANs to VLANs. This is called VLAN Mapping. In other words, on Cisco devices, VLAN Mapping term is used for mentioning the swap of incoming VLAN id to a new…
VLAN Mapping (VLAN Translation)
In the different locations of the customer, the same VLAN tag means the same. But there is a service provider network between the customer locations. Customers and the Service Provider use different VLAN tags in their networks. So, here there must be VLAN mapping or…
PAT Configuration with Packet Tracer
Packet Tracer PAT Configuration Example In some cases there can be hundreds of inside local addresses and at the same time your Global IP Addresses can be limited. At this time you can use PAT instead of Static and Dynamic NAT translation. Here, we will…
Dynamic NAT Configuration with Packet Tracer
Packet Tracer Dynamic NAT Configuration Example Before this article, we have talked about Static NAT configuration. Here, we will talk about another types of NAT, Dynamic NAT configuration on Packet Tracer. As in Static NAT, in the Dynamic NAT, the interfaces must be identified as…
Static NAT Configuration with Packet Tracer
Packet Tracer Static NAT Configuration Example In this example we will configure Static NAT (Network Address Translation) on Packet Tracer. For our Static NAT configuration, we will use the topology below. You can DOWNLOAD the Cisco Packet Tracer example with .pkt format at the End…
NAT – Part 1 (Network Address Translation)
The increase of the internet users has consumed IPv4 addresses rapidly. And to continue with these addresses various techniques have used by organizations. One of them is Network Address Translation(NAT). As you know there are public and private addresses. The public addresses are used to…
SNMP – Part 4 (SNMP Configuration On Nokia Service Routers)
In the previous articles on SNMP Cofigurations, we have talked about Huawei, Juniper, Cisco SNMP Configurations. In this article, we will handle Nokia SNMP configuration on Nokia Routers. As you know, the main aim to use SNMP is the same. We use SNMP to manage…
Routing with OSPF - Part 7
In htis article, we will talked about the remainning main lessons of OSPF. These small but important lessons are : OSPF Router ID OSPF Virtual Links OSPF Authentication OSPF Timers Let's talk about these parts one by one. If you would like to learn…
Routing with OSPF – Part 6
OSPF Protocol can work in different network topologies. Some of these Network types are Standard and Some of them is Cisco Proprietary. Mainly,these networks types are given below: • Broadcast Networks (Cisco Proprietary) • Nonbroadcast Multi Access(NBMA) Networks • Point-to-Point Networks (Cisco Proprietary) • Point-to-Multipoint…
Routing with OSPF – Part 5 (OSPF Area Types)
What are the OSPF Area Types? OSPF uses an hierarchical architecture and build OSPF network with different Areas. There are many specific Area types that are used with OSPF and these Area types has specific characteristics. So, what are these areas? General OSPF Area types…
Routing with OSPF – Part 4 (OSPF LSA Types)
In OSPF Link-State information, in other words,Routing information is exchanged between routers. This exchange is done with LSAs (Link State Advertisements). There are eleven different LSA types and each of them has a special purpose. Some of the LSA types are the main LSA types…
Routing with OSPF – Part 3 (OSPF Packet Types)
OSPF use OSPF Packet sto communicate and establish OSPF Operation. There are different Packet types in OSPF and in this article, we will focus on these OSPF Packet Types. We will explaint each Packet and see the duty of this packet. In almost, every technical…
Routing with OSPF – Part 2 (OSPF Adjacency)
OSPF Adjacency States Routers establish OSPF adjacency to use OSPF. From the beginning of the establishment to the full adjacency, there are some states. These states are mentioned below: OSPF (Open Shortest Path First) Neighbourship States • Down • Init : Hello packet received without…
Routing with OSPF - Part 1
OSPFv2 Overview OSPF (Open Shortest Path First) is a Link-State Routing Protocol. It is also Classless and an Open, Standard Protocol used by all vendors. OSPF uses Dijsktra Algortihm, a Shortest Path First Algorithm (SPF) to determine the best path to a destination network. In…
TCP Header Part – 5
TCP Options The last part of this article series is related to TCP options. After this there is aleady the data part. In this section there are some options that enhance TCP protocol. This options are MSS, Window Scaling, Selective Acknowledgements, Timestamps and Nop.…
TCP Header Part – 4
TCP Window Size, Checksum & Urgent Pointer The window, checksum and urgent pointer are another important fields in TCP header. Each of these fields are 2 bytes long. Window Size Window size the most important part in the TCP header. This fields is used by…
Subnetting in IPv6
IPv6 Subnetting We have talk about IPv4 Subnetting in another lessons. In this lesson, we will focus on IPv6 Subnetting and how to use it with IPv6 Addresses. Subnetting is used in IPv4 to use the address spaces effectively. But IPv6 provide too much addresses.…
IPv6 Address Types
What Are The Types of IPv6 Addresses? IPv6 has some similar and some different address types than IPv4. There are still unicast addresses in IPv6 world but this time there will be one more Unicast address types. Still multicast addresses are being used but with…
What does IPv6 bring?
What are the IPv6 Benefits? The new IP Protocol, IPv6 Protocol comes with some new features beside it. These new features brings manay benefits together with IPv6. What are these IPv6 Benefits? In this lessons, we will focus on Features coming withh IPv6 and IPv6…
IPv6 and IPv6 Addresses
What is an IPv6 Address? IPv6 Address is the new generation IP address that is mainly deveoped to overcome IPv4 exhaust and its limitations. As you know, IPv4 Addresses were limited and exhaused shortly. For the new technologies, more IP addresess needed and for…
IPv6 Routing Protocols – Part 2 (OSPFv3)
OSPFv3 is a new version of OSPFv2 protocol that is developed for IPv6. The previous version, OSPFv4 was only used for IPv4. With the IPv6 revolution, routing protocols have also changed and new versions of routing protocols developed. OSPFv3 is one of the routing protocols…
IPv6 Routing Protocols
IPv4 and IPv6 Protocol Comparison Routing is a process that we route packets in a network as static or dynamic. Static routing is done manually and dynamic routing is done with the help of Routing Protocols. These routing protocols are RIP, EIGRP,OSPF,ISIS and BGP. We…
IPTV Overview– Part 2
We can divide the IPTV compontents into 5 parts. These parts are defined below: National Head-End : Origination point of network broadcasts for tranmisssion over the IP network. Core Network : Generally an IP/MPLS network that transports the traffic to the access network. Access Network…
IPTV Overview– Part 1
IPTV with its long name Internet Protocol Television is a television system that this service is delivered using the IP suite over a packet-switched network like internet. Traditionally, the television system is delivered through terrestrial , cable tv or satellite. But IPTV is different than…
Ethernet Collisions and Troubleshooting
In this article, we will focus on ethernet collisions and how to troubleshoot these common situations. Let’s start with, what is collision. In computer networking Collision is the situation that occurs while the two or more device try to use the shared medium at the…
IPv6 Static Routes (On Juniper Routers)
On Juniper routers to create a static route for IPv6 we use “routing-options” hierarchy as IPv4. But this time after this hierarchy, we go under another hierarchy, “ rib inet6.0”. The below example will be a basic example of configuring IPv6 static routes on Juniper…
IPv6 Static Routes (On Cisco Routers)
On Cisco routers to create a static route for IPv6, we use the similar commands with IPv4. We can make this configuration with three ways : 1) To send all packets to the next-hop address : ipv6 route 2001:dc8:b15:4::1/64 2001:dc8:b15:5::1/64 2) Directly attached static route…
VTP Configuration with Packet Tracer
Packet Tracer VTP Configuration In this article, we will focus on how to configure VTP, with Packet Tracer. For VTP Configuration, we will use the topology below with two switches and two PCs. VTP Example Topology You can DOWNLOAD the Packet Tracer example with…
VTP (VLAN Trunking Protocol)
What is VLAN Trunking Protocol? VTP (VLAN Trunking Protocol) is a Layer 2 Protocol that allows to control, create and delete VLANs from a central VTP Server. Cisco switches are in “vtp server mode” by default. In a large network there can be mant switches…
SNMP - Part 3 (Configuration On Juniper Junos)
We begin the SNMP configuration with Cisco devices and here, we will continue how to configure a Juniper device for SNMP. In this article we will not mention all the parameters deeply like in the before article. We will check the difference of Juniper JUNOS…
SNMP Configuration On Cisco IOS
In this Cisco SNMP Configuration Example, we will see how to configure SNMP on Cisco SNMP Agent device. In this part I do not consider necessary what the snmp agent is. You already know that it is the device that we consider to manage with…
Enabling MPLS On Cisco Routers
In this article, we will study how to enable CEF, how to enable MPLS and how to configure label protocol ldp on Cisco routers. During this survey we will check the configuretion with various basic show command that will be useful during MPLS configurations. After…
TCP Header Part – 3
Each TCP segment has a special purpose and this is determined by flags.Here we will study on 6 important control flags. There are also other options in flag field, but we will focus only 6 of them. You can check these flags below. The most…
TCP Header Part – 1
In this section, we will survey the TCP header in packets. As you know TCP is a layer 4 protocol and its header is also have parameters about layer 4. Before TCP header, packet has layer 3 header, it is IP in our example. And…
TCP Header Part – 2
Sequence & Acknowledgement Number Sequence and Acknowledgement fields are another important fields in TCP Header. Each of these TCP Header Fields are 32 bits long. Datas generally sent and received with packets larger than MTU. So using sequence and acknowledgement number getting important during this…
Default Routes and Floating Static Routes on Alcatel Routers
In this lesson we will talk about two different Static Route types. One of them is "Default Routes" and the other is "Floating Static Routes". Now, let's see what are they and why we use these different Static Routes. We will also see, how to…
Static Routing with Alcatel-Lucent Service Routers
Static Routing with Nokia (Alcatel-Lucent) Service Routers As you know Nokia is another network device vendor like Cisco and Juniper. Here, we will see the static route configuration with Nokia routers. For this configuration, we will use one of the routers in Nokia's Service…
SNMP Configuration on Cisco Routers
There are a number of commands can be used to configure SNMP on a Cisco device. Some of these commands are required although some are optional. The required ones are mentioned below: Router(config)# snmp-server community string [view view-name] [ro | rw] [number] Router(config)# snmp-server…
Basic Frame-Relay Configuration with both Inverse-ARP and Frame-Relay Map Command
Here, we will talk about two options for configuring Frame-Relay Maps. One is Inverse-ARP and the other is with “frame-relay map” command. To show this in a basic topology, we will use the below topology configured with three Cisco 3600 series routers. Firstly, we will…
Basic Multipoint Frame Relay Configuration
Here, in multipoint Frame-Relay configuration, we will use the same Cisco 3600 series routers and a frame relay switch. But here, our configuration will not be point-to-point only. Routers will be connecting to the routers as multipoint. We will start with Frame-Relay Switch again.Create a…
Basic Frame Relay Point-to-Point Configuration
AS you know Frame-Relay is a well-known WAN technology that generally used for backbone routers. To understand the basic configuration of Frame-Relay, there is a configuration below with three Cisco 3600 Series Router and one Frame-Relay Switch. First of all, we will start with Frame-Relay…
Static Route Configuration on Juniper Routers
In this article we will focus on static route configuration on Juniper routers. Here, we will use Juniper JuNOS and we will be familiar with some JuNOS commands. The basic topology that we will use is below. We have three routers and two network. We…
Evolution from 2G to LTE (Part 3 – EDGE)
Beyond GPRS, EDGE(Enhanced Data rates for GSM Evolution) takes the cellular community one step closer to UMTS. It provides higher data rates than GPRS and introduces a new modulation scheme called “8-PSK”. EDGE is also being adopted by the TDMA community for their migration to…
Evolution from 2G to LTE (Part 2 – GPRS)
The evolution had started with additional of the packet switched network to the GSM network architecture. And this new technology called GPRS(General Packet Radio Service). It is also called 2,5G. GPRS is important as a migration step toward third-generation (3G) networks and allows network operators…
Evolution from 2G to LTE (Part 1 – GSM)
The evolution of the 2G technology to LTE technology is in three types: Technical evolution : The new network elements are developed with new technology Network Evolution : General functionality of network will change Service Evolution : Demand generated by the end user will increase…
Router DHCP Configuration with Packet Tracer
In this DHCP Cisco Packet Tracer router example, we will focus on DHCP Configuration in Cisco Packet Tracer. In other words, we will see how to configure a DHCP Server with Packet Tracer Router. Before start up I want to give some basic information about…
Access Control Lists for Traffic Control
There are various ways for network traffic control. One of the common ways for this job is using Access Contorol Lists. There are three types of access lists. These are; • Router Access Control Lists( RACLs) • Port Access Control Lists (PACLs) • VLAN Access…
What is MPLS?
In this lesson, we will focus MPLS in Networking and we will learn the answer of what is MPLS? So, What is MPLS? MPLS is a Packet-Forwarding technology which uses MPLS Labels for data forwarding decisions. It is the abbreviation of Multi Protocol Label Switching. Over time, users in networks…
Initial Configuration for Juniper Routers
This article is telling about some of the initial configurations of Juniper Routers. Here are the steps that you will experience when you firstly start the Juniper CLI Junos. 1) The first thing you will see is the default user name “Amnesiac” on the screen.…
IPv4 and IPv6 Headers
IPv4 Header versus IPv6 Header IPv4 and IPv6 are the two man version of Internet Protocol, IP. Both IPv4 and IPv6 has Headers and these headers are a little different. After IPv4 Header, IPv6 Header has designe to be simpler and more efficient even…
Cisco Single Area OSPF Configuration
OSPF Cisco Configuration OSPF (Open Shortest Path First) protocol is a well-known routing protocol that is widely used today. To configure a network for OSPF properly there are some steps. For basic OSPF Cisco Configuration, the following scenario will be a good example. …
Static Route Configuration on Cisco Routers
Cisco Static Route Configuration To send the traffic to the destination we can use two types of routing. Static and Dynamic routing. Static route tell the network devices about exact location.Beside, static routers can work well with small networks. For large scale networks dynamic routing…
Cisco Router Password Recovery
How to Password Recovery on Cisco Routers? There are several reasons to recover a router’s enable password. For example you can forget the password or somebody might give a password that you don’t know. So, to reach your router's or switch's command line interface, you…
EtherChannel Configuration
Etherchannel Configuration Layer 3 Etherchannel with PAgP Spanning-Tree blocks redundant links and avoid Layer 2 loops. Etherchannels load balance the traffic between the redundant links and uses the bandwidth more efficient. Sp, how can we configure etherchannel? To understand more clear, here is a basic…
IP (Internet Protocol)
IP is the primary netwok protocol that used for relaying packets across an internetwork. It is developed in the 1970s. In the network world it is commonly used with TCP(Transmission Control Protocol) as TCP/IP... Internet Protocol supports unique addresses for network devices. The previous version…